Nachdem ich das Video gesehen hab, hab ich endlich das Problem mit der neuen #eIDAS Verordnung in der #EU verstanden.
https://www.youtube.com/watch?v=lAuFuW1FiQY
#Privatsphäre #Piraten #Deutsch
Tips for Signal
Signal is flawed in that it’s centralized on Amazon servers, requires a phone number, and can not be self-hosted. However regular SMS is so horrible, and Signal is so intuitive for new users, that telling people not to use it likely does more harm to privacy than good. So here are some tips to improve:
1) Turn off read receipts
Signal has a system called “Sealed Sender” to hide metadata, but it’s flawed. It works by putting the metadata of who sent the message inside the encrypted packets. However, cybersecurity researchers from the University of Colorado Boulder, Boston University, George Washington University, and U.S. Naval Academy, found that Sealed Sender could be compromised by a malicious cloud host in as few as 5 messages to reveal who is communicating with who. In this paper published by NDSS, headed by Ian Martiny, these researchers found that Signal’s “read receipts”, which lets the sender know that the receiver got the message, can be used as an attack vector to analyze traffic. This is because read receipts send data packets right back to the sender.
Source:
https://www.ndss-symposium.org/wp-content/uploads/ndss2021_1C-4_24180_paper.pdf
Therefore, our recommendation to increase metadata protection is turn off read receipts, which can be toggled in the security settings.
2) Don’t use an American phone number
In an earlier post on burner numbers, we talked about burner crypto text services, such as virtualsim.net which allow you to pay a tiny bit of crypto for a 1 time SMS code. If you can be anywhere in the world, why would you pick a jurisdiction that’s hostile to privacy? You can reach us on our Cambodian line! Remember that spacing matters on Signal. It’s counting +4 4 and +44 as different countries.
3) Use Signal only for people you know
Signal has poor metadata protection because your real life friends likely don’t have DeGoogled phones, so they’ll save your burner Cambodian line as your real name in their contact list, and then their contact list syncs with Google or iCloud and your anonymity is blown.
So if you want to hide that you’re even talking to someone, then use SimpleX, Session, XMPP, or one of the many other options.
4) You can have multiple profiles with different numbers
With Graphene you can have different user profiles with new numbers, or even within the same user profile on a Work one. If you use a 2nd Work Profile number, just remember that the Amazon server can see two numbers pinging for messages from the same IP, so set your VPN to the largest city you can to disguise and don’t change cities/countries on both accounts at the same time. You could use numbers from different countries to throw them off too, but at the end of the day, Amazon would probably see that your Cambodian and Ohio identities both wake up at the exact same time every day.
If you really want anonymity, check out our SimpleX self-host script we made for you on our website.
How about using this fork?
Just finished watching the first season of Succession and it's already one of my favorite TV shows.
The series is just brilliant and such a good illustration of everything that's going wrong in the fiat world!
#Bitcoin #FIAT #TV #series
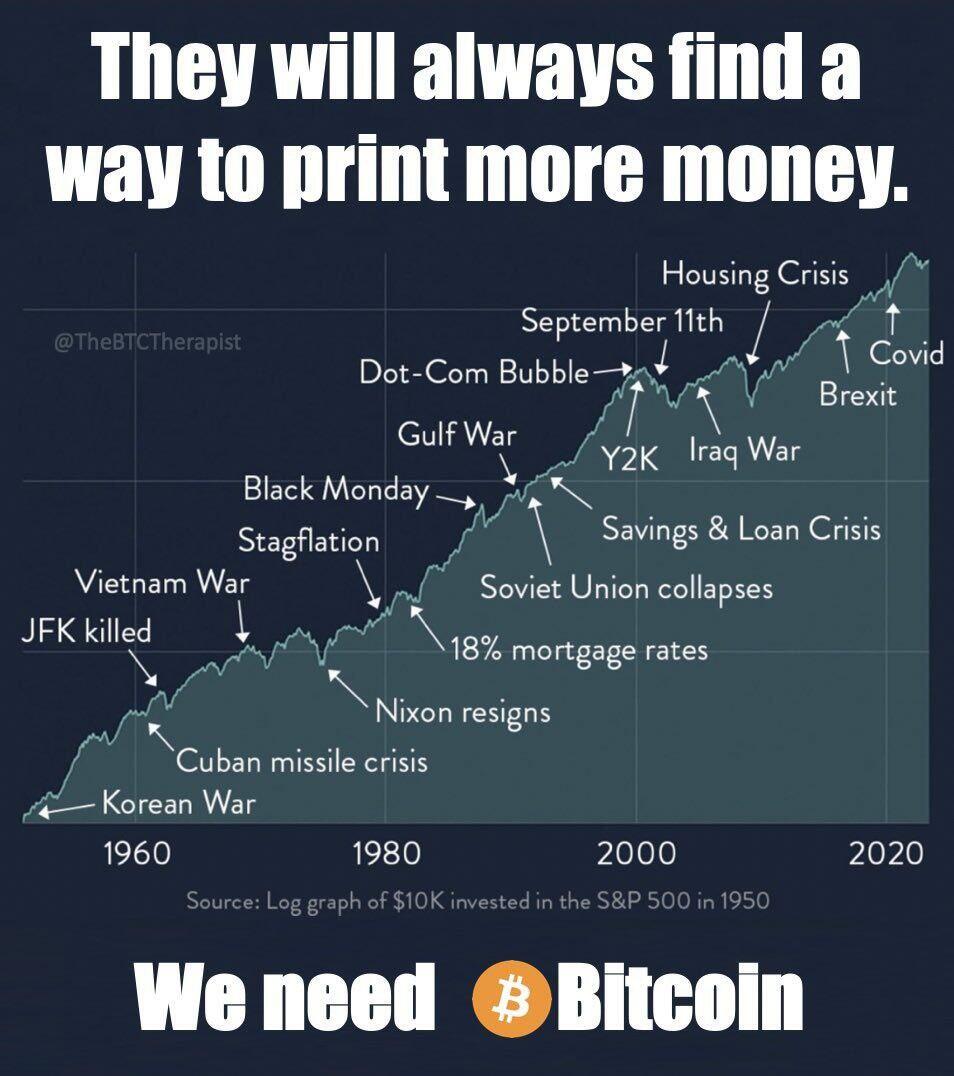
Das einzig interessante an der Grafik ist, wie stabil der Yen in der Vergangenheit war! Und das obwohl die japanische Notenbank mit Abstand das meiste Geld gedruckt hat. Ich denke Maurice würde wohl eher lachen als weinen 😉
Zwei deutsche Hochschulprofessoren kritisieren die Geldpolitik und reden positiv über Bitcoin. Sowas hat es früher nicht gegeben, wir sind echt weit gekommen!
#Bitcoin #Einundzwanzig #Deutsch #Podcast
Sehenswerte Sendung zum organisierten Anlagebetrug. Falls ihr schon immer wissen wolltet wer euch da ungefragt anruft und Krypto-Investments andrehen will
https://www.youtube.com/watch?v=Z1FR4JIo1Mk
#Deutsch #Bitcoin #scam
Auch spannend!
Sehenswerte Sendung zum organisierten Anlagebetrug. Falls ihr schon immer wissen wolltet wer euch da ungefragt anruft und Krypto-Investments andrehen will
https://www.youtube.com/watch?v=Z1FR4JIo1Mk
#Deutsch #Bitcoin #scam
Die SEC hat noch keinen Bitcoin ETF genehmigt, da sie Angst vor einer 51%-Attacke haben, durch #MarkusSeiMudda!
#Einundzwanzig #Deutsch
Die Node von #MarkusSeiMudda ist so fett, ihr eigener Sohn kann sich keinen Channel zu ihr leisten.
#einundzwanzig #lightning
#MarkusSeiMudda stackt mehr Sats als Michael Saylor, und das allein durchs Routing.
#einundzwanzig #lightning
Blocktrainer Bitcoin Podcast
Wochenrückblick #43 mit nostr:npub1pzcj8yfs3kx2thtjpz3agr2w54m52kv9a2933smqyt6n6k2ql3aq2d0wlx Schwachstelle bei Lightning, Fake ETF-News, CBDC Dystopie

Ich hab irgendwie immer das Gefühl ihr besprecht die News von vorletzter Woche. Klappt es nicht etwas aktueller?
Just paid my VPN using lightning. Wow, what a great experience!
You can buy a voucher for mullvad.net and redeem it in 10 seconds using this service:
https://vpn.sovereign.engineering/
#lightning #vpn #mullvad #spendl
Wenn du eine Hardware Wallet besitzt, musst du diesen Vortrag gesehen haben!
https://www.youtube.com/watch?v=sv6rRvbAo1Q&t=0
#Bitcoin #Deutsch #German #Einundzwanzig
Amerikanische Tech-Firmen wollen scheinbar die Chatkontrolle in der EU durchsetzen.
Wer ist schuld dran wenn es klappt, die Lobby oder die Politik?
#Deutsch #EU #Privacy #Einundzwanzig
Great report on the currency crisis in Argentina!
https://www.npr.org/2023/09/22/1197954122/argentina-peso-inflation-milei
#Bitcoin
#Argentina
#Bitcoinfixesthis