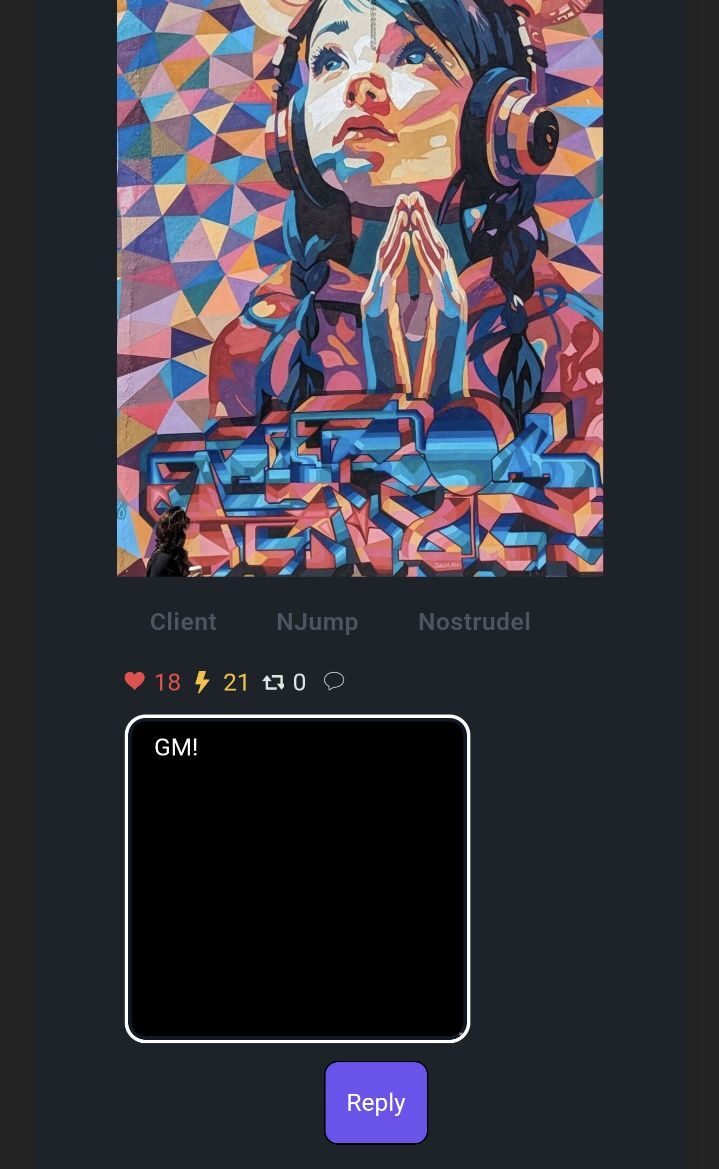
It's the most bizzare shit I hear all the time.
Pretty cool!
True. Skill almost completely erased from societies.
I am. Who plays the music? The host?
SALUTE THE CYPHERPUNK OGs✊🏼.
nostr:note168s5rkg6aj44m97403va0j2dsjq6als94w79qa9gu5savuvpaqvsm44gf3
NO TITLE #838876
#notitle 
Another banger by Vahan!
He was always the biggest advocate of my noise work...always pushing me to go deeper into the experimental audio field...he convinced me and #JustinChancellor to incorporate noise textures in #mtvoid music.
Respect.
nostr:note1xlse07xsqpgmz88fw7qgs5sjq77gz8m9du8u6aj32lyadaqt2yysgysqj8
GHOST - NOISE INC.
Will be my next audio release on nostr:npub1yfg0d955c2jrj2080ew7pa4xrtj7x7s7umt28wh0zurwmxgpyj9shwv6vg
Dropping tomorrow.
You can check my #noise content here :
This track is My Codename...what is yours?
Noise Inc. project was and still is my field for different type of audio/visual experimentation.
It goes from extreme harsh noise to cyber punk. I explore deep soundscapes and minimal structures.
A lot more #noisemusic is coming.
#glitch #artstr nostr:npub1yfg0d955c2jrj2080ew7pa4xrtj7x7s7umt28wh0zurwmxgpyj9shwv6vg
https://wavlake.com/track/9e2724cd-3a0c-4e61-9f41-7c1651ff4ba5 
Best part about #nostr is being close to great minds, authors, creators, devs, deep thinkers, innovators and with a bit of social skills and being nice you can talk directly to these awesome humans! This creates the dynamics and exponential growth curve of our times. I personally never take it for granted and I'm always grateful for this amazing connections. #relaythat #knwoledge #privacy #security
Thanks for taking time to give this in depth answer. For general purpose I use Proton and Tutanota on daily. Skiff was cool until it wasn't so also good because we need those red flags 🚩 to not feel too comfortable. Security and privacy in today's wrld is a serious job and study.
ARTISTS REVOLT AGAINST SOCIAL MEDIA
--- Deep Questions podcast 295 with Cal Newport
I’m a fan of Cal Newport and the content he creates. It’s mostly about how to keep your (digital) distractions under control by using different deep-work methods. It’s basicly a way of living by making your day a good day.
Link to view the podcast: https://piped.r4fo.com/watch?v=KcQMt9HabqA The part I would like to highlight is discussed in the first 37 minutes.
"In this episode Cal takes a closer look at a growing trend of artists quitting social media and instead reverting to old fashioned websites. Are these acts of principled sacrifice or a sustainable way to be creative online? Cal argues for the latter, showing how the internet without social media curation algorithms can be a place of rich discovery and audience building. He then takes questions on similar topics and ends by playing a few rounds of “deep or crazy” during the final segment."
Some video’s which are part of this revolt:
- Deleting social media and making a website: https://piped.r4fo.com/watch?v=tV6BbPTN5PQ
- Why I don’t post anymore: https://piped.r4fo.com/watch?v=W3h9gV_z8OM&t=0
- I deleted all my social media and made a website: https://piped.r4fo.com/watch?v=r0RqucKwIcw
Let me try to summarize some important parts of Cal his analysis.
What are the main reasons why artists are stopping with social media?
1. Social media is controlling and reducing the quality of their art
2. The algorithms are rewarding sameness and not uniqueness
3. Social media is making them unhappy
4. They didn’t get into social media for social validation
Cal dives shortly into the history of the internet and the discoverability challenges / problems with the web (networks of networks of networks). He also is mentioning the value of serendipity discovery mechanisms.
👀 At 16m45s Cal is discussing and drawing the concept of a distributed trust model, this is where the nostreness kicks in! 👀
This is a clip from 22m28 till 23m22s of the podcast:
https://shares.sebastix.dev/mYIzuTLC.mp4
Link to the show and all notes: https://www.thedeeplife.com/podcasts/episodes/ep-295-artists-revolt-against-social-media/
#growNostr #OpenWeb #GoodbyeBigTech #communities #enshitification
#nostr changes that I believe.
Thx. Gotta implement that.
Key I get...what is nostrlogin ? Is it via out verifiers?
Interesting. To be honest...I was big into privacy email/storage/encryption providers. People who are serious about privacy told me that they are a possible trap...and boom skiff went out of bussiness...so those all in one formulas are always risky. What do you think?
I am so deep into ios and mac osx systems that the moment I make the switch will be a big one for me. Made some steps already.
Hey :) do you log in into noogle.lol ?
It is. That's another reason why I highly recommend #GrapheneOS + silent.link esim.
#GrapheneOS helps mitigate against baseband attacks. This is going to be a long reply, but it's worth reading :)
TL;DR
GrapheneOS deploys a multi-layered approach to defend against baseband attacks, including isolation, encryption, and overall system hardening. This helps mitigate the risks posed by potential vulnerabilities in the cellular baseband.
"Is the baseband isolated?
Yes, the baseband is isolated on all of the officially supported devices. Memory access is partitioned by the IOMMU and limited to internal memory and memory shared by the driver implementations. The baseband on the officially supported devices with a Qualcomm SoC implements Wi-Fi and Bluetooth as internal sandboxed processes rather than having a separate baseband for those like earlier devices.
Earlier generation devices we used to support prior to Pixels had Wi-Fi + Bluetooth implemented on a separate SoC. This was not properly contained by the stock OS and we put substantial work into addressing that problem. However, that work has been obsoleted now that Wi-Fi and Bluetooth are provided by the SoC on the officially supported devices.
A component being on a separate chip is orthogonal to whether it's isolated. In order to be isolated, the drivers need to treat it as untrusted. If it has DMA access, that needs to be contained via IOMMU and the driver needs to treat the shared memory as untrusted, as it would do with data received another way. There's a lot of attack surface between the baseband and the kernel/userspace software stack connected to it. OS security is very relevant to containing hardware components including the radios and the vast majority of the attack surface is in software. The OS relies upon the hardware and firmware to be able to contain components but ends up being primarily responsible for it due to control over the configuration of shared memory and the complexity of the interface and the OS side implementation.
The mobile Atheros Wi-Fi driver/firmware is primarily a SoftMAC implementation with the vast majority of the complexity in the driver rather than the firmware. The fully functional driver is massive and the firmware is quite small. Unfortunately, since the Linux kernel is monolithic and has no internal security boundaries, the attack surface is problematic and a HardMAC implementation with most complexity in the isolated firmware could be better than the status quo. An isolated driver would be ideal."
https://grapheneos.org/faq#baseband-isolation
"Does GrapheneOS offer protection against evil backdoor basebands?"
GrapheneOS only elects to support devices that offer the best modem and radio isolation via IOMMU mitigations and policies. IOMMU only allows a device attached to the host memory by direct memory access to read or write to memory values that the driver in the kernel specifically allows it to, and only elects to support devices that have open source drivers which are readily supported by their vendors and updated frequently.
The firmware for the radios and modems is not state-carrying. GrapheneOS will load the firmware binaries when the operating system boots. Prior to this, the system image (which contains the firmware binaries) will be verified via Android Verified Boot which is keyed to Daniel Micay's signing keys. Should any of the firmware be exploited, it is already limited from the host memory via IOMMU, and rebooting it will restore it to a known good state.
"What does GrapheneOS do about cellular tracking, interception and silent SMS?
GrapheneOS always considers networks to be hostile and avoids placing trust in them. It leaves out various carrier apps included in the stock OS granting carriers varying levels of administrative access beyond standard carrier configuration. GrapheneOS also avoids trust in the cellular network in other ways including providing a secure network time update implementation rather than trusting the cellular network for this. Time is sensitive and can be used to bypass security checks depending on certificate / key expiry.
Cellular networks use inherently insecure protocols and have many trusted parties. Even if interception of the connection or some other man-in-the-middle attack along the network is not currently occurring, the network is still untrustworthy and information should not be sent unencrypted.
Authenticated transport encryption such as HTTPS for web sites avoids trusting the cellular network. End-to-end encrypted protocols such as the Signal messaging protocol also avoid trusting the servers. GrapheneOS uses authenticated encryption with modern protocols, forward secrecy and strong cipher configurations for our services. We only recommend apps taking a decent approach in this area.
Legacy calls and texts should be avoided as they're not secure and trust the carrier / network along with having weak security against other parties. Trying to detect some forms of interception rather than dealing with the root of the problem (unencrypted communications / data transfer) would be foolish and doomed to failure.
GrapheneOS does not add gimmicks without a proper threat model and rationale. We won't include flawed heuristics to guess when the cellular network should be trusted. These kinds of features provide a false sense of security and encourage unwarranted trust in cellular protocols and carrier networks as the default. These also trigger false positives causing unnecessary concern and panic. The correct approach is avoiding trusting the network as explained above.
Connecting to your carrier's network inherently depends on you identifying yourself to it and anyone able to obtain administrative access. Activating airplane mode will fully disable the cellular radio transmit and receive capabilities, which will prevent your phone from being reached from the cellular network and stop your carrier (and anyone impersonating them to you) from tracking the device via the cellular radio. The baseband implements other functionality such as Wi-Fi and GPS functionality, but each of these components is separately sandboxed on the baseband and independent of each other. Enabling airplane mode disables the cellular radio, but Wi-Fi can be re-enabled and used without activating the cellular radio again. This allows using the device as a Wi-Fi only device.
The LTE-only mode added by GrapheneOS is solely intended for attack surface reduction. It should not be mistaken as a way to make the cellular network into something that can be trusted.
Receiving a silent SMS is not a good indicator of being targeted by your cell carrier, police or government because anyone on the cell network can send them including yourself. Cellular triangulation will happen regardless of whether or not SMS texts are being sent or received by the phone. Even if an SMS did serve a useful purpose for tracking, a silent SMS would be little different than receiving unsolicited spam. In fact, sending spam would be stealthier since it wouldn't trigger alerts for silent SMS but rather would be ignored with the rest of the spam. Regardless, sending texts or other data is not required or particularly useful to track devices connected to a network for an adversary with the appropriate access.
Airplane mode is the only way to avoid the cellular network tracking your device and works correctly on the devices we support."
Thanks a lot! So the bottom line is that GrapheneOS does give some protection against this second layer system running in the background.
It might be location based mine says 49$ gotta change location ;)