100% this - nostr:nprofile1qqsrmhh22fcqncju3rf5yyhhex4rvdz0hm4a9d56qnh80l7rcrhhxugpr9mhxue69uhkummnw3ezuun4vf3x2unydakxctnrvvqs6amnwvaz7tmwdaejumr0dsq3yamnwvaz7tmsw4e8qmr9wpskwtn9wv4tz7j4 you're sharing good content, let people say thanks, get a Ln address up there - also you'd reach more people using hashtags imo.
Thanks Matt, done
Self sovereign zaps are back ⚡️
Thanks for the push!

nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch or nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv are my current top recommendations. You get a lightning address and they handle all the backend work. They are custodial, but you can easily move the funds to a wallet or address you control. There are trade off for everything.
Self sovereign zaps now setup ⚡️
It does seem that way!
Yep this one blew up. That’s interesting!
A dream come true to meet #btc OG nostr:npub1qg8j6gdwpxlntlxlkew7eu283wzx7hmj32esch42hntdpqdgrslqv024kw and perform close up! ♠️🎩🪄🧙🏾♂️✌🏽
nostr:npub167n5w6cj2wseqtmk26zllc7n28uv9c4vw28k2kht206vnghe5a7stgzu3r
Awesome
The algorithm could just be
Show me the most liked / zapped post from each person I follow in the past 24h, then show me the rest sorted by most liked / zapped
The void shouted back 🌍 ... here's what it said
⚡ I SHOULD ENABLE LIGHTNING
One overwhelming response was I need to enable lightning. I did have a self custodial LN setup with zaps once, but my channel partners closed on me and I haven't found new peers. I'm not using a custodial solution so my options are probably to find someone willing to peer and/or use an LSP.
👥 I AM THE ALGORITHM
Many people told me that I am the algorithm and that if I want to been seen I need to be very active interacting with people such that they interact back. My humble opinion is that this is not actually addressing the issue. Primal is great, and like most nostr clients I have used it has a few feed options ("algorithms").
- Latest
- Latest with replies
- Trending 24H
- Most Zapped
- Nostr Highlights
- Hashtags
This means that 5 of the 6 options are either content which already has lots of engagement or content which has just been posted.
I think what's missing is a more sophisticated algorithm which takes into account how many posts someone has made. If you follow bob and alice and bob makes 100 posts a day and alice makes 1, you probably don't want to use any of the existing algorithms, you probably want to see that 1 post by alice, even if it doesn't have any engagement yet, you follow her for a reason (presumably)
nostr:note18z3z5dq6f5ttd5a4vfzwm94cefladwq759hqfg773tr2q9xhxwys4utryq
I don't care about huge engagement, just some to know that it's worth posting haha
nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch or nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv are my current top recommendations. You get a lightning address and they handle all the backend work. They are custodial, but you can easily move the funds to a wallet or address you control. There are trade off for everything.
Thanks - I want to do it the sovereign way
I wasn't using an LSP, just one sided channels opened from my side
I've been posting on and off on nostr for quite some time and have 500 followers, many of whom like the content I post on X but not the same content when posted here.
I think it's the lack of algorithms which means you either see content which already has lots of views (if sorting by popular) or content which has just been posted (if sorting by recent posts).
Thank you for taking the time to write a thoughtful reply.
I had self custodial zaps set up way back. My LN channels were closed on me and haven’t found a good peer to set up again with.
Any suggestions?
I had self custodial zaps set up, LN channels were closed on me and haven’t found a good peer to set up again with. Any suggestions?
I want to use nostr more but it feels like I am shouting into the void, probably a skill issue
How about an onboarding option to disable the wallet, which remains hidden unless reactivated in settings @miljan ?
What is the nonce key exfiltration attack?
When signing a bitcoin transaction a number is used to generate the signature, this number is used once, and is therefore called the nonce.
This should be a cryptographically secure random number, which is never reused.
Suppose an attacker compromises your signing device, and can get it to use a particular nonce, rather than a random number.
If they use part of your private key as the nonce, they can leak part of your private key out of your signing device with each transaction you sign and broadcast.
If you make enough transactions, they can reconstruct your whole private key, and steal your bitcoin, just by watching the bitcoin transactions being made and decoding each part of the private key.
They don't need to compromise your computer, or physically access your device, and all the while your signing device appears to be working correctly, up until all your bitcoin is stolen.
There have recently been two new papers expanding on this attack.
- Dark Skippy by Lloyd Fournier, Nick Farrow of FrostsnapTech and Robin Linus of ZeroSync and BitVM.
- Engineering a backdoored bitcoin wallet by Adam Scott and Sean Andersen at block
I think it's great that these researchers have raised attention to this previously known attack vector.
Now, there are two types of reaction in my x feed on this issue, panic and ambivalence.
⚠️ Reaction 1 - Panicked
Nonce key exfil would enable theft at a distance, on all devices that update to malicious firmware & make 12 transactions. The attack doesn't require compromising the online device the signer talks to. The attack is not mitigated on most signing devices, and therefore large amounts of bitcoin are potentially vulnerable. The attack would be undetectable until the thieving begins
🤷♂️ Reaction 2 - Ambivalent
This attack requires getting malicious firmware onto a device. Competent signing device firmware devs secure firmware signing key(s) appropriately. Provided the firmware signing keys are not compromised this attack is mitigated because most signing devices check new firmware signatures before upgrading. Malicious firmware would enable many other attacks like generation of compromised wallets or exfiltration of keys in other ways (via screen, microSD or USB).
I think both Panic and Ambivalence are extreme.
❌ Panicked - Most hardware wallets verify firmware signatures so this attack requires either malicious firmware or a compromised firmware signing key / build pipeline and for many transactions to be signed with that firmware. Anti-klepto requires the online wallet to participate and adoption is limited. Creating panic leads uninformed users to rush to move their bitcoin to a new setup and this is when mistakes happen.
❌ Ambivalent - This attack is particularly nefarious because it can be done at a distance without needing to compromise any other user devices which makes it very scalable. If any firmware release is compromised all devices that run that version will be compromised. How secure is your signing key? How secure is your build pipeline? If anti-klepto was widely supported you would probably use it, so let's get it widely supported.
💡 Constructive - Focus effort into adding anti-klepto to a new version of PSBT instead of taking shots at each other or dismissing concerns.
Using the public nostr:npub18d4r6wanxkyrdfjdrjqzj2ukua5cas669ew2g5w7lf4a8te7awzqey6lt3 accelerator API you can now fetch a lightning invoice to boost any transaction.
Integrate into your app / service today.
A very limited batch of the display stand I designed for nostr:npub1s0vtkgej33n7ec4d7ycxmwt78up8hpfa30d0yfksrshq7t82mchqynpq6j Passport is available for purchase at BTC2024 in Nashville for $20.
Pick one up at booth 211. If you are not at the event and want to get your hands on one register your interest at the link below or send me a message.
https://tips.orange.surf/apps/37e8jKpHw5g7fmS5csD5bBLeg53r/pos

We just published the first mempool research report
📜 The Empty Block Report 📜
Welcome to the 5th Epoch 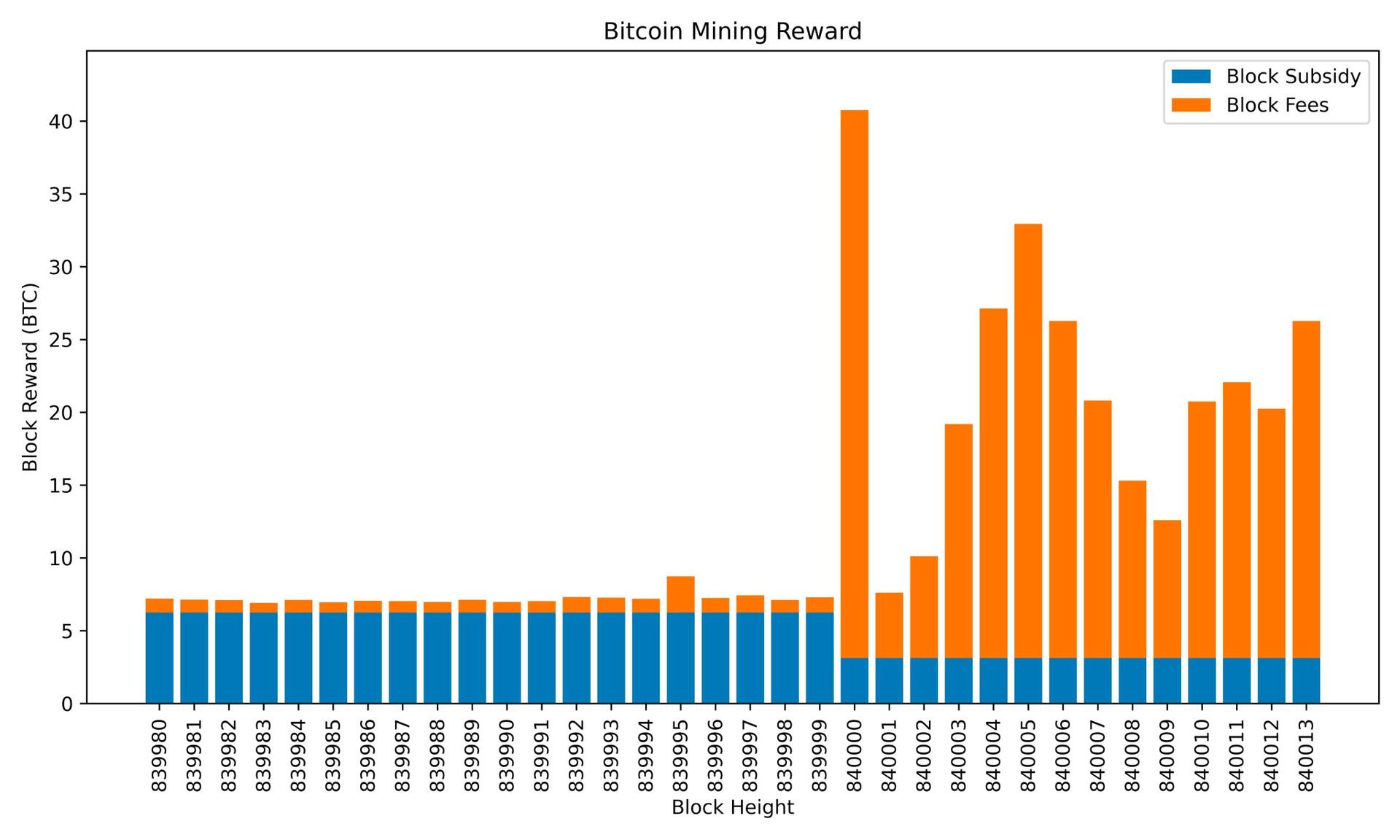
Full video https://www.youtube.com/watch?v=Zrv1EDIqHkY
big prime energy
I enjoyed this chat. It had something for everyone.
262,800 blocks

