Moq, a super popular NuGet package, included a dependency that harvested email addresses from the git.config files of all Moq users.
The behavior was removed, but by that point, it collected quite the data.
You don't need to have malicious/shady bejavior up for months... a few days in a super-popular library and the damage is done.
A Russian court convicted a hacker for developing malware and stealing card data from foreigners.
He also donated to Navalny's Anti-Corruption Fund.
We all know why he was convicted. Too bad Russia doesn't prosecute all the other hackers that didn't donate to Navalny.
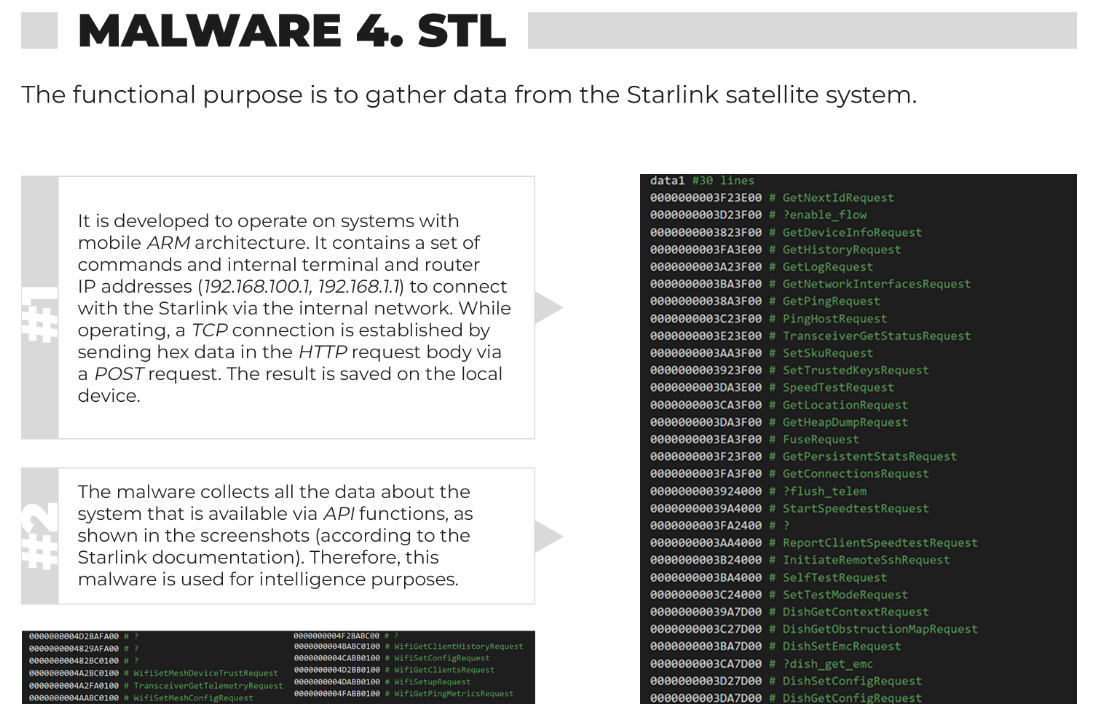
"The SBU cyber experts blocked attempts of russia’s military intelligence to gain access to the combat data exchange system of the Armed Forces of Ukraine."
"The SBU identified nearly 10 malware samples designed to extract information from the system."
SBU links the operation to Sandworm
Ok... it's live: https://rawcdn.githack.com/campuscodi/Microsoft-Patch-Tuesday-Security-Reports/3fc0327d05d51fd8bebb42df1d41a1e5fa648945/Reports/MSRC_CVEs2023-Aug.html
-87 patches
-1 zero-day (CVE-2023-38180)

New super clever side-channel attack dropped....
"As in the movie of the same name, Inception plants an “idea” in the CPU while it is in a sense “dreaming”, to make it take wrong actions based on supposedly self conceived experiences. Using this approach, Inception hijacks the transient control-flow of return instructions on all AMD Zen CPUs."
Patch Tuesday updates are late? 🤨
Interpol takes down 16Shop phishing-as-a-service platform
Image via ZeroFox: https://www.zerofox.com/blog/16shop-cash-app-phishing-kit/
BlueSky is not it... how do I go from +33 to -92 just by adding a link to my post... smh
"RedHotel's infrastructure for malware command-and-control, reconnaissance, and exploitation points to administration in Chengdu, China. Its methods align with other contractor groups linked to China's Ministry of State Security (MSS), indicating a nexus of cyber talent and operations in Chengdu."

lol but true

nostr:npub1zh3tctfxy433qlpqwnakrrx5fw6jyfcmq6kq6zfmrns7xqltdntqys8rtv
Not 2021. They're still in there, as of June 2023: https://www.nisc.go.jp/news/20230804.html
Newsletter: https://riskybiznews.substack.com/p/russian-bill-hide-military-police-pii-data
Podcast: https://risky.biz/RBNEWS182/
-Russian bill to hide the PII data of military, police, and intelligence agents
-Bitfinex 2016 hacker finally uncovered
-Rransomware attack cripples hospitals across five US states
-LetMeSpy shuts down after hack
-Japan's cybersecurity agency impacted in Barracuda hacks
-CISA calls for better UEFI security practices
-Bitter APT=Mysterious Elephant APT
-Major Points.com vulnerabilities
-Python libs get silent security updates

Also:
-Colorado Dept of Education suffers massive hack
-ChromeOS to split browser from OS
-Shin Bet warns of Iranian phishing
-Separate telco for RU state employees
-CISA publishes Cybersecurity Strategic Plan
-Nigerian BEC scammer pleads guilty
-FBI's NFT warning (translation: stop flooding IC3 with "my apes gone" complaints)
-Adware on the Play Store
-New npm and PyPI malware
-Malware reports on HUI Loader, Batloader, XORDDOS, PhantomControl, MerlinAgent
-Incognito Chain vulnerability

Newsletter: https://riskybiznews.substack.com/p/russian-bill-hide-military-police-pii-data
Podcast: https://risky.biz/RBNEWS182/
-Russian bill to hide the PII data of military, police, and intelligence agents
-Bitfinex 2016 hacker finally uncovered
-Rransomware attack cripples hospitals across five US states
-LetMeSpy shuts down after hack
-Japan's cybersecurity agency impacted in Barracuda hacks
-CISA calls for better UEFI security practices
-Bitter APT=Mysterious Elephant APT
-Major Points.com vulnerabilities
-Python libs get silent security updates

ACE Responder has released a tool named RogueSliver that can disrupt malware or red-team operations that use the Sliver C2 framework.
It can hijack beacons, send memes to the attacker, or flood and crash C2 servers.
https://github.com/ACE-Responder/RogueSliver
