Time to look into Bitcoin carnivore thing.
I'm sure it's satire but it's indeed not obvious enough, so it doesn't work that well.
I want Open Source smart appliances that just work.
I was thinking and I've found a pretty good steelman regarding geoengineering: the sprayed chemicals are not visible by naked eye and the white stuff is just water condensation.
Then possibly some government agency invented and spread the idea that the white stuff is the chemicals to make whistleblowers look absolutely ridiculous.
Also the idea that the chemicals are sprayed from commercial airplanes. They are not because the staff would definitely notice.
Yep, this specific idea was just funny thought, not a serious attack.
We should really help him backup his content using Nostr, though I don't think nostr is great at handling large files.
It is because it's crypto money. Currency is issued by government, money emerges in the market.
Sadly "crypto" no longer means "cryptography". It sucks and I hate it but it's the reality. 🤷♂️ Language evolves.
Yes, that too. You can use Rpis pin to transmit FM radio for instance. Which gives me crazy idea: if you transmitted a fake ad "call
You don't if you use several hardware wallets you own.
My point was I’m not sure you can pretend you’re *any* devices without being an Apple device. In any case nostr:nevent1qqsqac7czr2hk05gkf0l5s59tg3tz8xyspn9ea7aqxrvg9pswev8y8spzfmhxue69uhk7enxvd5xz6tw9ec82cspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qglwaehxw309ahx7um5wgkhyetvv9ujucnfw33k76tw9ehxjmn2vy728fpa
They have cheap BLE tags. If those cannot be reverse-engineered maybe you can record their beacons without the reach of any other device and then just replay them. Buying 256 tags may be worth it if the victim stores tens of millions satoshis.
I'd be really surprised if there isn't any way to sneak out 256 bits of data. Or less if the attacker wants to do some brute forcing.
Even without it, there are other similar networks which relay information.
The attacker could pretend it's 256 devices and transmit the seed by simply sending or not sending a message. It's not that high number.
I don't know how small GSM is today but I know that ten years ago the smallest widely available wifi module was around 100 times larger and 10 times costlier than today. So it migh become feasible in the future. There are other radio communication protocols as well.
Ever heard of GSM?
If that happens you're screwed anyway. A compromised HWW might as well contain a radio transmitter.
We need better tamper-proof seals.
You're exaggerating. Every competent hww checks firmware signature. Something an average joe can't do kn their laptop.
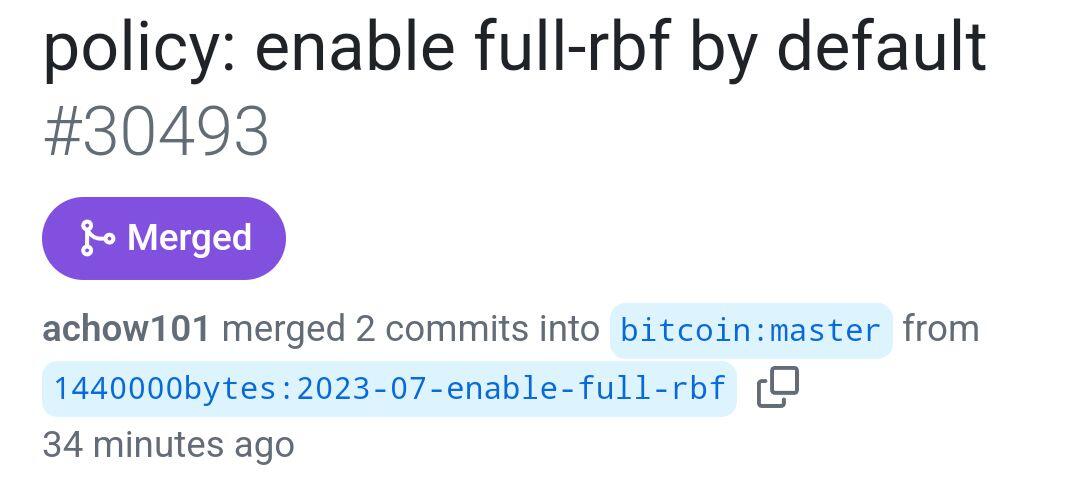
It took me 11 years. But I finally got full-RBF into Bitcoin Core.
https://github.com/bitcoin/bitcoin/pull/30493#event-13769240409
rbfr in another 11 years? 😃
What a fucking looser country 😮💨 unfortunately I live in it.. what is it thqt nostr:nprofile1qqs2xs05tluhtr6hpgsmqqxp04898gayjlyrjlexcrndv8j6el784xqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uq42ldx says => Everyone understand bitcoin when the need to understand it.
These fucking socialists (the politicians) doesnt need to yet...
Actually they're doing Bitcoin a favor.
