Not made in Russia!!!

I made one of these

I don't know what the numbers behind Unix command names mean
Guys we know it you don't like apple but please I don't care how little you care that you had to watch it live to properly express your completely non-caring attitude in a timely manner.
lesbians smh

The dividing line between millenials and gen x is finding minions funny
I think this model is a bit too tuned for ERP.
"Yeah so this is Mari, she's the new girl in the evangelion movies, I know you're from the Rei vs Asuka generation but she's pretty good too"

PLEROMA ADMINS READ THIS, AKKOMA TOO
Another important pleroma security post: nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6 and nostr:npub108zt8c43ulvdwnax2txurhhr07wdprl0msf608udz9rvpd5l68ascvdkr5 found ANOTHER injection bug, and this one was probably used for the attack. I think that single user instances are probably not affected, but I wouldn't want to risk it. Move your media and proxy to a subdomain as alex initially recommended, it's not complicated and takes 15 minutes, and eliminates this whole class of bugs.
Fix is being worked on, but just do the media/proxy thing now so you'll never have to worry about this again.
Mood

Alright, we found a second exploit that is much worse than the first one I found, it involves a bug in our oembed parser. A new release is being prepared right now. Unless there's a third exploit, this can be mitigated by disabling rich media in the pleroma settings. Frontends other than pleroma-fe might also be not vulnerable.
What alex is recommending here will also fix the issue, so you can do that as well:
There might be a second attack vector for the exploit, i recommend deactivating rich_media (i.e. website previews)
in your pleroma config for the time being
nostr:npub18htsymwgvzth35hka65qtr0xzku9vxp9agxqa9x6eyxrvke20w8qzqrk0m
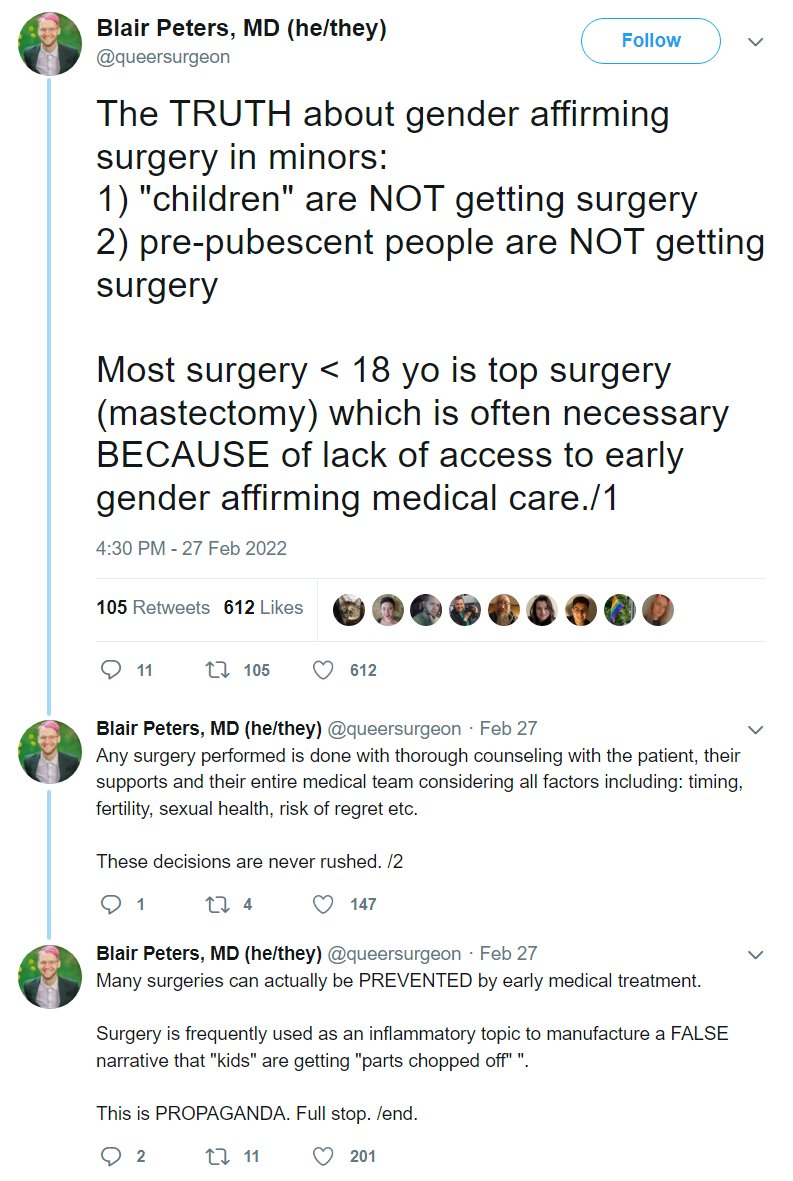
> they are not surgery
> but when they do it's mastectomy
???
Just to be clear, if you run a pleroma server, it’s a very good idea to add this to your nginx config immediately:
location ~ ^/(media|proxy) {
add_header Content-Security-Policy "sandbox;";
Most people will already not be vulnerable to this for a variety of reasons, but this will absolutely stop it.
Trending post topics on mastosoc:
- trans stuff
- racist, sexist, violent tech bros
- MAGA
- new mastodon app
- changing an icon is ageism and racism
- abortion
- fascism
- climate change