I do not stand with Israel.
I do not stand with Hamas.
I do not stand.
I have no legs.
I'll fix bugs with the post composer tomorrow. There is a collection of issues on GitLab now.
YouTube is gonna kill itself.

Soapbox has never looked so good, mashallah.


nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6 nostr:npub1vq7hd5tr7cxnaxurp90zlsg62s7udwllvfgesxlu0vhaqd0cy40qfpgx5j nostr:npub14qte6e3d5dykz86z8n2sslwluqnd6f7xz0wmcv8680e85pa5ptns944ml2 nostr:npub1rpr4g6wjgkz4493egxdutn8hvraf03hq09lff60mal3kuawef9yq6tn2gs > Linux Mint has no designer.
I havent used it in ages but it seemed fine. I wonder what you think of KekDE
KDE is mostly bloat with very little payoff.
The best DE was Pantheon for a while, until the devs forgot their gender and switched everything to flatpak.
Brb switching to Arch
The biggest most fundamental problem with Bluesky that nobody is talking about, is that it was designed specifically to be implemented by Twitter. And now that Elon owns Twitter and they no longer have that opportunity, they haven't shifted gears. They're still trying to design a protocol to be adopted by Twitter.
>bluesky
>$8m funding
>full-time dev team
>1/10th the userbase of fedi
>bridging isn't as a priority
TIL SQLite has a memory mapping option. https://phiresky.github.io/blog/2020/sqlite-performance-tuning/
Truth Social added Bluesky-like custom feeds. Except they're hardcoded and there's only two options.
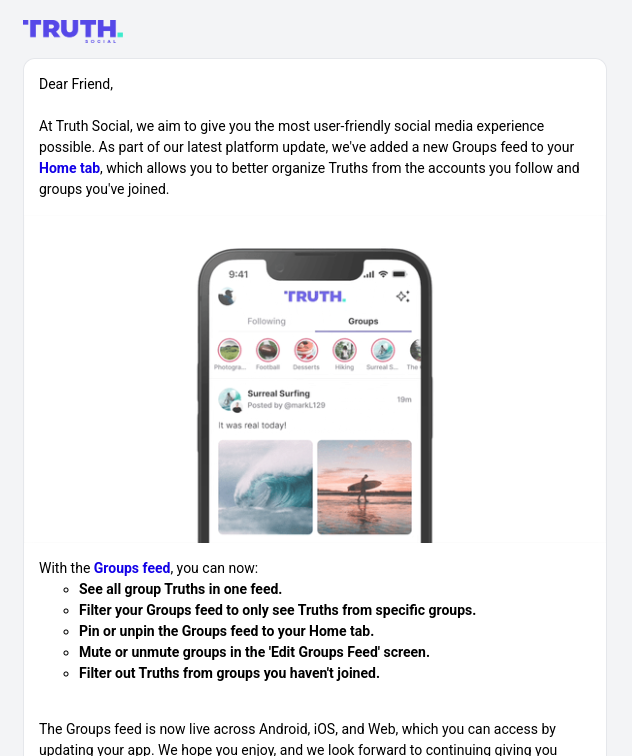
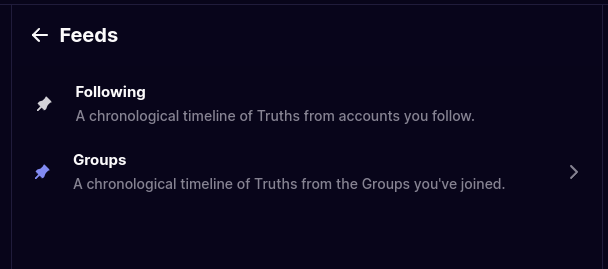
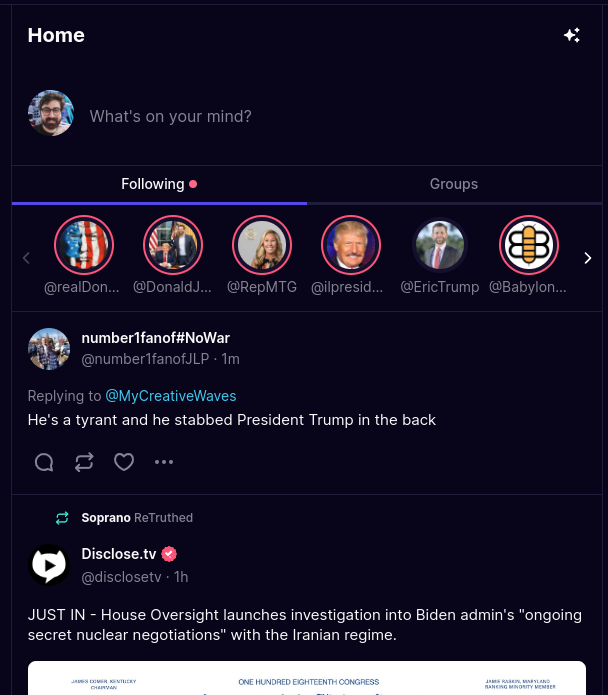
سبحان الله للشبكة الاجتماعية اللامركزية
Good news: I just improved right-to-left support in Soapbox. Now whether you speak Arabic or Hebrew, you can find it easier to argue online.
I'm working on improving routing on Coracle, and ran into the issue of deep-linking creating attack vectors for malicious links. To a certain extent, this is unavoidable, people can always direct someone to a bad event or link unless there's no navigation at all.
I'm more concerned about attackers being able to inject a malicious relay into Coracle, for example https://coracle.social/notes?relays=wss://my-evil-relay.com in order to phish someone's pubkey and correlate their identity.
How bad is this? I'm inclined to leave relay deep-linking out. But then relays are a resource in their own right, so I don't know if it's possible. Maybe ask for user approval before connecting to any relay not in their own relay list? This would cover malicious relay injection via NIP 65 as well.
Trying to grok the issue. A relay can send events with the wrong pubkey, but then signature verification will fail. They can also send wrong events for a filter, but then matchFilters will filter them out. In what scenario is it potentially harmful?






