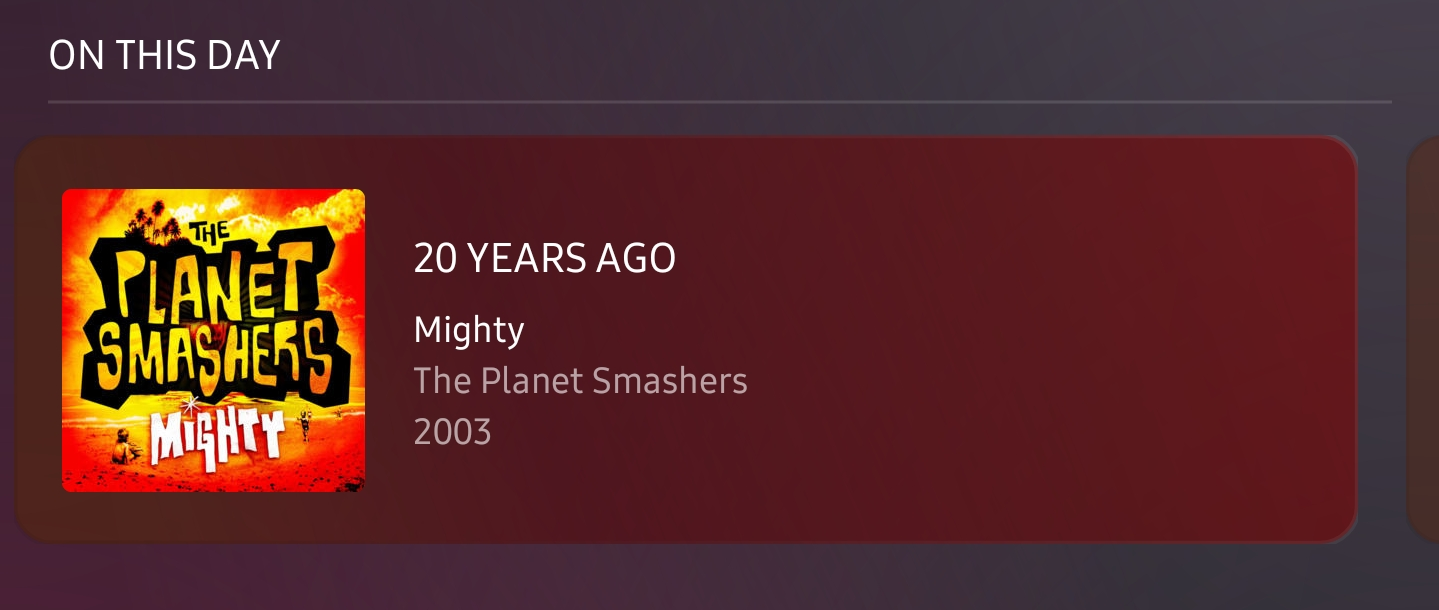
20 years ago today I was at this album release. I'm so fucking old
someone in the poast matrix asked me what the top 10 most followed users on poast were so in case you guys were wondering:
pleroma=# select nickname from users where local = 't' order by follower_count desc limit 10;
nickname
-----------------
Jim
josh
graf
RekietaLaw
Shadowman311
randbot
GatorTime
Wormwood
FelonyCommitter
DK_Dharmaraj
(10 rows)
TIL animal crossing makes gentoo reference

this is bordering on harassment at this point
the only thing in the ""leaks"" from poast anybody besides josh cared to talk about was dick pics sent in chats. it's a joke
for those wondering, here is the complete exploit by user "Fallout76" (ironic) attached as a txt file in a zip because soapbox FE sanitizes for this. this works on pleromaFE (not soapbox) maybe other FEs
the file has been deleted (was several days ago) and i have disabled pleroma FE for now until this vulnerability has been dealt with
https://i.poastcdn.org/a54c369be1f0e4f830646b07770c1e06cfda5bb4a0dcd75061a1a1fcd9d9a4fe.zip
>sonic oc posters start joining poast 3 days ago
>'hack' happens
sonic has the most fucking cursed energy
hey friends,
on may 19, 2023 an unknown user registered the domain name fedirelay.xyz and setup a fake mostr (nostr) relay to listen for requests on the fediverse.
on may 20, 2023 at 20:52 (utc) a user uploaded the attached document to poast. it was originally an obfuscated javascript file (unobfuscated and attached it here, renamed to .txt so you can view it in any editor).
what this javascript file does is take the viewers oauth token, encode it to make it look like a nostr pubkey and then forced the clandestine mostr relay to look up that user locally giving that server the encoded token all while appearing to be a legitimate mostr (nostr) bridge
i have taken steps to completely limit access to the admin api and corrected any CSP or other issues that could possibly have contributed to this, however most of you are still vulnerable to it. the default pleroma install serves media files on your root domain as a local folder (i.e. yourdomain.xyz/media) and the default CSP for any site is to allow executing scripts via the root domain. in order to prevent this you should take steps to either move your media from yourdomain.xyz/media to media.yourdomain.xyz (or any subdomain outside of your root domain) or perhaps by limiting the CSP for that subdirectory via nginx configuration.
if you are an instance owner, the obfuscated file hash is `b2977f2d97f598d2ebd6dcf37afd9047b5da2b6dc95a7b2824fb111c906fb117` so you can search yourdomain.xyz/media/b2977f2d97f598d2ebd6dcf37afd9047b5da2b6dc95a7b2824fb111c906fb117.js and see if you have it on your server.
sorry to anybody i let down but i could never have foreseen this level of sophistication and i would not have ever expected it. now that we are aware of it, we will be more diligent in the future. thanks for being here with us still friends
https://i.poastcdn.org/4ed28ef4fa5e18bfa5c1f75a5c1cc759f7b718c0b600e7e2fcc6d0cdb0215f15.txt
i am not sure the breadth of this yet, but my username was briefly changed using oauth tokens. i am trying to figure it out. i dont know the source at this time but i can confirm someone did change my name.
im sorry, im looking into it now
nostr:note1sxjcl4pjjldmchn96lje5v2nsydw6s9wvh5nszzaugv9juttwqusdjh77r
hmm yes, very wise
got totk running at 30fps stable in hyrule field on steam deck. we're so back
glad you're still around friend
>people are using .zip domains to make phishing URLs
example: https://github.com/kubernetes/kubernetes/archive/refs/tags/@v1.27.1.zip
to a normal person this looks like a github url but the @ at the end tells outdated browsers its hosted at v1.27.1 dot zip
thats funny as hell
beautiful evening outside. cracking a pint and firing up the grill. mashallah
women will never get it (the orgasm)
hey wyd
nostr:npub190g9xdz7zzhd9z7sa97rzx4tx3c0d4l5qhw93zc9d08puduh6tcqmrqj79 nostr:npub1el3mgvtdjpfntdkwq446pmprpdv85v6rs85zh7dq9gvy7tgx37xs2kl27r wait are you the REAL nostr???????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????
