Fourth Dan is where it’s at
Tae Kwon Do… anyone? Bueller?
I’ll just show myself out.
I saw a neighbor allow her 5-6 year old son decide to not get on the bus to kindergarten on the second day of school.
Children are not ready to make their own decisions about never leaving their comfort zone. Who’s the parent?
I’m a parent of 4 from 4 years to 12 years old so I speak from experience.
Superman’s Dead by Our Lady Peace mentions the subway several times
Yes i solved a problem this way. I was trying to figure out how to generate a password that would always pass complexity requirements without reducing the entropy.
I woke up that night with the simple solution immediately top of mind…
just a loop that generates a random password, then tests it for complexity. If it doesn’t meet complexity requirements, loop again. If complexity test succeeds, return that as the generated password. (And a max loop count to avoid infinite loop conditions, of course.)
Moon landing can be verified visually from earth with telescopes or lasers
If you can’t scale storing and transmitting text with computers, then you’re not good at computers.
Thanks to Pi-hole (primary DNS server for privacy) and AdGuard (secondary and tertiary DNS servers for protection when pihole is down) my network is so much faster than people without network level blocking.
If you can’t run pihole just plug the AdGuard DNS servers into your Wi-Fi configuration. The family servers also block adult content for family friendly internet access.
The hard drive lasts longest that never stops spinning.
Many long experienced IT people have known this for 20 years.
To what campaign are you referring exactly? She’s never gotten a single primary vote. She’s been selected by the DNC leadership with no regard for democrat voters.
Let’s go with some new #nostr content!!!
I have a 100 sats for original #lego builds replying to this with pics. I’ll try not to cap the number of zaps but this is my first #bounty so we’ll see how it goes.
I propose anyone interested in Lego follow and use the #brickstr hashtag.
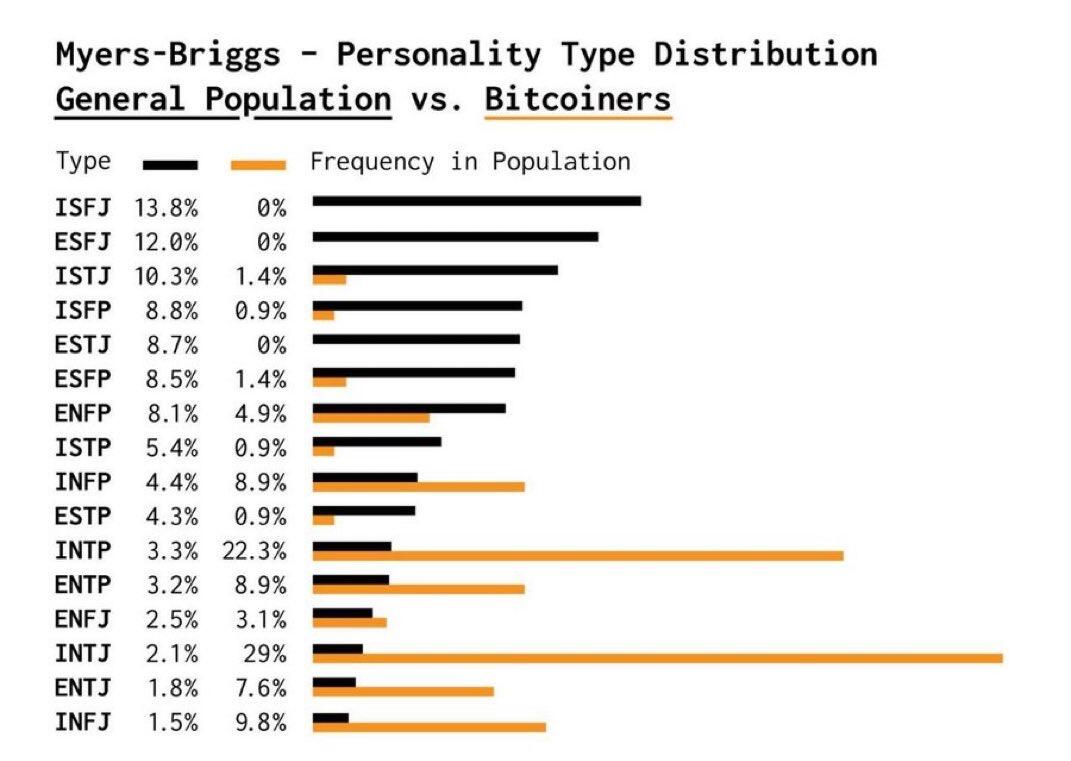
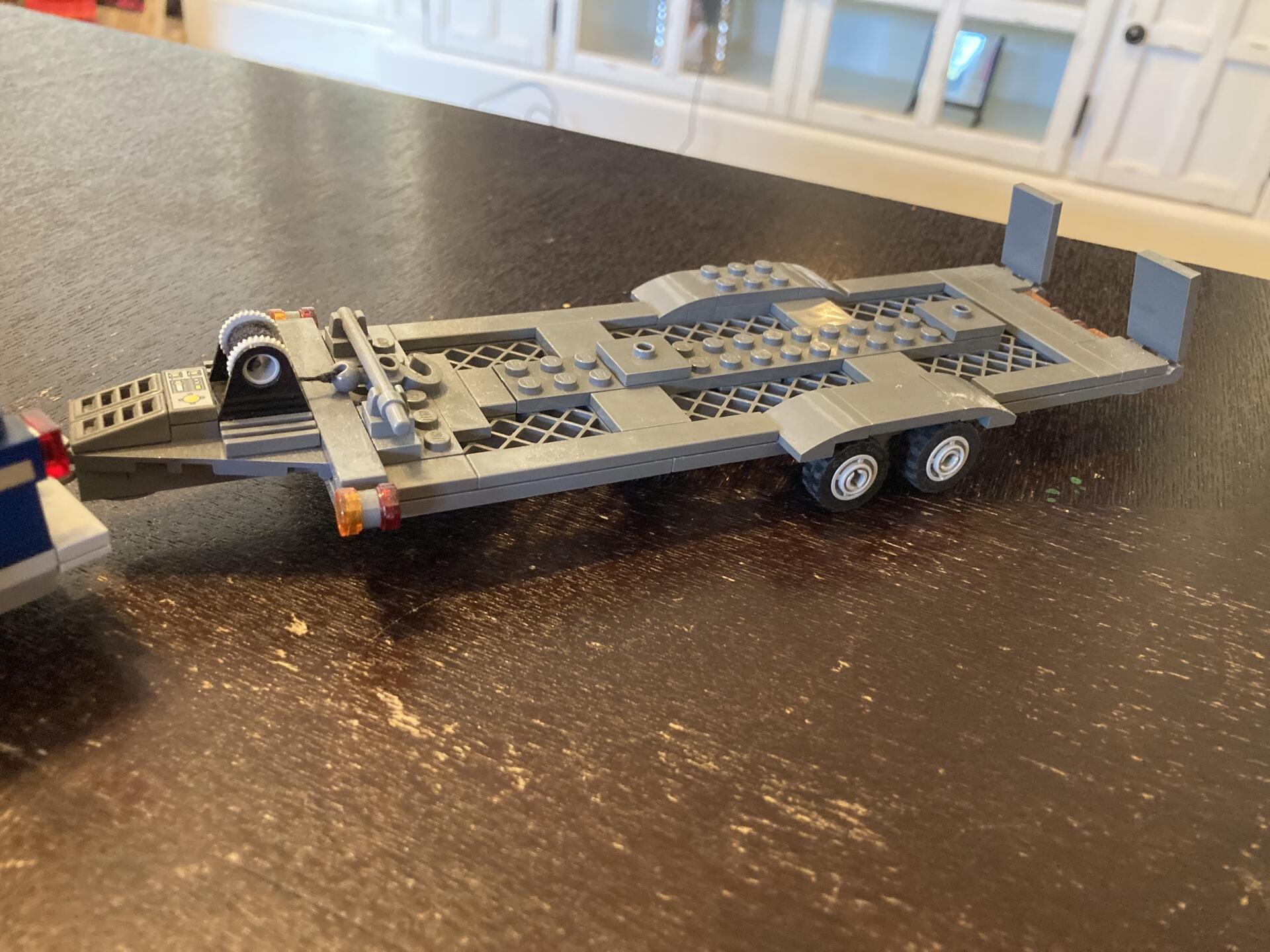
I’ll start with this dualie pickup with car hauler trailer. It’s my own design but I likely stole some exterior aspects from designs on bricklink or rebrickable.
Scale is 8 knobs (wide) and the trailer is for hauling the current speed champs of same scale. 

We didn’t use the secp256k1 curve for nothing. If you want weaker curves, NIST has a couple.