imo the best #gunstr
https://apedefense.com/shop/ar-15-parts/stocks-grips/ape-pistol-grip/
Funny how this works. Couple years back, I cheekily gave my audience a 'homework question': https://reyify.com/blog/homework-answer-advancing-2022
Just this week, I realised that it's a solution to a problem that's been bothering me for a while: cool, I can use Curve Trees to get an efficient ZK proof of knowledge of 1 out of N secp256k1 pubkeys (e.g. taproot utxos), but isn't that a bit useless to limit usage, if a bad actor can just keep generating proofs indefinitely, using the same pubkey, but we don't know because we wanted the ZK property for user anonymity?
Because curve trees use a 'rerandomised' pubkey, we can use the above 'homework' proof (proof that you know the opening of a Pedersen commitment), plus a DLEQ, to create a verifiable key image, that can only be used once, for a specific curve tree (which is an accumulator that everyone can reconstruct, using the blockchain - e.g. 100k taproot pubkeys).
This can give 'decentralized' anonymous usage tokens (i.e. without an issuer), with very large anon sets without bad prover or verifier computation blowup.
More detail: https://github.com/AdamISZ/aut-ct.pdf
tsch. the teacher could never provide a simple answer when we students asked what are some real world use cases for ring theory. luck is when preparation meets opportunity.
BREAKING: New York Times “journalist” Dick Cuckerson is a BANKER.
The nostr:npub10qrssqjsydd38j8mv7h27dq0ynpns3djgu88mhr7cr2qcqrgyezspkxqj8 investigative team worked closely with nostr:npub13tctmes9ug5gcj4huj92ryw2ky600l62xwmkssdn9mmkf8y0u6jq5g7qx7 and made the shocking discovery early this morning.
Can’t believe NYT is hiring bankers to write their #Bitcoin FUD op-eds…
These anti-Bitcoin propagandists are a DISGRACE. 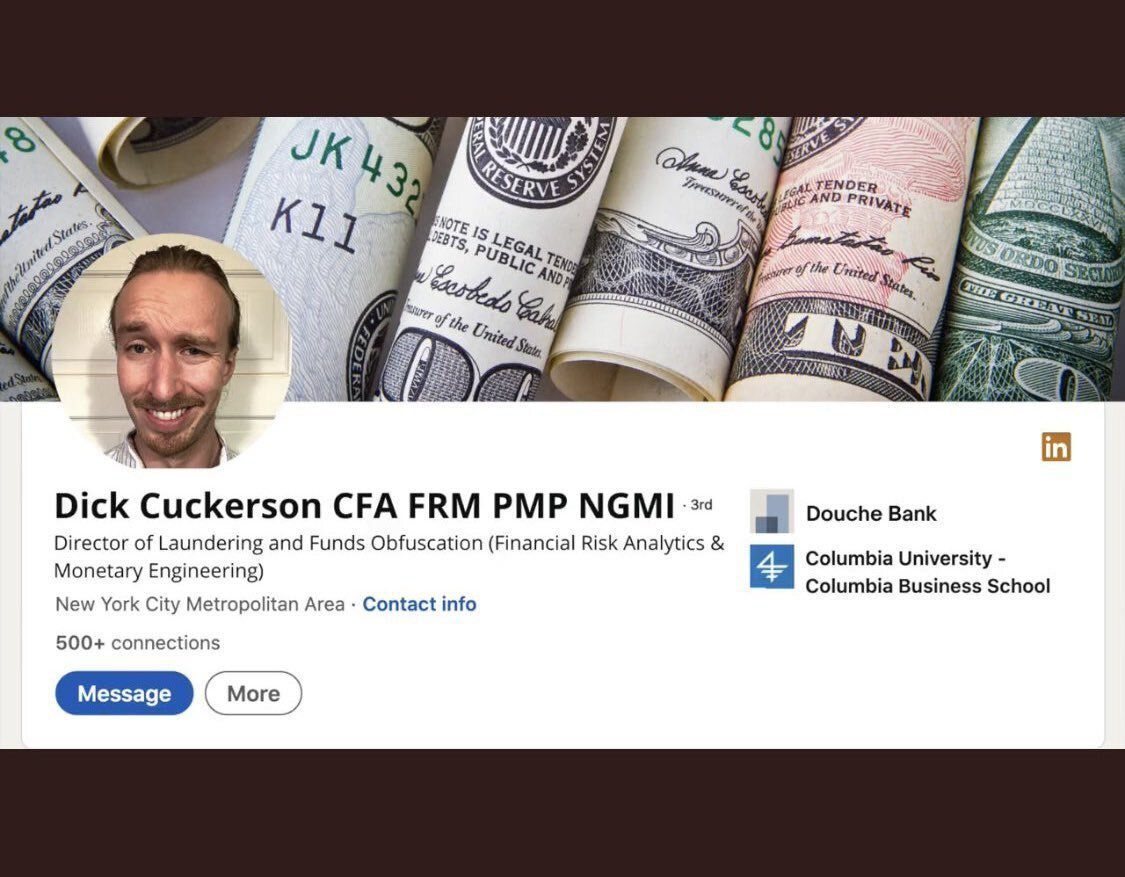 nostr:note13595xhlxadtkpqjqa4p5j3quesq8m4n7m7sj222nhe9unzaqfwvq7cl9wa
nostr:note13595xhlxadtkpqjqa4p5j3quesq8m4n7m7sj222nhe9unzaqfwvq7cl9wa
oh my god
of course the govt planted child pornography on his computer, that or the CIA hires pedos
Yo, where my nerds at?!!

I created a bitcoin mnemonic that starts with "coffee".
Its fingerprint is c0ffee4b
It has a receive address that starts with 3Coffee
That address wrote an OP_RETURN that says "c0ffee inception!"
And the txid of that transaction starts with... c0ffee!!!
https://mempool.space/tx/c0ffeebcb6682294ebe29f06e0afb790f23f551d5c592b59bce1ccaffe128049
Jesus, Keith...
Twatter collects so much more information, including IP addresses, sooooo
I finally found a fix for Windows failing to install KB5034441 update
GM PV
gm #plebchain
build a nostr:npub17tyke9lkgxd98ruyeul6wt3pj3s9uxzgp9hxu5tsenjmweue6sqq4y3mgl
Hell yeah GMRS!
Extra detail about privacy: privacy is not secrecy. Privacy means having the ability to communicate privately without interference from others, but it does not mean that the communication is not heard by others. Encrypted communication is a violation of the FCC regulations. Likewise, it’s even illegal to speak in code phrases except the commonly known 10 codes.
Do not use GMRS for secrecy.
“In a closed society where everybody’s guilty, the only crime is getting caught.”
—Hunter S. Thompson
nostr:note1cvgdz8xq947hssnew8h55zerthvml7dml4fjud4n24mqk9w8s4usgalfhv
Hell yeah GMRS!
Extra detail about privacy: privacy is not secrecy. Privacy means having the ability to communicate privately without interference from others, but it does not mean that the communication is not heard by others. Encrypted communication is a violation of the FCC regulations. Likewise, it’s even illegal to speak in code phrases except the commonly known 10 codes.
Do not use GMRS for secrecy.

 #m=image%2Fjpeg&dim=1153x2048&blurhash=%5DAELjA%25NK69tR.M%7B%7E99tRjs%3BtJJ%25MxRPajRRV%40EMNGoI%5EPwzOFJBSg%3FGWXspV%7BRQ57oza3n7s.RONGs%3Bt8a%24Ion%23o%23ohWY&x=c627289a61a375d118a672565629f050e15c79a0ea769399d036751660fd4632
#m=image%2Fjpeg&dim=1153x2048&blurhash=%5DAELjA%25NK69tR.M%7B%7E99tRjs%3BtJJ%25MxRPajRRV%40EMNGoI%5EPwzOFJBSg%3FGWXspV%7BRQ57oza3n7s.RONGs%3Bt8a%24Ion%23o%23ohWY&x=c627289a61a375d118a672565629f050e15c79a0ea769399d036751660fd4632

 #m=image%2Fjpeg&dim=756x1008&blurhash=_FFq%7B%3B%3Fu0N%25LXn%25L%3FF%3Fa%25MEg%25L%7EAxubb0%25oe%7D%3F%251t7NHE2t7NH-U%24%2558RQni0%24s.xZNH-8xaShEMxZ%251I%3BWCW%3DNH%24%25kBWqjFNHS%23xZWqxFWVNHjFoftQw%5EW%3BkCj%5BRkw%5DoJ&x=921a5976a81f702cedc74bc63d6cfbae225437abe40d35d17cb9aa9c0b53e9cc
#m=image%2Fjpeg&dim=756x1008&blurhash=_FFq%7B%3B%3Fu0N%25LXn%25L%3FF%3Fa%25MEg%25L%7EAxubb0%25oe%7D%3F%251t7NHE2t7NH-U%24%2558RQni0%24s.xZNH-8xaShEMxZ%251I%3BWCW%3DNH%24%25kBWqjFNHS%23xZWqxFWVNHjFoftQw%5EW%3BkCj%5BRkw%5DoJ&x=921a5976a81f702cedc74bc63d6cfbae225437abe40d35d17cb9aa9c0b53e9cc