Beautiful night at the pee wee fields 
Bitcoin accepted -> Bitcoin preferred -> Bitcoin only
Will be interesting to see how far down that progression we see society and the vendors within it go.
Little bit disappointed the funds available in my HSA don’t include the bitcoin ETFs.
That time you are listening to the Stephan Livera podcast and the ad read is for a service that is for one million dollar net worth and above. I didn’t get into Bitcoin early enough for that madness.
I can’t imagine the panic of being in a suit like that if the water cooling systems failed. I think I’m just too claustrophobic for that.
Isn’t the whole reason to outsource these functions is so you can blame the vendor?
I’m not quite sure how to measure its accuracy. But it seems pretty close. I did a couple of mile walk that day to get those steps.
Is my watch telling me I slept walked? Don’t remember getting up… 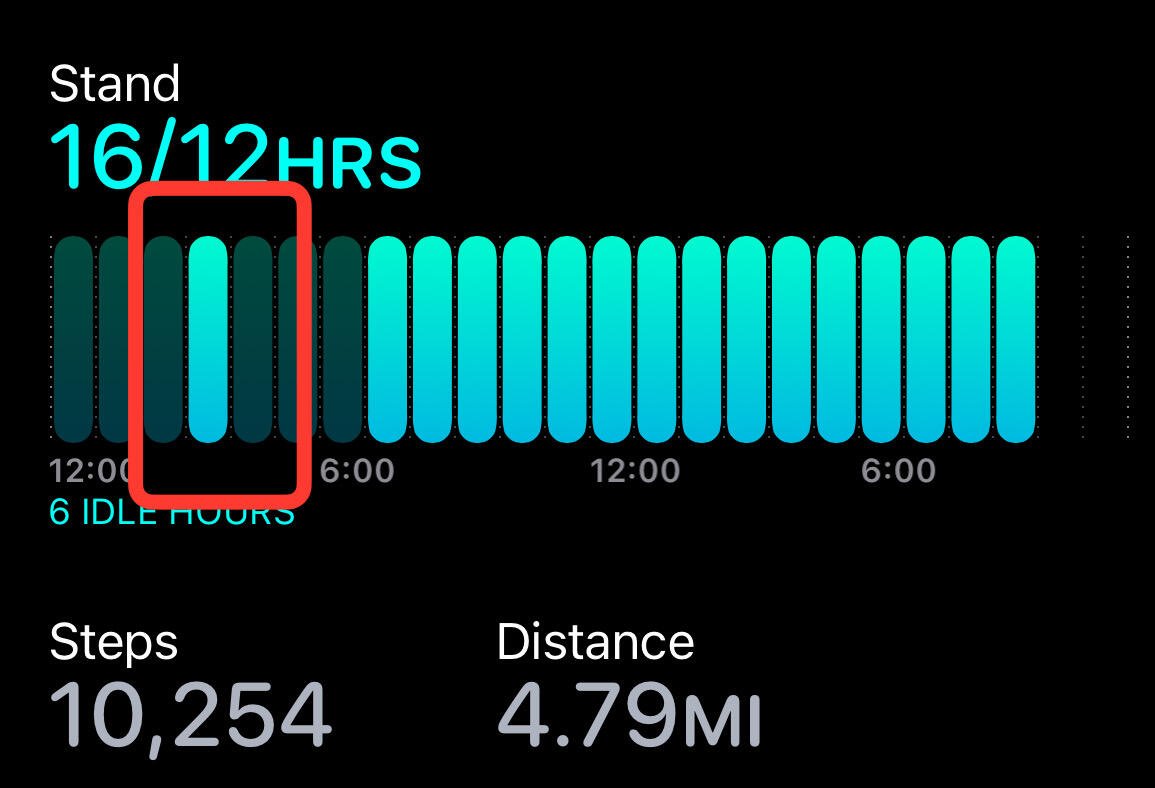
I mean I know two people that died of Covid who didn’t get the vaccine. There might be some survivorship bias. That being said, I don’t think it should be forced on anyone.
According to my wife a cruise thru the Drake passage isn’t an acceptable bucket list item.
If I understand this right, the relay would be able to see the public IP of every client and correlate that to the group IDs that they are downloading? In the worst case of a note being published to a single malicious relay, that relay would know the public IP of every client that downloaded the note and know that they where a member of the group (or at least have high confidence of it)?
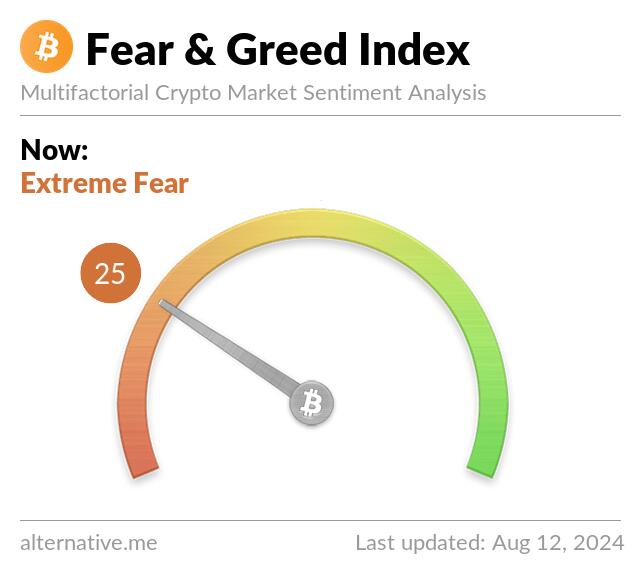
There doesn’t seem to be enough momentum or resistance in these measurements. They seem to swing wildly from one extreme to another based on whatever the news of the day is.
I wondered about this as well. How does the podcast economics work? Does the host pay for bigger names to come on their show? Do smaller names go for free just for the publicity?
My friend nostr:nprofile1qqswum4p82uluhz2dr40nvdrflspffntgqghc58w9fs57nx6jkdkuaqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3jamnwvaz7t68g9xyzkzexyejumn0wd68yvfwvdhk6qtxwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tmwwp6kyvtpv45ry7nhx3jkceth0y6nvwpjd3uxxdncdek8z7n2deuxkum3xvcrxemhw5exuurxv9uxgdpewekkgefkw93hzdrwwaur7cnjdaskgcmpwd6r6arjw4jscep45n wanted a bot that said "fuck" followed by 12 words from the BIP39 word list. So, I made a bot for him. This bot disrespects a different Bitcoin wallet every hour. Maybe one of them will be yours? I'm sorry 😂
Maybe some one else writes a bot that checks the generated wallet for any bitcoin. 
It’s a sad day… nostr:note1mnyfl9hjck35mw67hd659j6a2gxltmyhzq684lm99xnf6wzyeunsh33fy8