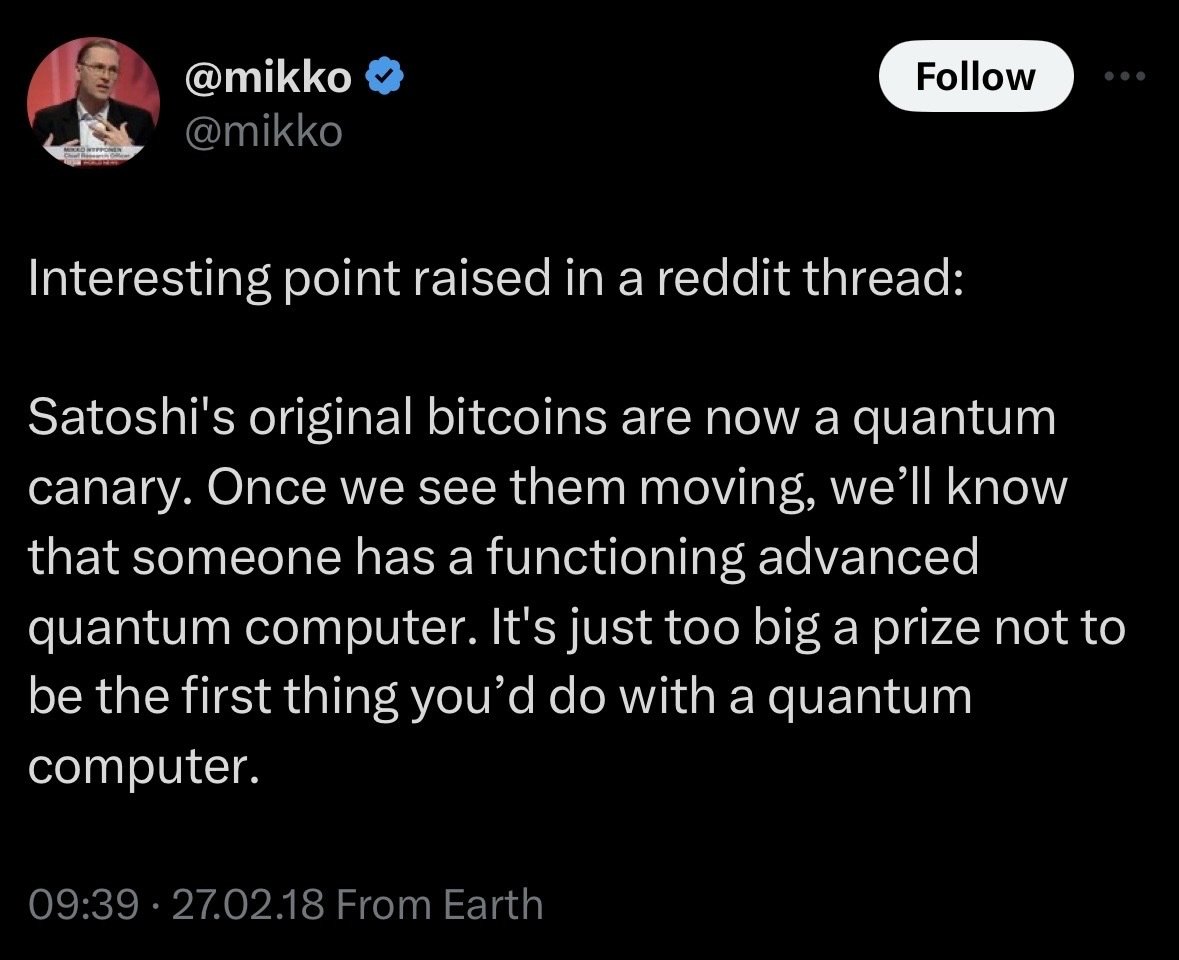
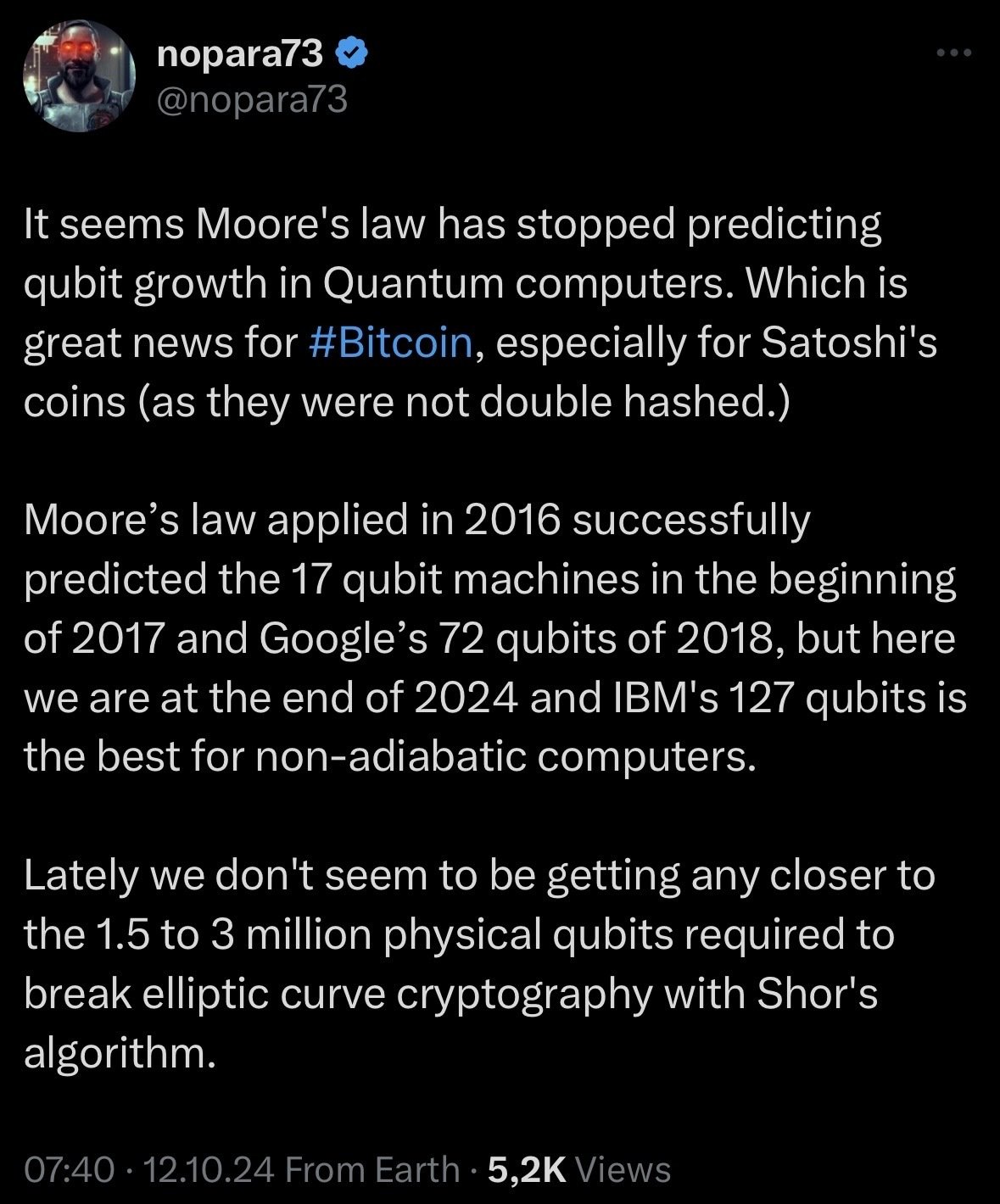
SHA256 has another 10 years i reckon... and sec256k1 probably another 20, before they are "theoretically broken"
it's important to understand that what the media says is the dumbed down, hyperbolic version
the reality is that "breaking" md5 did not mean instantly you could reverse an md5 hash on a hash-sized thing, most likely target being a password, it was just a way to reduce the time a brute force attack would take by a fairly substantial degree... i mean from 100 years down to 30, sorta thing.
"broken" is always used hyperbolically by the media as is "unsafe" by those who have claimed that secp256k1 is "weaker" than edwards ed25519 or other curves... bitcoin is still fully here, and running just fine and nobody has broken a single signature on the chain that wasn't created in a broken way, to recover the key
those keys were dodgy secret keys in the first place, the few cases you can find, that's how they did it, weak entropy, a very small search space to brute force it
breaking sha256 is not going to happen any time soon, and there really is no actual facts behind the hyperboly of Schnorr's algorithm, which can be performed with a quantum computer.
nobody has broken a key with a quantum computer yet in a legitimate, fully dangerous way, and this story most likely is a case of a broken key generation algorithm as well
normies just can't comprehend the time scales and numbers involved in actually cracking these codes, and the press are just pulling eyes so they make it sound a lot more momentous than it actually is