Maybe I am missing something, but with a tool like Amber on a device that only I control, I am sure only I can use those keys, accept requests and sign, but with this enclave thing, which is "online" and you "connect" to it using a frontend (I guess), how does this work? Is the frontend part of nsec.app running client/browser side? How can I be sure only "my device" (as long as I don't delete website data/cookies of nsec.app ?) can access those keys? How does this differ from Amber?
Store your nsec in a secure enclave!
We've spent a big part of 2024 trying to make a reliable non-custodial signer with nsec.app. It hasn't worked out perfectly - remote access to keys stored on a mobile device is still unreliable, especially on iOS.
That's why we got very interested in AWS Nitro Enclaves - h/t nostr:npub136jg2fnty2z5vwcnh7p4jpckrs3tk0dpueftgs7mznuuaenjpfps6tjnxf and MapleAI team for inspiration!
The idea is to have an open-source custodial signer and deploy it in an isolated environment that provides attestation for the deployed code. Anyone would be able to reproduce the code build and verify that the signer is running the correct code in a safe environment.
So here it is: https://github.com/nostrband/noauth-enclaved
Each instance of a signer deployed in an enclave announces itself on Nostr. We added some Nostr to attestation provided by AWS - the report is linked to pubkeys of a person building the code image, and a person running it. This way you can choose a signer based on your own preferences.
It's already integrated into nsec.app, go to Settings => Secure enclave and try to upload your keys to the server. The signer API is described in README.
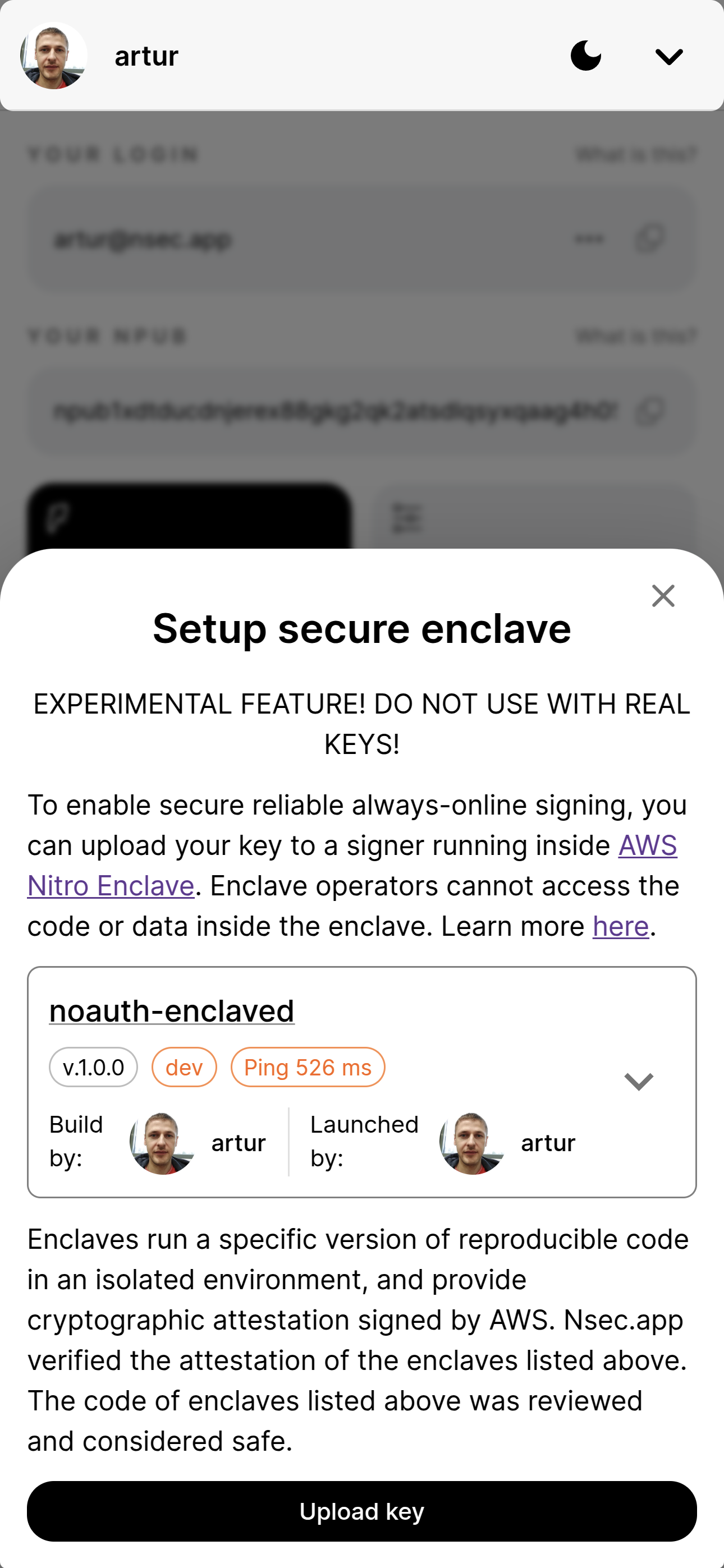
DO NOT deploy your real keys just yet - it's running in a production environment, but the code hasn't been well audited yet. First we need some community members to review the code and reproduce the code image.
The signer can also be used to generate throwaway keys for automated testing of nip46 implementations, check out "generate_test_key" method.
Looking forward to your feedback!
(Signed by my nsec from the enclave)
Discussion
Amber works great for apps on the same device. Cross device it has same issues as nsec.app - Amber is killed by mobile OS and can't process requests reliably.
This enclaved signer can accept your nsec and process requests to it. You still retain your nsec and can control the signer with it, that's what nsec.app does. Your local key just can't be always-online.
Does it make sense?
Mmhh I get what you say about the drawbacks of an in device signer like Amber (even though I think it depends on the usage one has with a nostr client), but I don't really understand the "you still retain your nsec and can control the signer with it", but probably it's just because I didn't fully understand the overall logic flow.
