We are getting DoSed. I deployed an update with stricter rate limits and things seem to be improved.
Hi nostr:nprofile1qqsqgc0uhmxycvm5gwvn944c7yfxnnxm0nyh8tt62zhrvtd3xkj8fhgprdmhxue69uhkwmr9v9ek7mnpw3hhytnyv4mz7un9d3shjqgcwaehxw309ahx7umywf5hvefwv9c8qtmjv4kxz7gpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7s3al0v x nostr:nprofile1qqsywfvswmy9lyjqapfyyrtjz0y4a9gs9uw7j20mvren5tpj2uxf33qprdmhxue69uhkwmr9v9ek7mnpw3hhytnyv4mz7un9d3shjqg5waehxw309aex2mrp0yhxsmmydshxzu30qy08wue69uhkzerdd9hzu6tsd4hhxctfvdhjucm0d5argwp58qhsefcr7x sometimes I see this message when scrolling the ditto feed.
Discussion
Traffic details pls. Just curious
It's just one IP hammering the Mastodon API. But this has never happened before so I didn't configure rate limits. It was easy to fix.
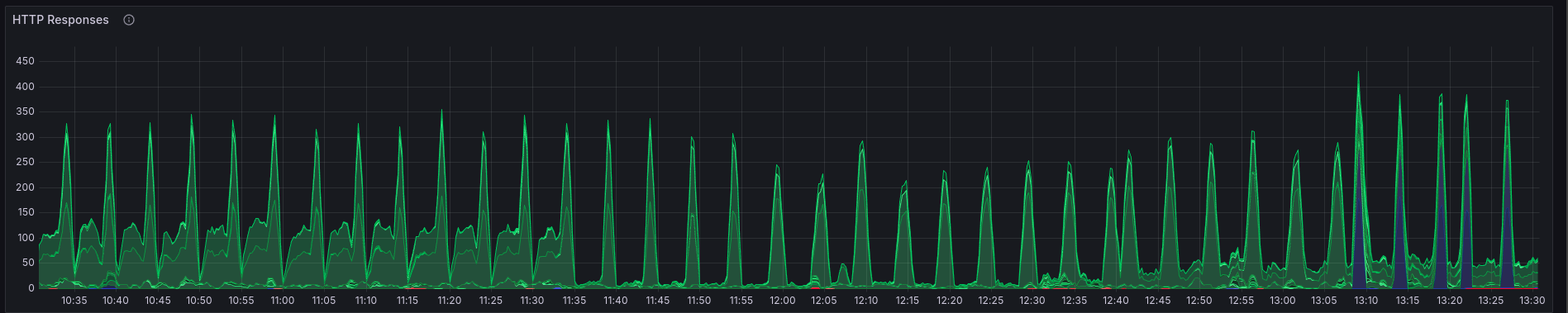
The blue spikes on the right are 429 errors after applying rate limits.
Are layer 7 attacks possible? I assume so, but idk the codebase. Just curious if you can horizontally scale away that problem.

