#GrapheneOS is still not vulnerable to Cellebrite device exploitation as of the February 2025 support matrix. Appears the documents have leaked online in multiple places. I'll make a larger post summarizing it when I have time.
Here is what you came to see:
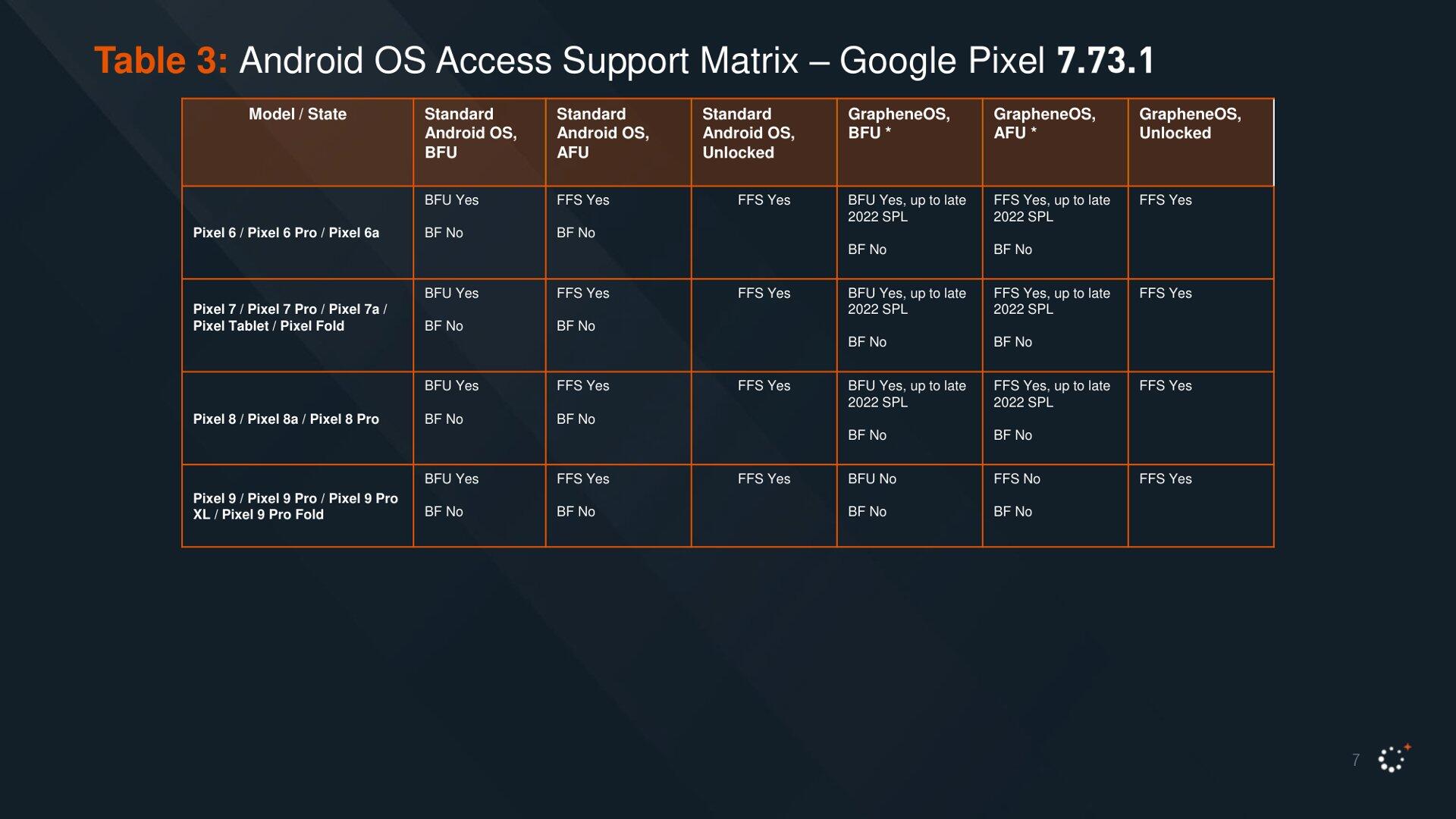
Pixels with GrapheneOS remain the only device explicitly mentioned by Cellebrite as being unaffected by their exploits, and remains the only third-party operating system in their documentation entirely. We are the leading contender for mobile security and this is a great real world example.
Here is a blog post that summarises the big pages for Android devices already:







