Yep, blockchain is good for ordering (time) only. Absolutely critical for #bitcoin; important, but not critical for #nostr
Putting this out there...
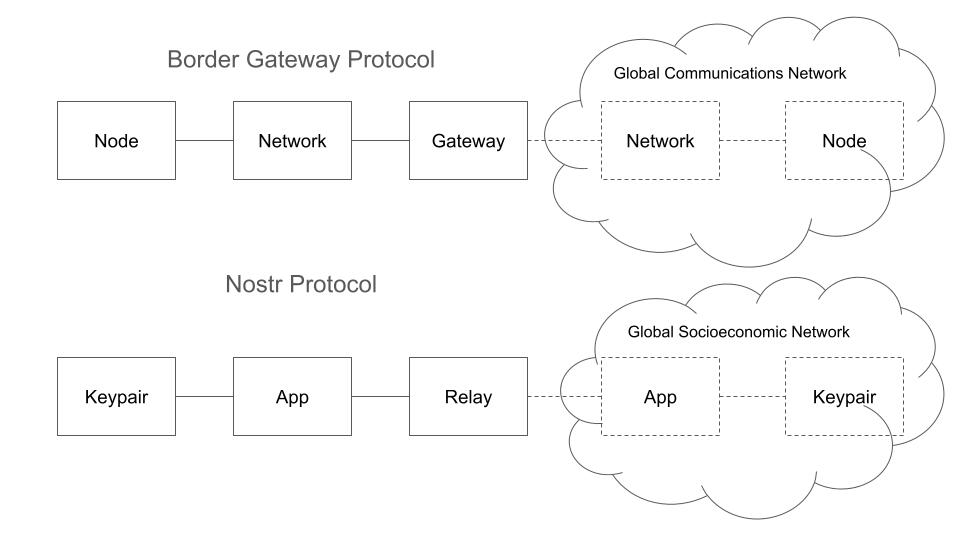
Back in the early days of the internet, it was the Border Gateway Protocol (BGP) that enabled the internet to globally scale. In brief, (show below), a node connects to a network, which connects to a gateway which made everything look like a singular network, namely the internet.
I attempted to find the same pattern to #nostr - and what I came up with is also shown below.
It's a similar pattern to BGC - three things: a "keypair"(npub/nsec) which uses an "app", which, in turn, connects to a "relay".
This pattern is parallel to BGC, the keypair uses an app which connects to a relay (or relays) that makes everything the #nostr network look singular. This is what makes the #nostr protocol compelling.
So, in addition to a "global communication network" (i.e., the internet), we now have a "global socioeconomic network" (the #nostr network).
For me, it makes it clear that the end game is not a "killer app" but rather building many apps that can leverage the #nostr network as a singular whole.
Comments welcome!
Using a NIP-05 service would be nice as well. I am thinking that NIP-05 could evolve into a trusted name service where I could rotate my pubkey if required.
“Communication is a manner of selection by one party intended to serve as a motivating structure for the other party.”
Niklas Luhmann, Trust and Power [slightly paraphrased]
“Mathematically guaranteed ownership.” nostr:note1y85wyg7ffv8qhhvvflm78l5papumgfgaf4k5rdzccwnnvdmk3t2q3csrfc
I can try what I want.
Maybe. I am looking to replace my wallet component. Want to use a relay as the datastore- not a db.
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 why does mstr insist on using “the blockchain” for DID?
Is there no other practical way to add key rotation?
https://github.com/MicroStrategy/did-btc-spec/issues/7#issuecomment-2245601679
Key rotation for a ‘name’, not an identifier. I’ve been looking at this problem for a long while and have concluded that this problem needs to be solved at a higher level. I think a trusted nip05 provider that keeps a history of keys (npubs), is a better approach. I think key rotation at the did:method level is not the way to go.
Super! nostr:note1f3jnuts89mndzhu4m9qc48ezyn0g6yj2p5alkgqujazvn870p7nsefqd2f
This is little more than an idea - #nostr #safebox . Let's see how this goes....
Nostr SafeBox is like those hotel safeboxes where you put your passport and money in while you are travelling. Digital travelling should be no different. You should be able to access your safebox whenever you need it - and get rid of it, when you no longer need it.
Still super-early - working on the concept of a ‘safebox’ for Nostr. It’s a generalization of the wallet concept for storing secure, private personal information.
The idea is that the safebox contains different item types, wallets, records, etc. You can give a client access by providing the `nsec` of the safebox. If you no longer trust the client, you can transfer the data to another safebox and delete the current one (no guarantees on deletion, of course)
#Nostr fixes this. 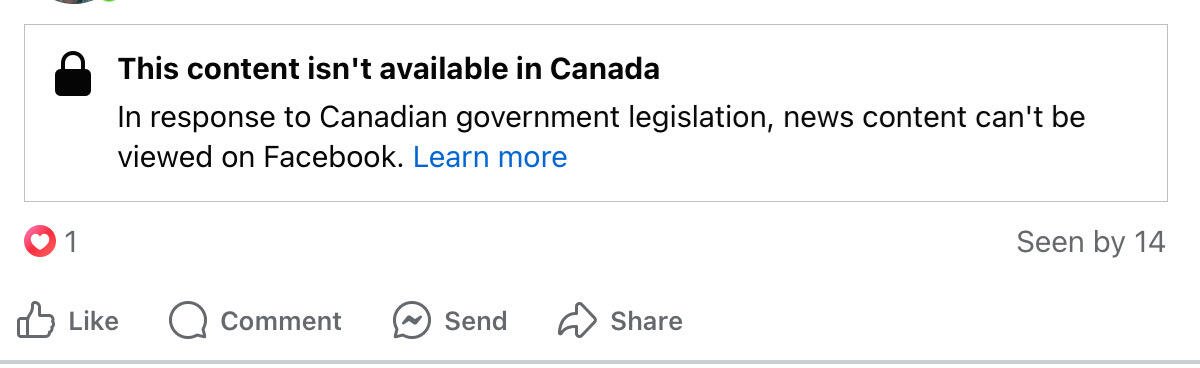
No one should have admin rights to your soul. Use #nostr
I can’t help shake the sense that society is going through a collective Stockholm Syndrome phase with vendors with which they have little choice.
For reference:
Stockholm syndrome is a psychological phenomenon where hostages or victims develop positive feelings, empathy, and loyalty towards their captors or abusers. This can occur over a period of captivity or abusive relationship. The syndrome is named after a bank robbery in Stockholm, Sweden, in 1973, where hostages defended their captors after being released. It is considered a coping mechanism and survival strategy, helping victims deal with the trauma and fear they experience. 
“Any poorly-written software is indistinguishable from an attack.”
Update Arthur C. Clarke quote.
nostr:npub1m4ny6hjqzepn4rxknuq94c2gpqzr29ufkkw7ttcxyak7v43n6vvsajc2jl nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js nostr:npub1q6ya7kz84rfnw6yjmg5kyttuplwpauv43a9ug3cajztx4g0v48eqhtt3sh nostr:npub1dg6es53r3hys9tk3n7aldgz4lx4ly8qu4zg468zwyl6smuhjjrvsnhsguz nostr:npub1unsnfxtxsht58arcpq3d34rskx99zln79axv9v4awq5ar5sguv6qk68r2y nostr:npub1nf9vm6uhs4j7yaysmjn9eqlf7et5t6hvrkdqgpd995vcc9yfjyas0pxa3x
I am going to get started with daily devotions, including the rosary prayer.
I just wanted to make sure how willing are you to take part and/or advertise it to the Nostr network.
This is part of our daily routine.
A well-kept secret is more secure than any hardware device.
