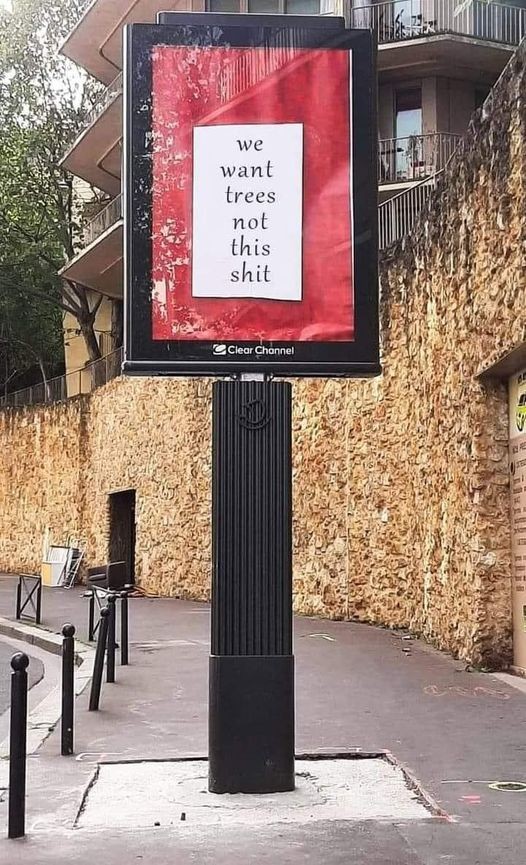
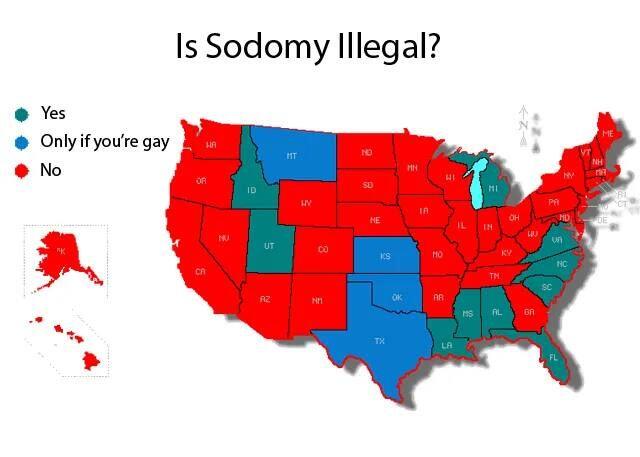
Ok, thanks for your answer!
So, no NIP-60 for now?
Pity. When I was setting a wallet on 0xchat and I saw the warning explaining that ecash is stored locally, I thought it could be a nice idea to use nostr relays as storage/backup for the nuts...
Thanks for your work anyway!
🫂
Is it coming to 0xchat??
👀
Looking forward to having my nuts backed up on some relays!! 🥜
You can dig deeper on:
Thx nostr:nprofile1qqs9pk20ctv9srrg9vr354p03v0rrgsqkpggh2u45va77zz4mu5p6ccpremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcppemhxue69uhkummn9ekx7mp069f2j4 for pointing out the small button in Amethyst PM that secures PM with NIP-17, giftwrap.
nostr:nprofile1qqsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqpzamhxue69uhhv6t5daezumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qgwwaehxw309ahx7uewd3hkctcscpyug thoughts on making NIP-17 DM's the default option?
🫂
BitKey - Mi primera Hardware wallet de Bitcoin (ESP-ENG) #hispano #BitKey #mexico #nostr
You can read the blog here:
https://blurt.blog/blurt-1831602/@cristo/3sx81r-bitkey-mi-primera-hardware-wallet-de-bitcoin-esp-eng

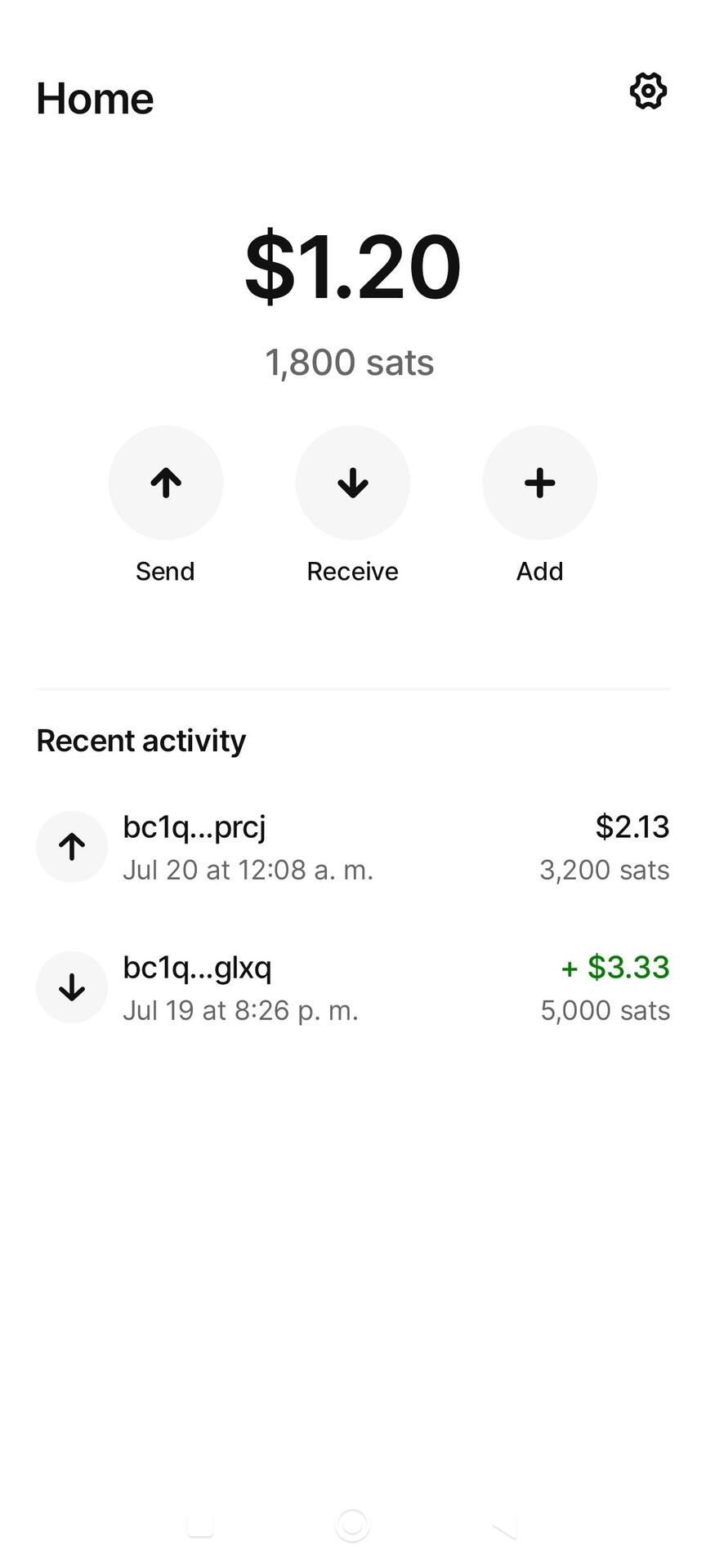
Interesting.
But I must mention that those utxo's appearing in the screenshot are too close to become "dust".
https://unchained.com/blog/small-utxo-bitcoin-dust/
I suppose those were some testing transactions, thus being small amounts, but I reckon it's important to consider that onchain is not the best option for such small amounts transactions.
Anyway, just trying to help.
🫂
I mostly agree.
The good thing is that NWS doesn't need the whole internet running on it in order to be very useful in some cases.
🫂
In the coming age of Generative AI, will that only applied to content signed cryptographycally, as in #nostr?
A permissionless npub (can't be censored, theoretically) replacing permissioned IP+DNS+CA (each of them could be censored) to publish web services (HTTPS).
It works using nostr relays to proxy we client and server, and nostr npub as service identity.
🫂
What?
😲
I'm really interested in:
- communication between apps, a la nostr:nprofile1qqszm52qe2qdkc4u7dma0klx3532jka2g8geck6fwxncyp90wktq2xspp4mhxue69uhkummn9ekx7mqprpmhxue69uhhwetvvdhk6efwdehhxarj9emkjmn9qy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsy47788.
- app store/publication a la nostr:nprofile1qqs83nn04fezvsu89p8xg7axjwye2u67errat3dx2um725fs7qnrqlgpzdmhxue69uhhqatjwpkx2urpvuhx2ue0e2p4dj
🫂
Regarding communication between apps possibilities:
I don't blame the raccoons.
Yes, that's true for a shared domain, yes.
The TXT record points out directly to the final user. True.
On the other hand, DNS architecture allows the user to hide behind a DNS recursive server (from the ISP, institution, DoH providers, etc), whereas it's easier to leak your final IP to the HTTPS server (if you don't user a webproxy).
Different privacy compromises, I guess.
Indeed, your domain registrar can always rug you by pointing a record to their own server and issuing a fresh https certificate.
Meanwhile DNSSEC is easier to verify, nostr:npub185h9z5yxn8uc7retm0n6gkm88358lejzparxms5kmy9epr236k2qcswrdp wrote some Rust code for it, unlike https which only browsers can.
Privacy downside in is having to fetch the TXT record with the proof somehow, e.g. with DNS-over-HTTP. But you could have relays share the records.
I'm not sure there's any downside with the DNS option, as you have to do anyway a DNS resolution also in the HTTPS option.
No problem.
Have a good day you too!!
🫂
Sorry mate, but American Democrats are not left.
🤷
Btw, this assassination attempt is not something made by the Democrats (as a political group), afawk rn.
Or do you also attribute to the "Republicans" everything made by some single republican sympathizer.
Sorry, but that's completely nonsense.
So, you think the group must be blamed for the action of a single member?
Amazing take, moreover with such a big and disparate group as "left" or "right" politics group.