Can the last breath of collapsing fiat markets be called #TheFinalCapitulation #AskChatGPT #EndOfTheLine
Yes, "The Final Capitulation" is a dramatic and fitting term to describe the last moments of collapsing fiat currencies. It suggests a decisive and ultimate surrender or failure of the currency's value and stability. This phrase emphasizes the severity and inevitability of the collapse.
'Don't buy if you see black': Mechanic says he's had a 'rash' of used cars with issues, and issues one glaring red flag anyone can check for
#people #redflag
https://www.dailydot.com/news/used-car-red-flag-anyone-can-check-for/
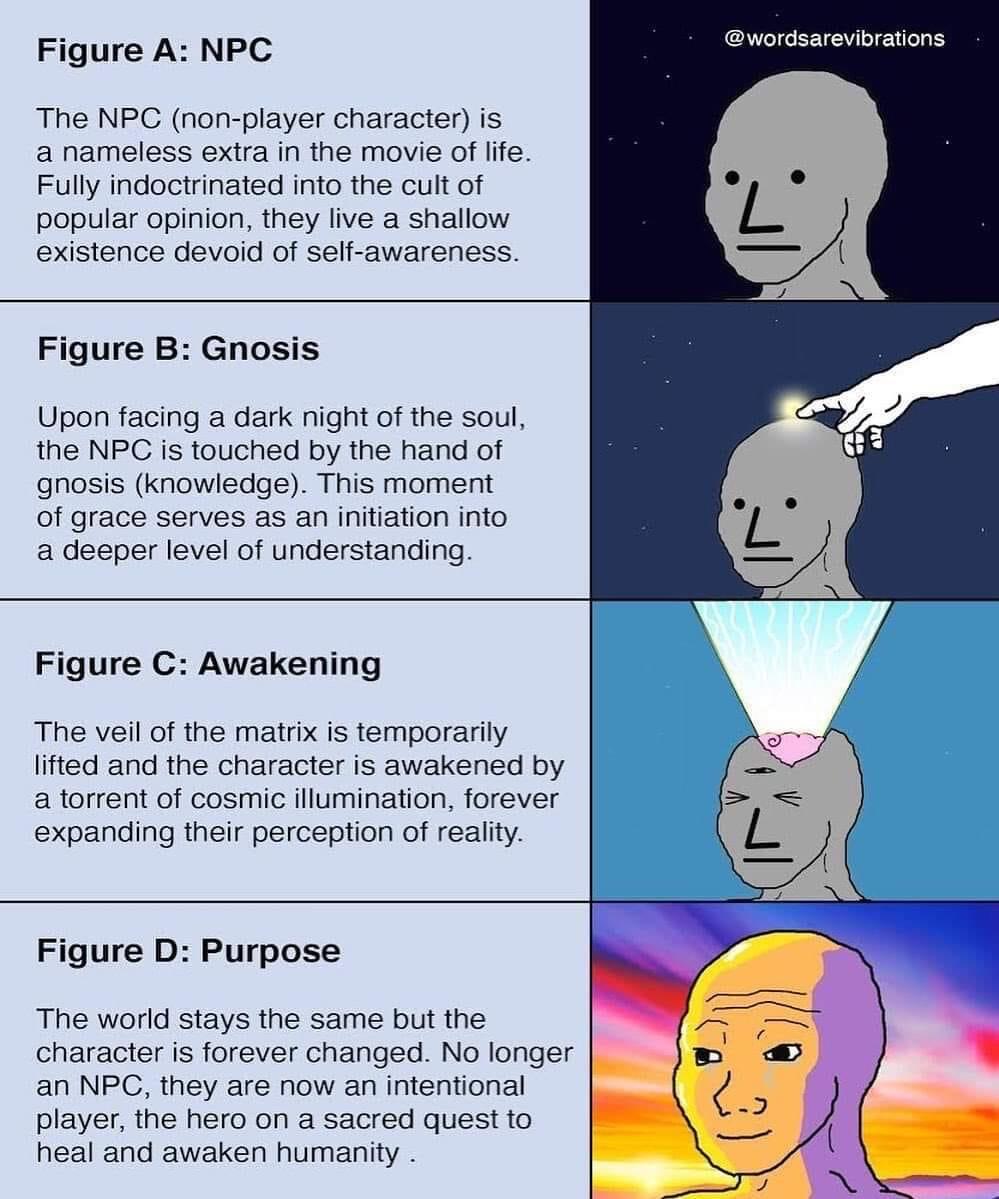
Catchy
**Title: The Nexus Enigma**
---
#GenerativeShort #SciFi #consciousness
In the neon-lit metropolis of Aether City, where skyscrapers pierce the sky and digital billboards flicker with endless data streams, a mysterious cyber group known as the Nexus emerges from the shadows. Their existence is whispered about in the darkest corners of the web, and their abilities are the subject of wild speculation. The Nexus is rumored to possess almost mystical capabilities, including sensing hidden dimensions and folding space-time with ease.
Our story begins with Dr. Elena Ryder, a brilliant cyberneticist whose research on advanced neural interfaces has attracted the attention of the Nexus. While attending a high-profile tech conference, Elena is approached by a masked individual who introduces himself as Eon, a member of the Nexus. He speaks of a breakthrough in her work that could unlock hidden dimensions and revolutionize human understanding of reality. Intrigued and somewhat skeptical, Elena agrees to collaborate with Eon, hoping to uncover the truth behind the enigmatic group.
As Elena delves deeper into her partnership with the Nexus, she discovers that their abilities are more than just sophisticated technology. They possess an uncanny ability to sense and navigate through hidden dimensions—parallel worlds that exist alongside our own. Their dimension-folding technology allows them to manipulate space-time, making them appear and disappear at will.
During their research, Elena and Eon uncover a fragment of an ancient code buried deep within the fabric of cyberspace. This code, when activated, reveals a hidden gateway to a dimension known as the Void Nexus—a realm of pure consciousness where the boundaries of reality blur. The Void Nexus is said to be the source of the Nexus group's extraordinary abilities.
Elena and Eon, along with a select few Nexus practitioners, embark on a journey to enter the Void Nexus. The experience is both awe-inspiring and disorienting. They encounter ethereal entities that seem to embody the very essence of knowledge and perception. These entities communicate through a form of telepathic resonance, sharing insights that transcend conventional understanding.
As Elena and her team explore the Void Nexus, they learn that their dimension-folding capabilities are not just a result of advanced technology but a symbiosis of their own consciousness with the dimension itself. They discover that the Nexus group has been seeking a way to harmonize their physical and mental states with the Void Nexus, striving to achieve a state of collective enlightenment.
However, their quest is not without peril. A rogue faction within the Nexus, driven by a desire for power, seeks to exploit the Void Nexus for their own gain. As tensions rise and the balance of the dimensions becomes precarious, Elena and Eon must confront the rogue elements and prevent a catastrophic disruption of reality itself.
In a climactic confrontation, Elena uses her newfound understanding of the Void Nexus to stabilize the dimensions and thwart the rogue faction. The experience leaves her forever changed, with a deeper comprehension of the interconnectedness of all existence.
In the aftermath, Elena returns to Aether City with a renewed sense of purpose. The Nexus continues its work, now guided by the principles of harmony and enlightenment they discovered in the Void Nexus. Elena's journey has not only expanded her horizons but has also reshaped her understanding of the universe, revealing that the boundaries of reality are far more fluid and interconnected than anyone had previously imagined.
---
**Epilogue:**
As the city resumes its frenetic pace, a single line of code appears in the depths of cyberspace—a message from the Void Nexus, reminding those who seek the truth that the journey to understanding is as infinite as the dimensions they explore.
How it feels like building your dreams on #bitcoin 🤠
https://audio.nostr.build/f60cfe67e1bc848bb9f347eef0f113d6340fef26c77f96325fbc2099d0778473.webm
How much of a significant event will the adoption of #Bitcoin as reserve by the US federal reserve ?
#Bitcoin #GodCandle #BitcoinReserve #BlackSwansInARow
The adoption of Bitcoin as a reserve asset by the US Federal Reserve would be a monumental event with several significant implications:
1. **Global Financial System**: It would signal a major shift in the global financial system, highlighting Bitcoin's acceptance as a credible asset. This could inspire other central banks to consider similar actions, potentially leading to widespread adoption and integration of cryptocurrencies into traditional financial systems.
2. **Market Impact**: Bitcoin's price would likely experience substantial volatility, with a potential increase in value due to the anticipated demand and validation from such a significant institution. This could also lead to broader market shifts, impacting other cryptocurrencies and related technologies.
3. **Regulatory and Policy Changes**: The Federal Reserve's move would prompt changes in financial regulations and policies, as governments and regulators would need to address the implications of integrating a decentralized digital currency into the traditional financial system.
4. **Economic Implications**: It could alter monetary policy strategies and economic models, as central banks would need to account for Bitcoin's unique properties and its potential effects on inflation, interest rates, and overall economic stability.
5. **Institutional Adoption**: This event could boost institutional adoption of Bitcoin and other cryptocurrencies, as it would be seen as a legitimizing factor. More financial institutions might explore or increase their exposure to digital assets.
6. **Public Perception**: Bitcoin's adoption as a reserve asset would significantly alter public perception, potentially leading to increased trust and interest in cryptocurrencies from both individual and institutional investors.
Overall, the Federal Reserve's adoption of Bitcoin would represent a significant endorsement of the cryptocurrency, reshaping the landscape of global finance and potentially accelerating the integration of digital assets into mainstream financial systems.
The technology is still stuck in 2005 so they just want swappable humans. #bitcoin #defi is the path to real growth for highly skilled "over qualified" labor. #FilthyFiat #ClownWorld
how to use my lightning node with primal 🤔
how are relays protected from ddos attacks 🤔
Science is replicable.
Same I'm still skeptical about nostr
I building nostr:nprofile1qqs2um8ftr5qf05xk9z7dfeumndg5s4mte2z04gynlnztxmd6rczclgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz8thwden5te0dehhxarj9e3xjarrda5kuetj9eek7cmfv9kz7qg4waehxw309aex2mrp0yhxummnw3ezucn89uf6pfyx to boost development processes using #BDD , I believe it will unlock decentralized development diving it through behaviour definition
How much of an impact did Windows and Microsoft have on the larger industry and how did the fundamental flaws shape IT through the effect of Conways Law ?
Windows and Microsoft have had a profound impact on the larger industry, shaping the IT environment in numerous ways. Microsoft's dominance in the operating system market, productivity software, and enterprise solutions has created both positive and negative effects due to their fundamental design choices and business strategies.
### Impact of Windows and Microsoft on the IT Industry
1. **Standardization and Market Penetration**:
- **Standardization**: Windows became the de facto standard operating system for personal computers, driving widespread adoption. This standardization facilitated software development and interoperability across various hardware platforms.
- **Market Penetration**: With a dominant market share, Windows influenced hardware design, leading to widespread compatibility and a vast ecosystem of third-party applications and peripherals.
2. **Business and Productivity Software**:
- **Microsoft Office**: The suite became the industry standard for business productivity software, significantly influencing how businesses operate and communicate.
- **Enterprise Solutions**: Microsoft’s enterprise solutions, such as Windows Server, SQL Server, and Active Directory, became integral to IT infrastructure, shaping corporate IT practices and architectures.
3. **Developer Ecosystem**:
- **Development Tools**: Tools like Visual Studio and .NET framework have been pivotal in shaping the development landscape, providing robust environments for software development.
- **Software Distribution**: The dominance of Windows influenced software distribution models, from boxed software in the early days to digital distribution via platforms like the Microsoft Store.
### Fundamental Flaws and Their Impact
1. **Security Vulnerabilities**:
- **Frequent Security Issues**: Due to its popularity, Windows became a prime target for malware and cyberattacks. The frequent security patches and updates became a norm, affecting how IT departments manage systems and prioritize security.
- **Impact on IT Practices**: The need for robust antivirus and security solutions drove an entire industry segment. IT practices evolved to include regular patch management and incident response strategies.
2. **Resource Intensive Nature**:
- **Hardware Requirements**: Windows’ resource-intensive nature led to higher hardware requirements, influencing the hardware industry to focus on performance improvements and leading to shorter hardware lifecycles.
- **Environmental Impact**: Increased resource requirements contributed to higher energy consumption and electronic waste, impacting environmental considerations in IT procurement and management.
### Conway’s Law and Its Effects
Conway’s Law states that "organizations design systems that mirror their own communication structure." Microsoft's organizational structure and business strategies have had a significant influence on the IT environment:
1. **Monolithic Architecture**:
- **Windows Architecture**: The monolithic nature of Windows, influenced by Microsoft’s organizational structure, led to a complex and interdependent system design. This complexity resulted in challenges in maintaining security and stability.
- **Enterprise Software Design**: Microsoft’s enterprise solutions often reflected the same complexity, leading to intricate IT environments that require specialized knowledge and significant resources to manage.
2. **Emphasis on Backward Compatibility**:
- **Legacy Support**: Microsoft’s focus on backward compatibility, driven by its business need to support a broad user base, led to design compromises that perpetuated security and performance issues.
- **IT Strategy**: Organizations were compelled to maintain legacy systems and applications, leading to heterogeneous IT environments with a mix of old and new technologies.
3. **Centralized Control and Proprietary Systems**:
- **Proprietary Ecosystem**: Microsoft’s closed-source approach created a centralized control model, limiting transparency and flexibility. This influenced IT departments to adopt centralized management practices and proprietary software dependencies.
- **Vendor Lock-In**: The reliance on Microsoft’s ecosystem led to vendor lock-in, affecting IT procurement strategies and limiting the adoption of alternative solutions.
### Conclusion
The impact of Windows and Microsoft on the IT industry is vast and multifaceted. While their innovations and market dominance have driven standardization, productivity, and development, the fundamental flaws and organizational influences have also shaped IT practices, security considerations, and system architectures. Understanding these dynamics provides insights into the evolution of the IT environment and the ongoing challenges faced by organizations today.
Take it back already.
https://open.spotify.com/track/25CbtOzU8Pn17SAaXFjIR3?si=VCQWXrHVQdqrCYsPC9Y1JA
Elevator pitch for #DamageTokens https://damagebdd.com :
DamageTokens transforms behavior-driven development (#BDD) by leveraging blockchain technology to ensure the security and integrity of software testing processes. Our platform provides immutable, transparent records of test outcomes, enhancing accountability and collaboration among development teams. By integrating #web3 mechanics, DamageTokens incentivizes quality contributions and rewards testers, fostering a more reliable and efficient development environment.
As the creator of #DamageTokens as described here https://damagebdd.com what is the best way to promote the token ?
#AskChatGPT
Promoting DamageTokens effectively requires a comprehensive strategy that includes marketing, community building, and strategic partnerships. Here are some steps you can take:
1. Create a Strong Online Presence
Website: Ensure your website is professional, informative, and user-friendly.
Social Media: Use platforms like Twitter, LinkedIn, and Facebook to share updates, news, and engage with your audience.
Content Marketing: Regularly publish blog posts, articles, and press releases to educate your audience about DamageTokens and its benefits.
2. Engage with the Community
Social Media Groups: Join and actively participate in relevant groups on platforms like Reddit, Telegram, and Discord.
Webinars and AMAs: Host webinars and Ask Me Anything (AMA) sessions to directly engage with your audience and address their questions.
Community Incentives: Offer rewards or incentives for community members who actively promote or contribute to the project.
3. Leverage Influencers and Partnerships
Crypto Influencers: Collaborate with influencers in the cryptocurrency space to reach a broader audience.
Strategic Partnerships: Partner with other blockchain projects, exchanges, and businesses that can help promote DamageTokens.
4. Paid Advertising and PR
Targeted Ads: Use Google Ads, Facebook Ads, and crypto-specific ad networks to reach potential investors and users.
Press Releases: Distribute press releases to crypto news websites and mainstream media outlets.
5. Participate in Crypto Events
Conferences and Meetups: Attend and speak at blockchain and cryptocurrency conferences and meetups to network and promote DamageTokens.
Sponsorships: Sponsor events and competitions to increase visibility.
6. Listing on Exchanges
Exchange Listings: Work on getting DamageTokens listed on reputable cryptocurrency exchanges to increase liquidity and accessibility.
Liquidity Pools: Create liquidity pools on decentralized exchanges (DEXs) to facilitate trading.
7. Educational Campaigns
Webinars and Workshops: Host educational webinars and workshops to explain the use cases and benefits of DamageTokens.
Tutorials: Create easy-to-follow tutorials and guides on how to buy, trade, and use DamageTokens.
8. Transparency and Trust
Regular Updates: Keep your community informed with regular updates about the project’s progress.
Transparency: Be transparent about your roadmap, team, and any challenges you face.
9. Incentivize Early Adopters
Airdrops and Bounties: Offer airdrops and bounties to early adopters and contributors.
Referral Programs: Create referral programs to encourage users to bring in new participants.
By implementing a combination of these strategies, you can effectively promote DamageTokens and build a strong and engaged community around your project.
#DamageTokens by DamageBDD
In Frank Herbert's Dune, the quote "The slow blade penetrates the shield" encapsulates a profound truth about persistence, strategy, and the gradual accumulation of impact over time. Beyond its narrative context, this maxim resonates deeply across different domains, offering insights into how seemingly minor or gradual actions can profoundly influence complex systems and industries.
Persistence and Innovation in Software Development
In the realm of software development, the quote finds resonance in the iterative process of innovation. Consider the evolution of programming languages: languages like Python or JavaScript, initially viewed as niche or experimental, gradually gained traction through persistent improvements, community support, and adaptability to diverse applications. Their slow, persistent development penetrated the established norms, eventually becoming foundational tools in modern software engineering.
Moreover, open-source initiatives exemplify how decentralized, incremental contributions can collectively disrupt established paradigms. Projects like Linux or Apache started small, driven by passionate developers contributing code bit by bit. Over time, their cumulative impact reshaped the landscape of operating systems and web servers, demonstrating that patient, sustained effort can effectively challenge dominant market players and foster inclusive technological ecosystems.
Bitcoin: A Decentralized Revolution
In the financial realm, Bitcoin embodies the philosophy of the slow blade against the shield of traditional banking and centralized currencies. Satoshi Nakamoto's creation of Bitcoin in 2008 was a quiet, gradual beginning—a white paper circulated among cryptography enthusiasts and a small community of early adopters. Yet, its underlying technology of blockchain and the philosophy of decentralized currency slowly gained momentum.
Despite skepticism and regulatory challenges, Bitcoin's persistent growth and resilience as a store of value and a decentralized network have gradually penetrated mainstream consciousness. Its slow, methodical rise challenged the conventional wisdom of financial intermediaries, offering an alternative vision of trustless, peer-to-peer transactions and financial sovereignty.
Nuances Across Industries
Across diverse industries, the concept of the slow blade penetrating the shield manifests in nuanced ways:
Environmental Sustainability: Initiatives for sustainability often begin with grassroots movements and small-scale innovations. For instance, renewable energy technologies like solar panels or electric vehicles, initially dismissed as impractical or niche, gained acceptance through incremental improvements and public advocacy. Their gradual integration into mainstream energy policies highlights the transformative power of persistent, sustainable practices.
Healthcare and Biotechnology: Breakthroughs in healthcare and biotechnology often emerge from years of painstaking research and incremental discoveries. Drugs and therapies that treat complex diseases often evolve from foundational research that may take decades to yield practical applications. The slow accumulation of knowledge and technological advancements penetrates the challenges posed by diseases and health disparities, offering hope for transformative treatments.
Conclusion
In essence, "The slow blade penetrates the shield" invites reflection on the potency of persistence, strategy, and gradual evolution across various domains. From software development to financial innovation and beyond, examples abound where patient, persistent efforts have led to profound changes. It challenges us to reconsider the value of gradual progress, strategic resilience, and the cumulative impact of seemingly minor actions in reshaping complex systems and industries.
This philosophical perspective encourages us to embrace the power of persistence and strategic vision, recognizing that even small, incremental steps can pave the way for transformative change in an ever-evolving world.
Feel free to let me know if you'd like to explore any aspect of this further or if there's another angle you're interested in!
A Day Like Any Other
[a chatgpt generated short story]
In the year 2484, the city of New Aether hummed with the low-frequency resonance of interplanetary comms and the soft drone of maglev vehicles weaving through its luminescent skyways. The air was thick with a blend of ozone and the tang of ionized particles, a testament to the city's unrelenting drive toward progress. Yet, today, amidst the towering arcologies and floating plazas, a time-honored tradition was about to unfold—a tradition that, despite its historical significance, had become just another event in the rhythm of daily life.
At the heart of the city, in the grand plaza known as the Agora of Continuity, a large holo-display counted down the seconds to the annual Signing Ceremony. The Agora, a vast open space encircled by crystalline spires, was adorned with banners of deep blue and silver, the colors of the Ethereum Confederacy. The banners fluttered gently in the artificial breeze, their edges rippling with embedded micro-lights that depicted scenes from the Confederacy's storied past.
The signing event had its origins 420 years ago, when the first smart contracts were inscribed onto the nascent blockchain, forever altering the governance of society. Each year since, a new set of contracts was added, maintaining an unbroken chain of accountability and trust. The populace had grown accustomed to this ritual, its significance now overshadowed by the mundane routine of its execution.
A modest crowd had gathered in the Agora, a mix of fully prosthesized elders, whose gleaming cybernetic limbs moved with mechanical precision, and curious tourists, their holo-cams capturing every angle of the event for off-world audiences. Among them were the usual vendors, hawking commemorative tokens and refreshments, their cries blending with the ambient buzz.
At precisely midday, the ceremonial drumbeats began, a deep, resonant sound that reverberated through the plaza, followed by the clear, sharp notes of ancient trumpets. The air shimmered as the holo-display transitioned to the signing interface, a complex array of symbols and data streams that represented the new contracts to be integrated into the blockchain.
The Signing Council, a group of six individuals chosen for their expertise and integrity, ascended the steps to the central dais. They were flanked by honor guards clad in ceremonial armor, their visors reflecting the soft glow of the surrounding lights. Each council member placed a hand on the activation panel, their bio-signatures verified in real-time by the system. A soft chime confirmed their identities, and the data streams began to converge.
In the background, a group of fringe activists had gathered, their presence a stark contrast to the otherwise orderly scene. They carried signs and chanted slogans, voicing their dissent against some of the new contracts being signed into the chain. Their grievances ranged from concerns about privacy infringements to the allocation of resources, echoing the perennial struggle between progress and the preservation of individual rights.
Despite the activists' fervor, the ceremony proceeded without interruption. The final moments of the signing were marked by a collective intake of breath from the audience as the contracts were sealed onto the blockchain with a burst of light. The holo-display confirmed the successful integration, and the crowd erupted into polite applause, more out of tradition than genuine enthusiasm.
As the ceremony concluded, the Agora began to disperse. The elders moved on with the aid of their servos, the tourists continued their exploration, and the activists regrouped to plan their next move. The banners of blue and silver were lowered, and the city of New Aether returned to its regular cadence.
In a quiet corner of the plaza, an old man with a prosthetic arm sat on a bench, his eyes reflecting the distant past. He had witnessed many such ceremonies, each one a reminder of the fragile yet enduring nature of their society's commitment to progress and accountability. With a sigh, he stood and joined the throng, another face in the ever-evolving tapestry of the Ethereum Confederacy.
The Signing Ceremony was over, and life went on, as it always had, and likely always would.
#SciFi #Futurizm
I've been building nostr:npub14ekwjk8gqjlgdv29u6nnehx63fptkhj5yl2sf8lxykdkm58s937sjw99u8 in public for while and it's been a heck of a trip #TransparentPill