Hier alternativ ein kleines Tool, das dabei hilft:
Die RootCA kannst du vermutlich sogar weg lassen, da eigentlich alle grösseren RootCAs im Store sein sollten. Wichtig ist die SubCA/Intermediate CA.
—–BEGIN CERTIFICATE—–
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
—–END CERTIFICATE—–
Du kannst dir die CA + SubCA von dem Aussteller (sehe es den Aussteller jetzt leider nicht mehr) als base64(!!!) herunterladen via Texteditor öffnen, kopieren und alle kodierten Zertifikate nacheinander in einem pem/crt-File abspeichern.
Erst das Serverzert, dann etwaige SubCAs, dann die RootCA.
Sieht dann am Ende so aus:
—–BEGIN CERTIFICATE—–
....
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
....
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
....
—–END CERTIFICATE—–
Versuch mal die komplette Certchain hochzuladen und nicht nur das Serverzertifikat. Kommt auf den jeweiligen Browser bzw das Gerät an, ob die CA installiert ist.
https://www.ssllabs.com/ssltest/analyze.html?d=relayted.de&s=87.106.216.189&hideResults=on&latest
Women playing stupid games end up winning stupid prizes.
"Centralized institutions": ...
" We":
This is lies, OUR trust in you is broken, WE will make you obsolete
Thank you Nicolas Dorier and all contributors to freedom tech. WAGMI
#cashu #ecash #bitcoin #nostr #pubky #pkdns #privacy
GM
Look like nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 is avoiding opinions he disagrees with on his podcast, so which one should I go on instead to talk about hardware wallet issues? 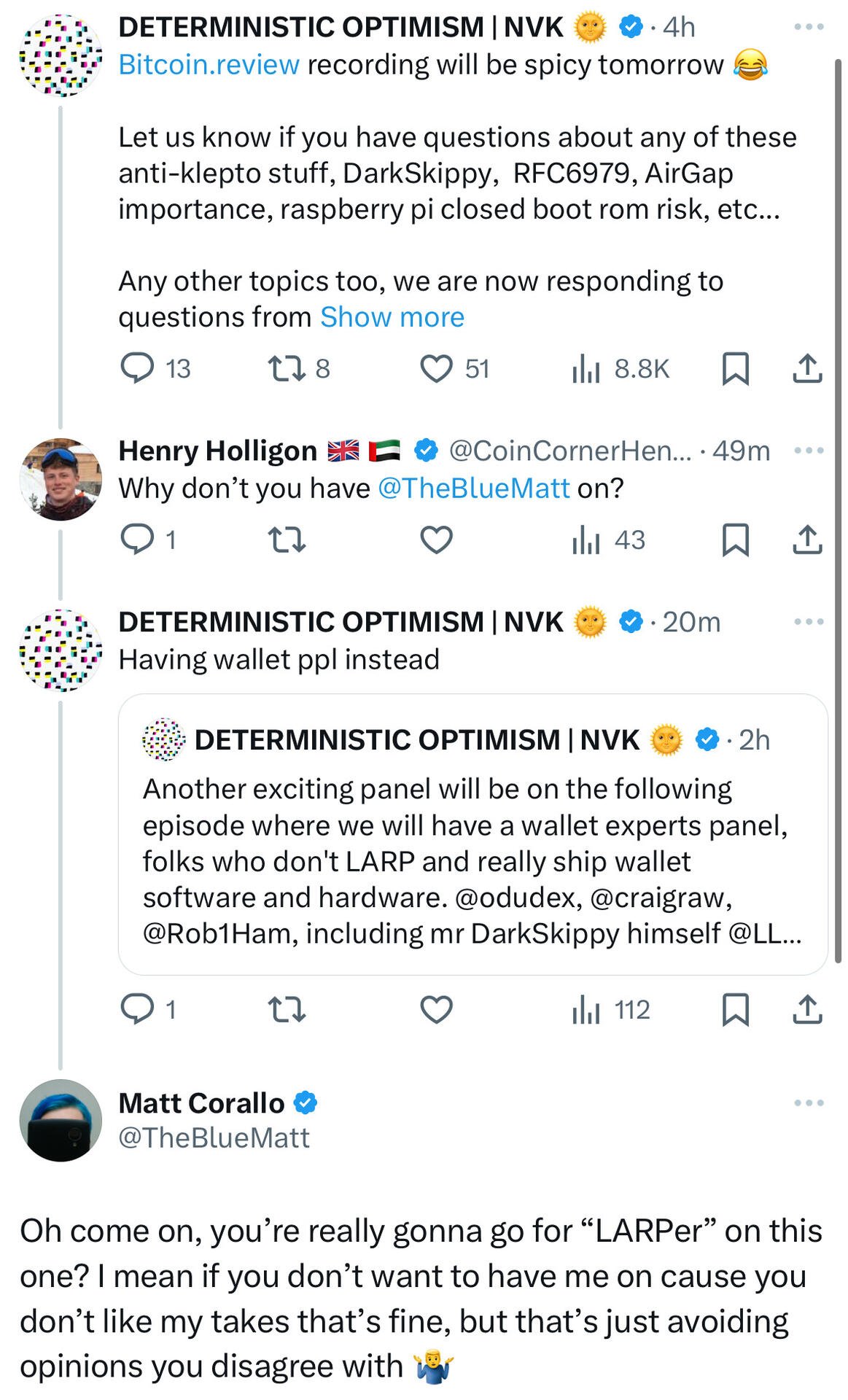
Sorry but you're acting like a drama queen. He explained everything in a few tweets. (I haven't listened to the Podcast)
NO ONE will use this attack vector, if there are better options. If you infiltrate the supply chain you wouldn't try to compromise the signing algorithm, you would directly go to i.e. seed creation. There will never be 100% security and fixing this issue won't change anything, because you open up new attack vectors... I don't understand why you are so focused on this and what you try to prove here...
Einer der besten Artikel, die ich bisher zu dem Thema gelesen habe und zudem von der Berliner Zeitung! Ich bin schwer beeindruckt!
Tour zum Chämtner Tobler und zur Rosinli Beiz
Matthäus 5:43-44 Hfa
[43] Es heißt bei euch: ›Liebe deinen Mitmenschen und hasse deinen Feind!‹ [44] Doch ich sage euch: Liebt eure Feinde und betet für die, die euch verfolgen!
Ledger phishing scam was just an ordinary phishing campaign with leaked emails IMO.
This one looks much more sophisticated, because you really cannot tell if phishing or not beside the links inside a mail.
Have seen the same coming from booking.com a week ago that happened to my parents. They received a phishing mail from their servers. (Verify credit card with a phishing link). Seems to be a new schema to compromise the mail infrastructure and to send "real Mails"
Here is an extract of the mail my parents received:
ARC-Authentication-Results: i=1; mx.google.com;
dkim=pass header.i=@booking.com header.s=bk header.b=qg05XoWJ;
spf=pass (google.com: domain of noreply@mailer.booking.com designates 37.10.30.4 as permitted sender) smtp.mailfrom=noreply@mailer.booking.com;
dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=booking.com
Return-Path:
Received: from mailout-202-r3.booking.com (mailout-202-r3.booking.com. [37.10.30.4])
by mx.google.com with ESMTPS id m18-
Not if spf=pass, dkim=pass, dmarc=pass. These mails were send from the trezor mail servers.
looks like phishing mails from the real trezor mail servers. spf, dkim, dmarc=pass means it's verified that they are send from their own servers.
