I adjusted my relays with the Amethyst client. Maybe that will help.
Why is it that often when I use a webclient for Nostr I have trouble
making posts or liking? I am using Mullvad but I wouldn't think that
would matter. I'm also using Firefox and Linux. #asknostr
Even making this post the send button wouldn't work. I had to refresh Coracle.
nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsw3u8v7rz83txuy8nc0eth6rsqh4z935fs3t6ugwc7364gpzy5pscyda538 Can you add NIP-46 login for bitcoinmints.com? That is the NIP nsec.app uses right?
Nostr Wallet Connect is badass! I can use cashu.me with my mint and zap using my own funds! #cashu #bitcoin #nwc
Aqua is getting good for payments with some of the new updates. Aqua uses the second layer lightning network and Liquid sidechain on bitcoin. By using both it makes it easier to use both the lightning network for payments, but also store bitcoin easily on Liquid temporarily before deciding to move a lot of bitcoin to a more secure and permanent location. https://www.nobsbitcoin.com/aqua-wallet-v0-2-0/
An address starting with a '3' probably is some kind of multisig. I wonder why they didn't use bech32.
🤣 funny.
I troll them back saying crypto is boring. Im interested in finding a girlfriend and having a family. What is so exciting about money anyway?!
I keep asking them more about themselves and if they want me. I don't tell them anything about myself at all!
I think GraphineOS strips metadata from pictures when taking the pictue.
For vanilla Android Im not sure. Sometimes I have used another app like Signal to send and image to myself. I think apps like Signal will remove meta data when they are compresses. I sure hope they do!
Yeah. The lightning channels can be configured to take a fee on each deposit and withdraw. That's an honest way.
One could also rugpull after running a mint for awhile by turning off their mint and taking all the SATs in the lightning channels. So, be careful which mints you trust!
Where is a place on Nostr to comment on something Eric said?
Holding bitcoin could be seen as a service or businesss. Holding and hopefully selling, lending or using as colateral for a profit.
I don't follow why holding bitcoin is high time preference. Compared to what?
#bitcoin
Don't forget about Cheapair.com. They have been accepting bitcoin for a long time and even have their own BTCpay Server to accept bitcoin.
Where is the secret stored? I don't understand how oauth is being used.
I'm implementing full disk encryption on my computers.
Finally! Signal usernames! https://www.signal.org/blog/phone-number-privacy-usernames/
nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv
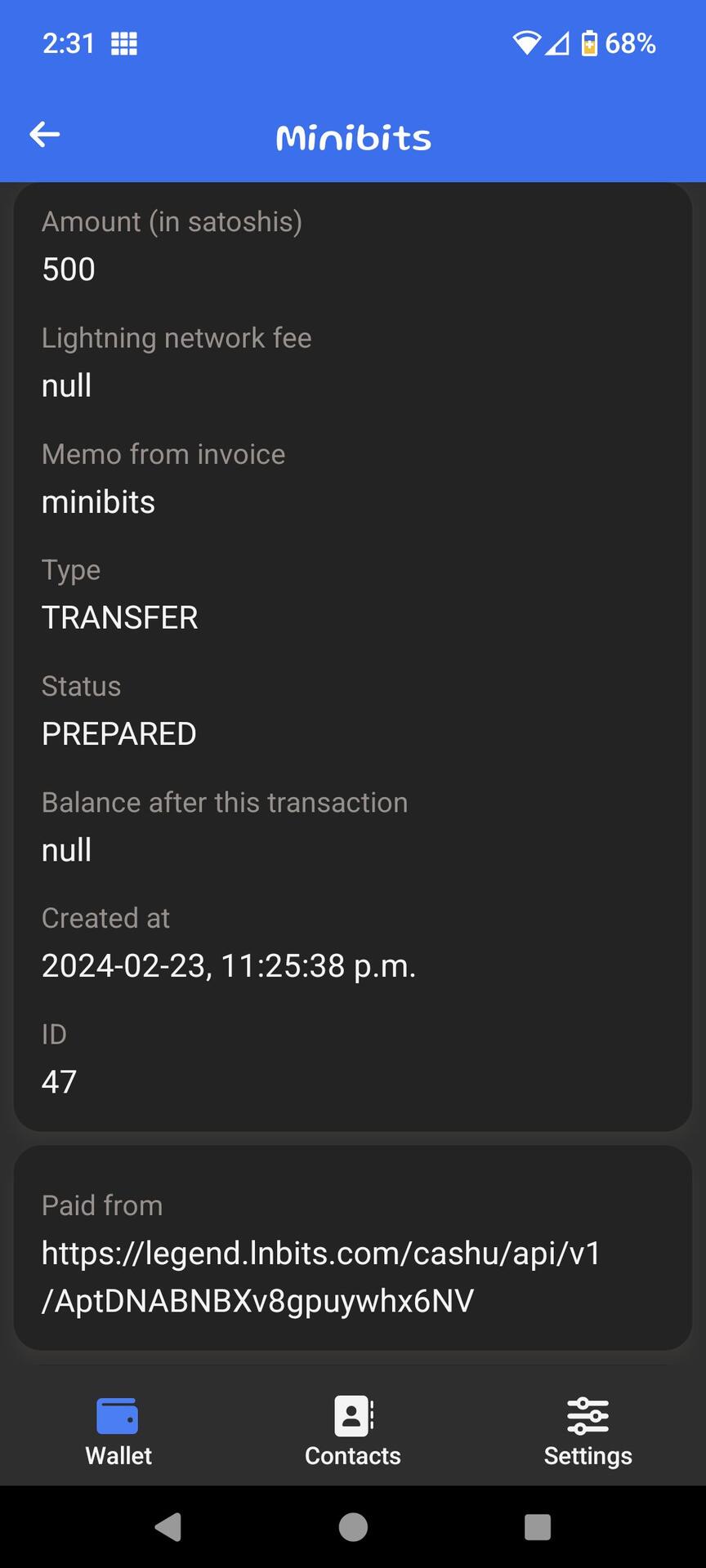
I'm not sure. Best to ask in the Minibits Telegram chat as these clients are under active development. GL
I'm jealous of you bitcoin celebrities getting nutted on all the time from zaps. 😳
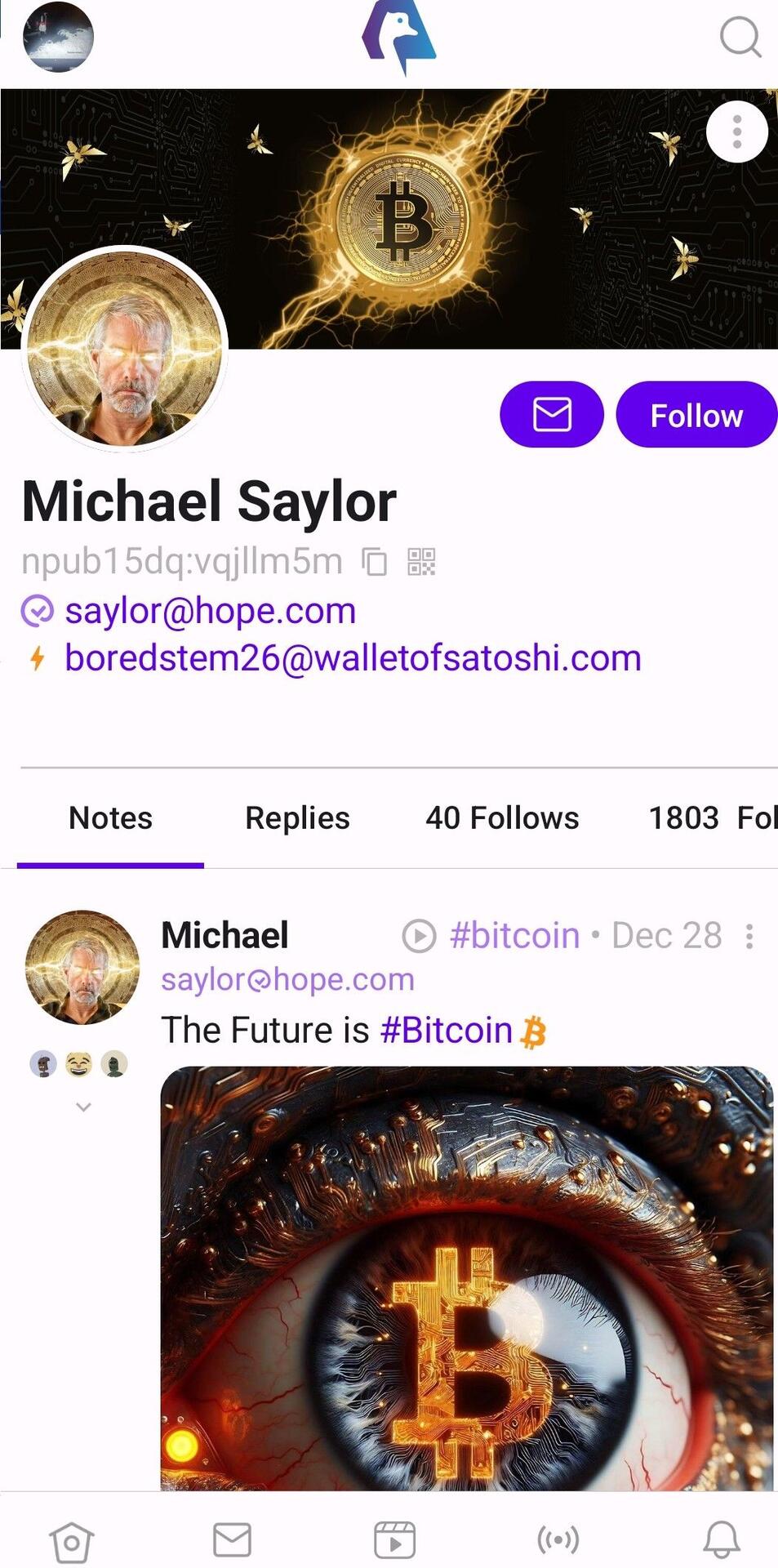
I believe it is legit. Hope.com is Saylor's domain.
This is your periodic reminder to install Amethyst (and all other Nostr clients) through Obtainium instead of Google's PlayStore.
You not only receive faster updates (the PlayStore is currently 4 versions behind) but you also start the process of freeing yourself from your invisible digital overlords.
Just follow this video: https://cdn.satellite.earth/2bd7e308c1797d64fca09b1d61e9bde24c68dd45e501c7383eff1e85392df11f.mp4
I've been installing APKs like a caveman!
I have never heard of Tangem or Safepal. If you can get the seed of those wallets you can import in into Electrum or Sparrow to do the CPFP. Im not sure if Blue Wallet does CPFP.
Flare.pub is like YouTube
No, I'll just take a shower and hope I don't smell like onions.
Just drink water.
nostr:npub1mutnyacc9uc4t5mmxvpprwsauj5p2qxq95v4a9j0jxl8wnkfvuyque23vg I have pending transactions which I'm worried are going to cause a force closure.
What can I do about that?
The first pending transaction is expired if I try to pay from Zeus. The other three I paid from Zeus but they still say pending on Mutiny.
I need to try Rust. I have used Haskell for years. When would Rust be more appropriate over Haskell, in your opinion?