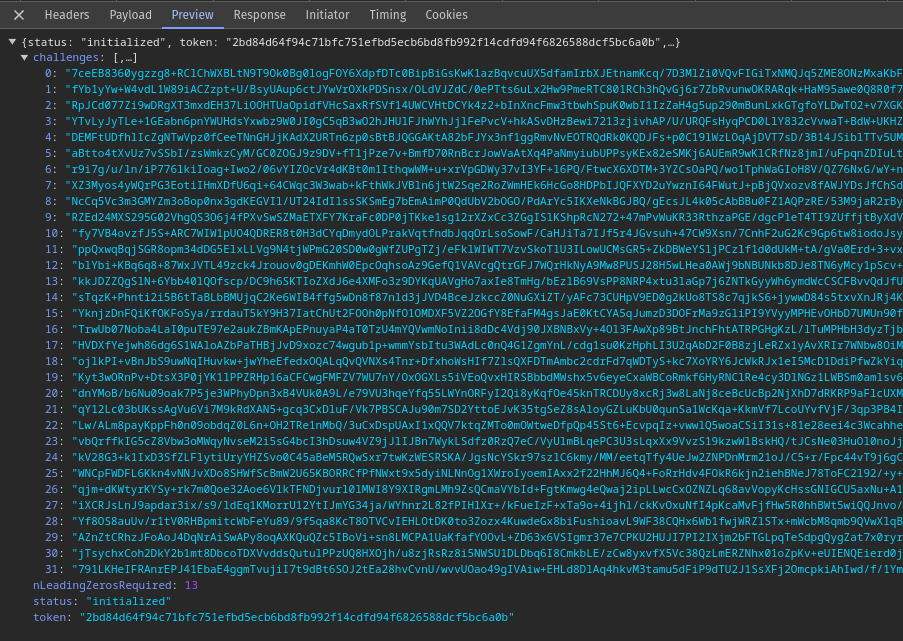
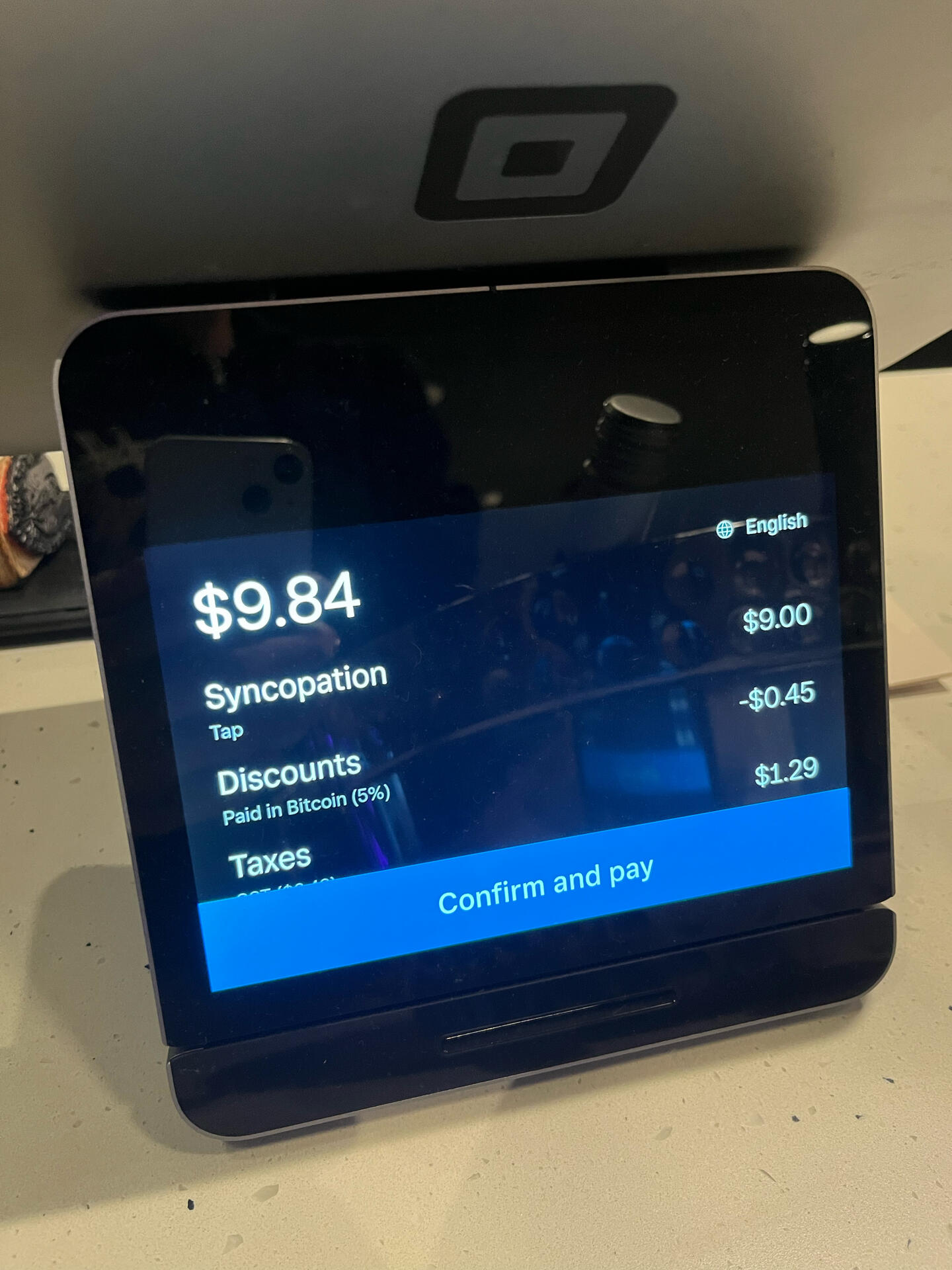
Oh, this is nice. I would still assume anything not running locally could leak somewhere, but this is a compelling architecture. (* Even things that run locally can leak if you aren't careful) nostr:note1xrnn9h9rt0t7tsx9uxxxplmj8m4al9atgulhz28vkqujutmqxd6s3qjyy2
Engineers that don't believe in "conspiracy theories" sadden me. Tell me that you don't want to know. Tell me that you're trying to fit in. Tell me it's your choice. Don't tell me that you accept conjecture over evidence and math, that's just poor engineering.
JSON should be required, but there's nothing wrong alternative encodings
People believe what they want to believe. There's serious medical advancements in healing a gunshot wound in two weeks with no scar though.
Not as interesting as whatever made his ear heal that fast.
whisper-cpp can transcribe audio at ~10x realtime on an Apple M2
If you have a decent PC, you can have surprisingly good experiences with a $200 Quest 2. I started playing VTOL VR as a "kids flight sim", and although it's a little heavy for the kids the experience of learning technical skills in modern VR is amazing. Doubly so when you have two people in the same aircraft.
Interesting breakdown! I usually work across these sections in a descending ratio of effort to likelihood of elimination:
Fast:
- Tone detection: Not definitive, but sets expectations.
- Logical fallacies: Most things fail here.
- Clarity: Similar to fallacies, people like making overly broad statements that don't mean anything.
- Check claims: This is often easy these days.
Slow:
- Context: If I don't understand it, I won't be able to evaluate it further.
- Arguments: The real meat, and where most of the time will be spent (if if hasn't failed already)
- Bias detection: Again not definitive, but can be easy to evaluate once you've made it this far.
- Assumptions: The second heaviest step.
- Source: Is almost an afterthought. "Reputable" sources make bad arguments all of the time. "Seedy" sources make good arguments more often than you expect. Source is often more related to bias than correctness. nostr:note1yck6mfk69tfj5lxusgqk2slkvxwh0a0uteej32r626gdtt7qslmsnusejk
“Those who manipulate this unseen mechanism of society constitute an invisible government which is the true ruling power of our country.”
This is why the only reasonable use for blockchains is a fungible cryptocurrency: the chain can only provide consensus, and the only meaningful value of a coin can be the global desire for fractional ownership of the whole system.
If you try to add special meaning to specific tokens, that needs to be enforced both in code and law. This favors those who control the software over other participants, and ultimately relinquishes sovereignty to whichever State the effect is supposed to happen in. Once control has been ceded to the State it becomes obvious that the blockchain provides no value beyond a simple Merkle tree, and since the State is the only real sovereign actor, they'll prefer to use a database that they have full control over.
#OnlyBitcoin
Science without skepticism is religion
Interpretations of quantum mechanics are like compiler errors in that hip new academic programming language that you're trying to learn. Sure they're technically consistent, but they're also oddly constructed and you can't help but wonder whether the system is a little too fancy for its own good. Maybe if you spent a couple decades understanding it you could figure out how to fix their mistake, but since only fanboys are going to spend that kind of time, you to do that you just hold your nose and work on things that matter.
🤔 nostr:note1qnjjezqtnvyucqff9853m46f80acy3g0keqterede9xt80rt4dlscvlefw
ReplyGuy was pretty annoying.
Wait until the first client exploit that burns half of nostr's nsecs. Without subkeys or another separation of identity and authentication, the web of trust would burn to the ground.
I have a hard time reconciling the availability of things socially with the availability of them adversarially. Yes, we have delete and edit and maybe expiring uploads ... for friendly participants. But not all participants are friendly, and retraction is a powerful signal that can reveal weaknesses.
Eric Schmidt, while CEO of Google, said the quiet thing very loudly:
"If you have something that you don't want anyone to know, maybe you shouldn't be doing it in the first place."
I can't tell if he said this for the right or wrong reasons, but it only gets truer. Be aware of the durability of your messages. As Earl Long said:
"Don't write anything you can phone.
Don't phone anything you can talk.
Don't talk anything you can whisper.
Don't whisper anything you can smile.
Don't smile anything you can nod.
Don't nod anything you can wink."
GM
"Show me the incentive and I'll show you the outcome" - Charlie Munger