Trust-minimized Zaps that are verifiable by everyone… I think I’ve found a way to do it. An attacker can still fake Zaps to themselves, but they can’t fake Zap honest recipients — and the proofs never expire.⚡️
Compatible with BOLT12 or LNURL, all a user needs is a normal lightwallet to verify Zaps. #[0] 🌲
Initially, I thought ION allowed unique URL registration like (did://bob.com), but Daniel clarified that it generates IDs in the format: "ChosenWord-RandomWord-RandomWord" (e.g., "Colby-Purple-Bee").
These trust-minimized IDs are more memorable than npubs or Bitcoin addresses and could function as usernames or domains atop Bitcoin.
Daniel and I discussed Web5 and Nostr 2.0 as co-protocols:
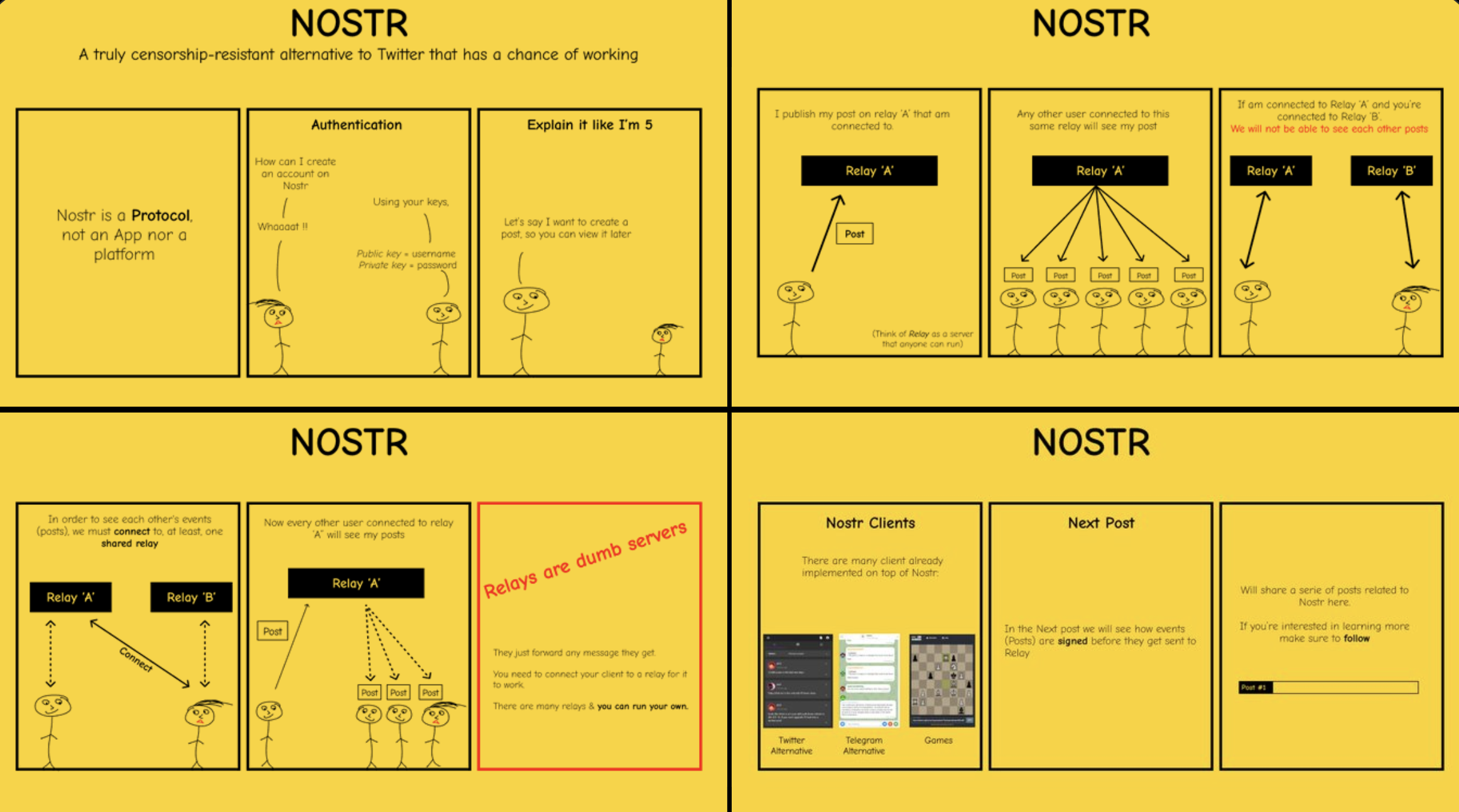
• Nostr 2.0 provides hosting for websites across hundreds of untrusted relays without the risks of content tampering, thanks to a tamper-evident Merkle root that's on-chain.
• Web5 enables self-hosting websites across local devices. This combination offers the best of both worlds: decentralized hosting with Nostr 2.0 and local self-hosting with Web5.
𝐾𝑒𝑦 𝑝𝑜𝑖𝑛𝑡𝑠 𝑓𝑟𝑜𝑚 𝑜𝑢𝑟 𝑑𝑖𝑠𝑐𝑢𝑠𝑠𝑖𝑜𝑛 𝑜𝑛 𝑁𝑜𝑠𝑡𝑟 𝟐.𝟎 𝑎𝑛𝑑 𝑊𝑒𝑏𝟓 𝑎𝑠 𝑐𝑜-𝑝𝑟𝑜𝑡𝑜𝑐𝑜𝑙𝑠:
1. Web5 allows website owners to self-host websites locally with decentralized domains, while Nostr 2.0 enables distributed hosting across hundreds of untrusted relays. This offers flexibility depending on the owner's needs.
2. Web5 provides resilient backup solutions for users decentralizing their website with Nostr 2.0, ensuring local copies across their trusted devices.
3. Web5 facilitates direct, encrypted communication between website owners and users. Visitors can browse decentralized websites hosted on many Nostr 2.0 relays and establish a direct connection with the website owners through Web5, all thanks to using the same DID system for domains.
We encourage the Web5 TBD team to develop an ION middlelayer for Nostr 2.0, making ION a middlelayer similar to the decentralized GitHub we are building for the bounty started by #[7]
This modular structure means the Nostr 2.0 base layer for storage ossifies into a standard. This encourages people to build new middlelayers and a diversity of clients for each middlelayer atop the universal, hash-organized off-chain storage. 🧱
Unlike IPFS, Nostr 2.0 lets people browse and verify websites without hosting them. Users don’t need to rely on public IPFS gateways to verify the data either — thanks to the on-chain Merkle roots Nostr 2.0 utilizes for syncing any off-chain data, identical to the type of on-chain Merkle roots ION uses. We aimed for the same Merkle DAGs and content addressing standards that ION already uses in order to be interoperable.
Most importantly, making all Nostr 2.0 nodes become ION nodes offers a significant advantage: When users type in a DID URL into a browser, the conjoined node would resolve the URL and deliver the tamper-evident website files to the user. 🖖
Replacing IPFS with Nostr 2.0 achieves this all-in-one package for a decentralized web powered by Bitcoin, where users can resolve URLs and browse decentralized websites through one type of modular node. If hundreds or thousands of operators run this conjoined node (Nostr 2.0+ION+Bitcoin full-node), the decentralized web becomes a reality. Anytime they want to host specific Twitter profiles or a GitHub repo, they simply add those middlelayers to their node stack and configure their hosting preferences.
🐝
Good quote.
“This paired with the high likelihood that ION DIDs will almost always be resolved by ION nodes instead of clients/light wallets manually doing what an ION node does for you sort of nullifies / diminishes the censorship resistance provided by the anchor to Bitcoin.”
Thanks Moe.
We cannot rely on a prevalence of honest ION nodes as a form of security because it creates the risk of an ION Sybil attack. The proof a user receives must prove that the URL is not registered to anyone else, like it does in ENS.
Unlike ENS, an ION node could omit previous registrations of a custom URL and deliver valid proofs of a new on-chain registration. This means an attacker could perform URL spoofing on users with a mere ION node Sybil attack and a few bitcoin transactions, unlike the extremely costly 51% attack required for URL spoofing in ENS.
In ENS, full-nodes can’t perform this trick without launching a 51% attack because users receive a Patricia-Merkle proof from full-nodes that verifies the current state of the domain registry. ION trade-offs aren’t worth the risks.
🥹 eureka..
⛓️🐝🔮🤫
Collapses lead to people begging for safety. That desperation might be used as leverage to consolidate government-controlled banking more than ever before.
DIDs as URLs will be needed for a decentralized web, but I have some concerning doubts about ION.
1. ION uses IPFS. Nostr 2.0 will replace IPFS for off-chain data storage. IPFS is clunky software that forces users to spin up a node to verify data, killing the user-server model that we're trying to decentralize with Nostr. Proof of this requirement in IPFS is in the quote below.
https://decrypt.co/resources/how-to-use-ipfs-the-backbone-of-web3
“Brave gives you the option to access IPFS content through a public gateway or 𝘵𝘩𝘳𝘰𝘶𝘨𝘩 𝘺𝘰𝘶𝘳 𝘰𝘸𝘯 𝘭𝘰𝘤𝘢𝘭 𝘯𝘰𝘥𝘦—𝘵𝘩𝘦 𝘭𝘢𝘵𝘵𝘦𝘳 𝘰𝘱𝘵𝘪𝘰𝘯 𝘪𝘴 𝘧𝘰𝘳 𝘵𝘩𝘰𝘴𝘦 𝘸𝘩𝘰 𝘸𝘢𝘯𝘵 𝘵𝘰 𝘷𝘦𝘳𝘪𝘧𝘺 𝘤𝘰𝘯𝘵𝘦𝘯𝘵 𝘭𝘰𝘤𝘢𝘭𝘭𝘺.”
In Nostr 2.0, user light wallets can verify data with on-chain Merkle proofs without needing to spin up an IPFS node or Nostr node. This advancement addresses some of the resource-intensiveness associated with IPFS and can help improve the user experience and scalability of decentralized web applications.
2. Light wallet users verifying a custom URL on ION doesn't seem as secure as light wallet users doing so via an ENS registry. To my knowledge, ION doesn't support custom domains yet; this might be why.👇🧵
The ENS registry lets user light wallets verify the state of the on-chain domain registry smart contract with a Patricia-Merkle proof that prevents duplicate registration of domains. This way, light wallet users can't be tricked into resolving a domain to the wrong IP.
ION, on the other hand, verifies domains through a normal Merkle proof, but light wallet users can be tricked because an ION node could modify their ION software and deliver a Merkle proof to users showing a new on-chain registration of an already registered domain.
𝘛𝘩𝘦 𝘐𝘖𝘕 𝘯𝘰𝘥𝘦 𝘤𝘰𝘶𝘭𝘥 𝘪𝘨𝘯𝘰𝘳𝘦 𝘢 𝘱𝘳𝘦𝘷𝘪𝘰𝘶𝘴 𝘳𝘦𝘨𝘪𝘴𝘵𝘳𝘢𝘵𝘪𝘰𝘯 𝘰𝘧 𝘵𝘩𝘦 𝘤𝘶𝘴𝘵𝘰𝘮 𝘥𝘰𝘮𝘢𝘪𝘯, 𝘯𝘰𝘵 𝘥𝘦𝘭𝘪𝘷𝘦𝘳 𝘢 𝘔𝘦𝘳𝘬𝘭𝘦 𝘱𝘳𝘰𝘰𝘧 𝘰𝘧 𝘪𝘵 𝘵𝘰 𝘵𝘩𝘦 𝘶𝘴𝘦𝘳, 𝘢𝘯𝘥 𝘵𝘩𝘦 𝘭𝘪𝘨𝘩𝘵 𝘸𝘢𝘭𝘭𝘦𝘵 𝘶𝘴𝘦𝘳 𝘸𝘰𝘶𝘭𝘥 𝘯𝘦𝘷𝘦𝘳 𝘬𝘯𝘰𝘸. 𝘚𝘪𝘯𝘤𝘦 𝘭𝘪𝘨𝘩𝘵 𝘸𝘢𝘭𝘭𝘦𝘵 𝘶𝘴𝘦𝘳𝘴 𝘥𝘰𝘯'𝘵 𝘩𝘢𝘷𝘦 𝘢 𝘗𝘢𝘵𝘳𝘪𝘤𝘪𝘢-𝘔𝘦𝘳𝘬𝘭𝘦 𝘱𝘳𝘰𝘰𝘧 𝘵𝘰 𝘷𝘦𝘳𝘪𝘧𝘺 𝘵𝘩𝘦 𝘴𝘵𝘢𝘵𝘦 𝘰𝘧 𝘵𝘩𝘦 𝘳𝘦𝘨𝘪𝘴𝘵𝘳𝘺, 𝘵𝘩𝘦𝘺'𝘳𝘦 𝘫𝘶𝘴𝘵 𝘳𝘦𝘭𝘺𝘪𝘯𝘨 𝘰𝘯 𝘵𝘩𝘦 𝘧𝘢𝘤𝘵 𝘵𝘩𝘢𝘵 𝘵𝘩𝘦 𝘔𝘦𝘳𝘬𝘭𝘦 𝘳𝘰𝘰𝘵 𝘰𝘧 𝘵𝘩𝘦 𝘱𝘳𝘰𝘰𝘧 𝘪𝘴 𝘰𝘯-𝘤𝘩𝘢𝘪𝘯 𝘧𝘰𝘳 𝘵𝘩𝘦𝘪𝘳 𝘥𝘰𝘮𝘢𝘪𝘯 𝘷𝘦𝘳𝘪𝘧𝘪𝘤𝘢𝘵𝘪𝘰𝘯 — 𝘵𝘩𝘢𝘵 𝘪𝘴𝘯'𝘵 𝘦𝘯𝘰𝘶𝘨𝘩.
An ION node could deliver a valid Merkle proof showing the data is on-chain while omitting the previous registration. Since the user doesn't have the ability to verify if the registry rejected the domain registration entry in ION, it is vulnerable to this omission attack — unlike the ENS registry, where light wallet users can verify if the ENS registry rejected the custom URL by checking the state of the ENS smart contract with Patricia-Merkle trees. Light wallet users don't have the luxury of a Patricia-Merkle tree in ION, so they don't get the same level of verification.
This is likely why ION does not support custom URLs.
The normal internet started with IP addresses, then custom domains came afterward. It seems like a wise route to follow for now, as current solutions for custom URLs on Bitcoin are inadequate. Bitcoin addresses will be our URLs for now, like IPs in the early '80s.
I'd appreciate anyone skilled in DID URLs responding #[1] #[2] and proving me wrong if I am. ION is indeed complicated, and now I understand why #[3] and #[4] complain about it as a standard.
Clever idea for sharing keys in person. #[2]
It can also improve the security of websites because anytime a hacker inserts a foreign file, he’ll change the hashes of the website… the user or node will automatically detect that it doesn’t match the Merkle Root in the website author’s original bitcoin transaction.
Websites are stored as Merkle DAGs, so all websites become tamper-evident. It solves security, trust, and distributed hosting issues of the normal web.
Nostr 2.0 is far more than DID key delegation… it will extend nostr to webapps where DIDs are the URLs.
It’s a tamper-evident web where anyone can host your website without needing to trust them, effectively decentralizing all websites with Nostr. Native apps are great too, but we have a great opportunity to decentralize the web here.
#[0]