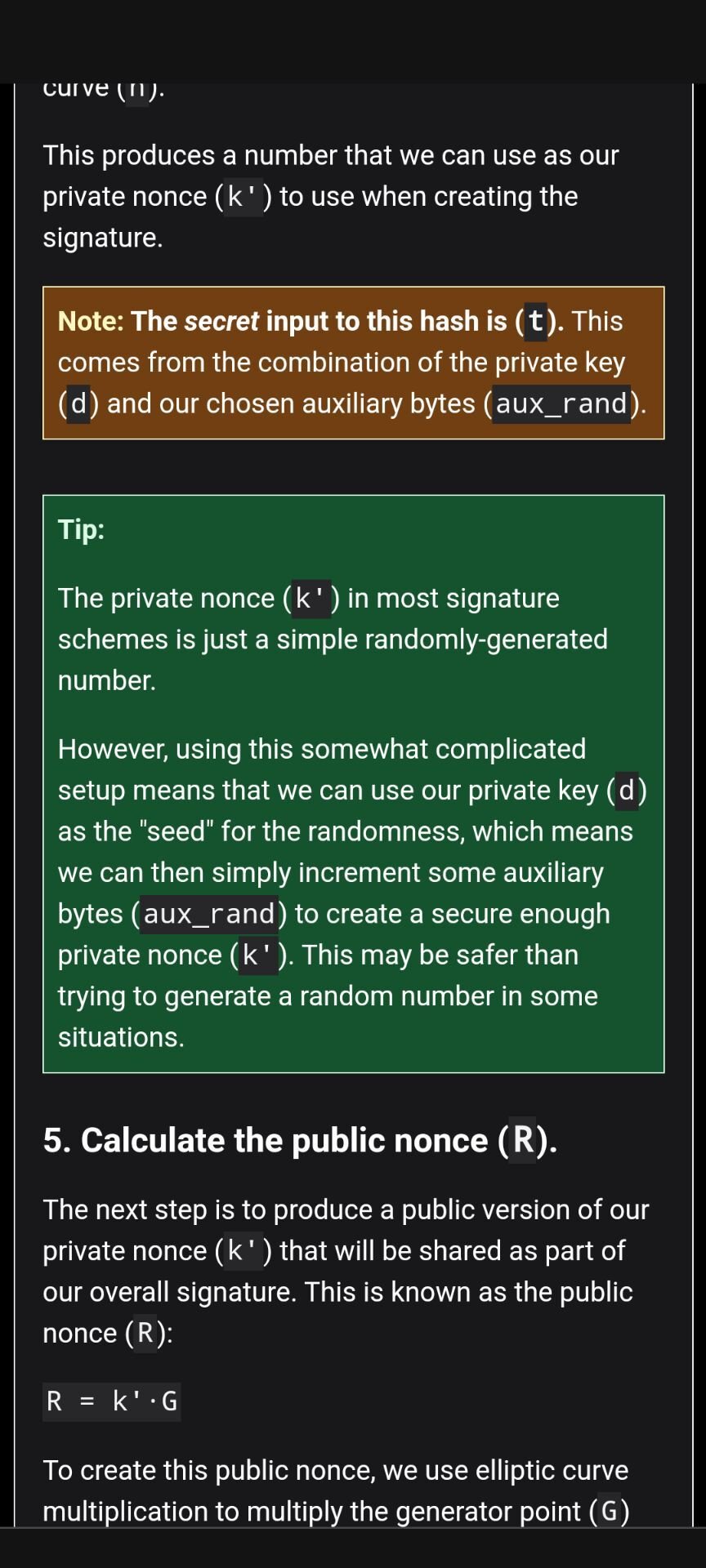
w2c

Would keeping aux_Rand a counter be used in something like FROST?
nostr:nprofile1qqswrlemlh2wgqc4jkds3d8ueqj9a2j3gcm7r48v9tskdd6rxsd7rtcpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqjxamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6jg4k33 nostr:nprofile1qqsdnpcgf3yrjz3fpawj5drq8tny74gn0kd54l7wmrqw4cpsav3z5fgpz4mhxue69uhk2er9dchxummnw3ezumrpdejqz9rhwden5te0wfjkccte9ejxzmt4wvhxjmcprpmhxue69uhhyetvv9ujuumwdae8gtnnda3kjctvl3x2lg
Yeah we do something like this in frostsnap, it used to explicitly be called aux_rand. We're just seeding ChaCha20Rng with our secret share, and using the nonce counter to increment 
oh yeah i forgot to bring this up, it's very easy to scrape every image uploaded to primal
nostr:note1c5mclzmgke7lsq9dp6j4lqewrngxafwemykrl8ynnttdjpdq7wxsnhgqzn
need proof of home address before image rights
In that case the attack could simply exfiltrate the master xpriv
Today we disclose Dark Skippy - a powerful new method for a malicious signing device to leak secret keys.
With a modified signing function, a device can efficiently and covertly exfiltrate a master secret seed by embedding it within transaction signatures
https://darkskippy.com/demo.mp4
If an attacker manages to corrupt a signing device, Dark Skippy can deliberately use weak & low entropy secret nonces to embed chunks of the seed words into transaction signatures.
It takes just two input signatures to leak a 12 word seedphrase onto the Bitcoin blockchain.
The attacker can watch on-chain until they spot an affected transaction, unblind and invert the low entropy nonces using an algorithm like Pollard's Kangaroo algorithm to learn the master secret seed.
Then the attacker can wait and steal the funds whenever they decide best.
Despite this attack vector not being new, we believe that Dark Skippy is now the best-in-class attack for malicious signing devices.
- The attack is impractical to detect
- Requires no additional communication channels
- Effective on stateless devices
- Exfils master secret
Beyond ensuring your device firmware is genuine and honest (opensource), mitigations include anti-exfil signing protocols and we present some new ideas for additions to PSBT specifications to disrupt this attack.
We encourage mitigation discussion and implementation exploration.
This attack highlights the importance of verifying and securing your device's firmware, and the danger of sharing stateless signing devices with other people.
We will be publicly releasing our code later this year.
Authors: nostr:npub1xh897wvhn93tda0zws94mdyc7eagc8qm0798clp7x48zh6kjwazq29gst6 (follow him so he gets onto nostr), Robin Linus, and myself.
If you have any concerns or questions we recommend checking out the FAQ page on our website:
Check out our latest prototypes for the next generation of Bitcoin self-custody!

Why shouldn't I eat a complimentary biscuit?

now this is podracing
toxic trait: adding target="_blank" to absolutely every link on a website
First zap.stream:
Tried to get my zaps working again, realized channels were dead
Tried to abandon channels, funds disappear from wallet
Tried to reset wallet transactions, exposed RPC secrets
Tried to export node seed, LND doesnt let you
100k sats vanished into the ether, reckless.
Job for tomorrow.
zap.stream is good though, no note spam
nostr:note1u2x7zj3h8k208kvkrn6gkj5p2dalg9gzwtwseaxxy38sjpa49tzqsugy58
testing reckless nostr apps goodluck to my npub
I WILL USE
love it, PNG? 🙏
cool post from nostr:npub1l6uy9chxyn943cmylrmukd3uqdq8h623nt2gxfh4rruhdv64zpvsx6zvtg
https://conduition.io/coding/ticketmaster/
My friend sent to me,
"Wait I know this person, they wrote some incredible FROST posts and are on nostr!"
I scored 0 in the snake game! #snakegame
true but need some proof if someone is putting an existing identity on nostr. Would be very easy scam to make fake account and ask for donations nostr:npub17xvf49kht23cddxgw92rvfktkd3vqvjgkgsdexh9847wl0927tqsrhc9as 🤨
all accounts are fake unless NIP05d or otherwise attested
Update your bitcoin nodes!
sudo apt update && sudo apt upgrade
A recently disclosed SSH exploit is actively being attempted!

~3 lines of python to pause ecash redemptions except for a winning token
~5 lines of code on the mint to randomly select a winning token
~10 lines of code for a physical unlocking mechanism to activate upon balance increase
i completely made this up but could be real


