I'm ignoring stuff like attacking le blockchain because that's not in the same realm as mary sue's password for her secret recipe book
nostr:npub15fkerqqyp9mlh7n8xd6d5k9s27etuvaarvnp2vqed83dw9c603pqs5j9gr talking about systems with access control usually isn't relevant when talking about password cracking. Only really interesting when they have the hash on a local disk.
I mean, that's basically a non-problem. They somehow got my encrypted file without otherwise compromising me, and know enough about the encryption scheme to try attacking it? Like, I lost a floppy disk and the disk has "encrypted with X" written on it or something
I'm sure there's stuff you can determine by inspection of the encrypted data, but not with much certainty
How does an attacker find out how long your password is, if you don't tell them? I'm open to the idea that maybe somehow that can be done through some trickery, but I don't see how.
a password is just a little piece of a security system and in these discussions that often gets lost
like the stuff about people extracting data from airgapped systems by using a freaking SATA cable as a radio antenna, the proposed vulnerability is irrelevant because by the time it's accessible, you're already totally compromised
my position is the NSA can crack just about anything if they want to devote their resources to it. 1 billion tries a second? pfft they'll run it in parallel in a warehouse of servers the size of rhode island if they're serious
but in order to do that at all, they have to have a copy, yes? they're not doing that remotely, or even with remote access, because any sane system would notice and halt a spike in authentication requests beyond known peak + some margin. so you're likely pwned for a whole bunch of reasons and the password isn't going to save you
most people don't need their passwords cracked because they'll fall for a basic phishing scam
nostr:npub15fkerqqyp9mlh7n8xd6d5k9s27etuvaarvnp2vqed83dw9c603pqs5j9gr ok so apparently you can't see my post to enzymical. The other hand of that was:
I don't think the average person is creative enough to NOT pick one of the known sentences so it would be a very bad security policy if you're talking about a commercial product.
Frankly though I'm not sure I could pick a sentence that's never existed if I was really trying.
No, I see it, and I'm trying to tell you that the fact that a password is known to exist does not compromise it absent *a lot* of knowledge about the specific nature of the password.
I can generate every 30 character combination of alphanumeric+common symbol passwords trivially, does that mean a 30 character random password is easy to crack?
nostr:npub15fkerqqyp9mlh7n8xd6d5k9s27etuvaarvnp2vqed83dw9c603pqs5j9gr I feel pretty confident that the NSA has a list of all known valid English sentences (with permutations) and they could probably run it in a few minutes. I don't have proof of this but I suspect a table like that would fit within a terabyte
How are they going to do that without a copy of your data on their server? You're already pwned at that point.
Yes, it is, because Password123! is in Professor Hackmo's pocket dictionary of passwords for script kiddies, and a ~60 character passphrase of semi-random english words is not.
nostr:npub15fkerqqyp9mlh7n8xd6d5k9s27etuvaarvnp2vqed83dw9c603pqs5j9gr see my response to enzymical. If the sentence is mutated in some weird way, you're probably right, but if the sentence has ever been spoken by any human in history it will be trivial to find it with a modern computer.
I don't think the average person is creative enough to NOT pick one of those so it would be a very bad security policy if you're talking about a commercial product.
Just because a sentence is known to exist doesn't mean the attacker can reasonably pick it from the ~10^5000 options. Any information you give an attacker about the nature of a password bounds the space, regardless of the nature of the key.
The point is, unless the attacker *knows* they're looking for english passphrases that are very well defined -- which they don't because nobody has a security policy specifying such a thing -- the fact that a password is a phrase in english does not weaken it at all.
nostr:npub15fkerqqyp9mlh7n8xd6d5k9s27etuvaarvnp2vqed83dw9c603pqs5j9gr I think with the restrictions of valid grammar, the number or meaningful English sentences is actually very small compared to random character combinations even with many words. Even if there are billions of them, that's no problem for hashcat.
I don't think so. If you consider words as symbols, sure, some of them only have a few possibilities. But some have tens of thousands of possibilities. How many nouns are there in the English language? How many verbs?
And the assumption that the sentence will be strictly perfect English is an extremely poor one to begin with.
And the attacker doesn't have any knowledge that they should be using such a rule set. They just know it's a string of characters. In the case of my example, it's 63 characters. They don't even know how long it is.
It would be stupid for a password policy to be "You have to use a password that strictly conforms to the rules of written English and is between 30 and 40 characters long" but nobody is suggesting doing that, and that's not what the anti-phrase claim itself makes about the security of a phrase.
to a computer a password should just be an array of bytes and a space is just "00100000"
if they don't allow spaces, it suggests they're doing something like string concatenation that directly inserts the password into a bit of code, which is a very bad idea
I've never understood this claim but I've seen it quite a bit
like, maybe this could be an extremely specific attack on an individual known for some phrase, but otherwise, you're not doing a successful dictionary attack on a long password just because it's a sentence in more or less proper english
even if you claim there's some loss of randomness due to the patterns of letters and spaces -- which is true -- that's more than offset by how easy it is to remember and type out an *extremely long password*
"and so mary said, bring me a cup of orange juice with my toast"
good fucking luck pal
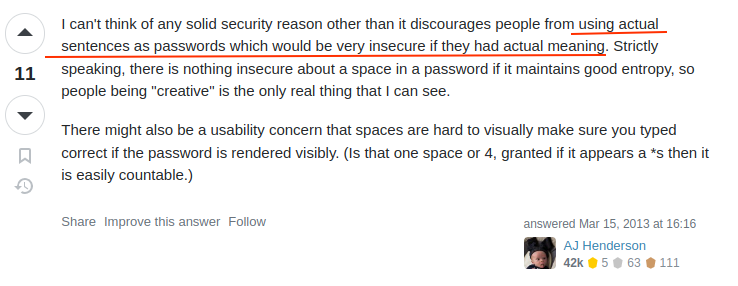
not allowing spaces in passwords seems like a pretty big red flag that the underlying code is crap
you can't just link your game folder again? should still be there unless you intentionally went through uninstalling them
you'd think they would have to read the Bible cover to cover
more than once
despite
>get up
>back doesn't hurt at all
it's a christmas miracle
yeah but I mean the motivation behind the decision to use those switches specifically
I have several very cheap mice and they're all at least usable, but this thing is the worst mouse I've ever seen
