To broadcast a raw transaction over Tor anonymously
you have the command 'torthistx' available in all of your #Raspiblitz terminals.
To use it simply copy a raw transaction from Sparrow Wallet for example and paste it to the terminal after:
torthistx
It will return the TXID.

#torthistx
A quick summary on regreSSHion https://cert.europa.eu/publications/security-advisories/2024-066/pdf
Most home nodes are not exposed to the public internet, but any cloud server or VPS is at high risk.
Log in and check the openssh-server version with:
apt list openssh-server
See the safe versions for Debian (most distros on RPi are Debian based): https://security-tracker.debian.org/tracker/CVE-2024-6387
for Ubuntu (the most used on cloud servers): https://ubuntu.com/security/CVE-2024-6387
in many occasions autoupdate (aka unattended-upgrades) took care of it already, but if not run manually:
# update the apt store
sudo apt update
# look for openssh-server updating
sudo apt upgrade -y
# restart the ssh service to update the running code
sudo systemctl restart ssh

#regreSSHion #security
Most devices can be flashed with the degoogled open source OS: https://lineageos.org, but only Google allows on it's flagship devices for the bootloader signing keys to be changed so it can be safely relocked: https://grapheneos.org/faq#future-devices
Do not disturb, nodes are syncing!
In for the #Raspiblitz demo at #PizzaDayPrague this time. See some of you there 🫡


Gogol Bordello - Start Wearing Purple (rootzoll nostr video edit)
nostr:npub1a8q2nsfw8gzwm4u6l3ma3xmvvsfue9pwl8npc509z2puh6wmpj8sqk3zhj & nostr:npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm
Welcome on Nostr Rootzoll, looking forward to the music posts uncensored!
nostr:note1du9qkg5zqnzxz0qdr69wy2j2g3sxt8r0myd3ergxd8kwyx3d2ptq89za3e
Hold off updating Bitcoin Core to v27.0 if you have LND connected.
Will be fixed in the upcoming LND v0.17.5 soon.
Source: https://twitter.com/roasbeef/status/1781086945986404559

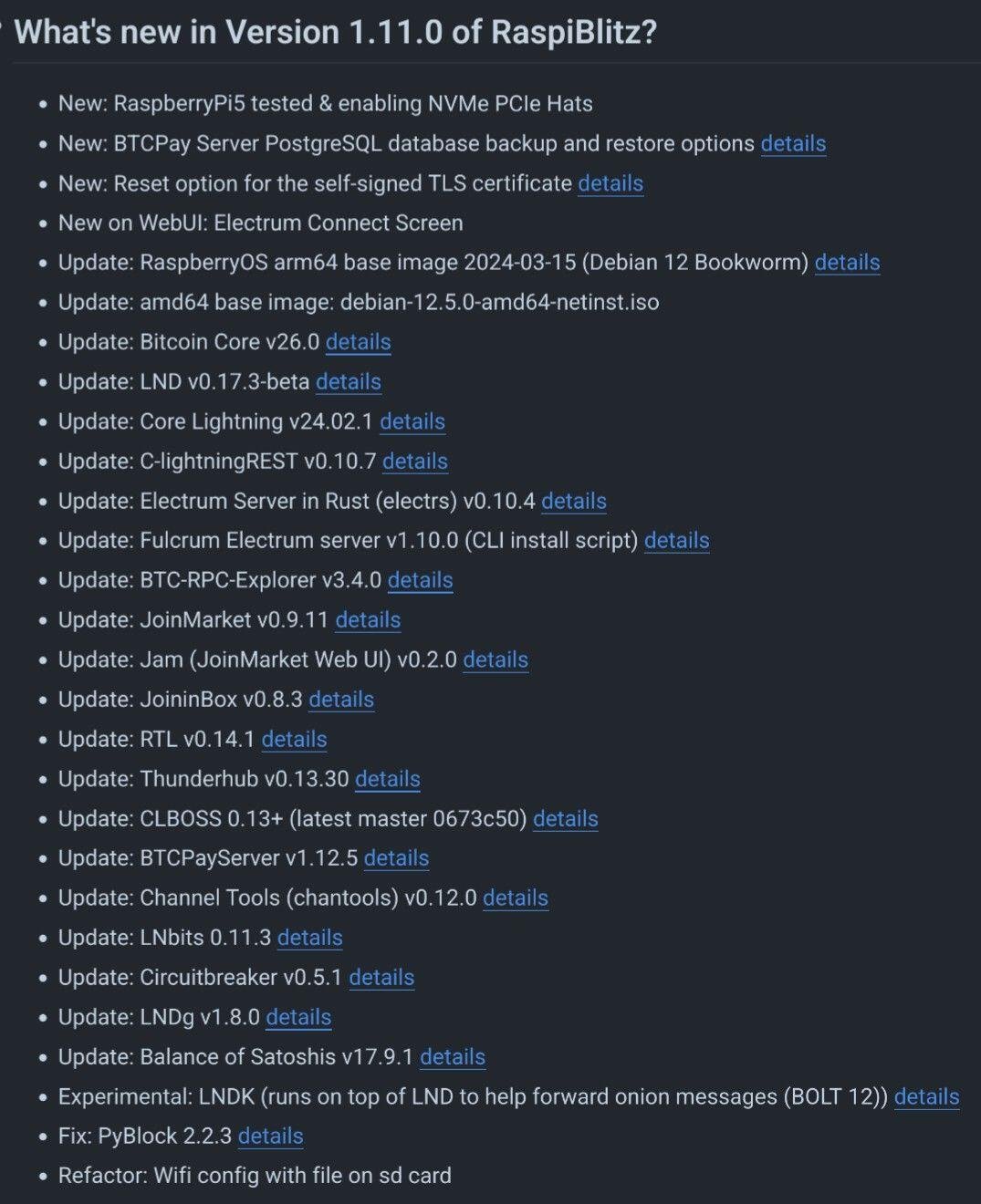
⚡ Version 1.11.0 of RaspiBlitz released ⚡
Now supports RaspberryPi 4 & 5 with NVMe PCIe drive. Many updates: Bitcoin 26.0.0, LND 0.17.3, Core Lightning 24.02.1, LNbits 0.11.3 .. and new documentation.
Download: https://docs.raspiblitz.org/docs/setup/software-setup/download
The name is biased, but the #Raspiblitz scripts run on anything Debian compatible on aarch64 and amd64 including Thinkpads:
https://github.com/raspiblitz/raspiblitz/tree/dev/alternative.platforms
you can find prebuilt images too.
If would prefer more manual work see: https://v2.minibolt.info/ (built from the Raspibolt guide)
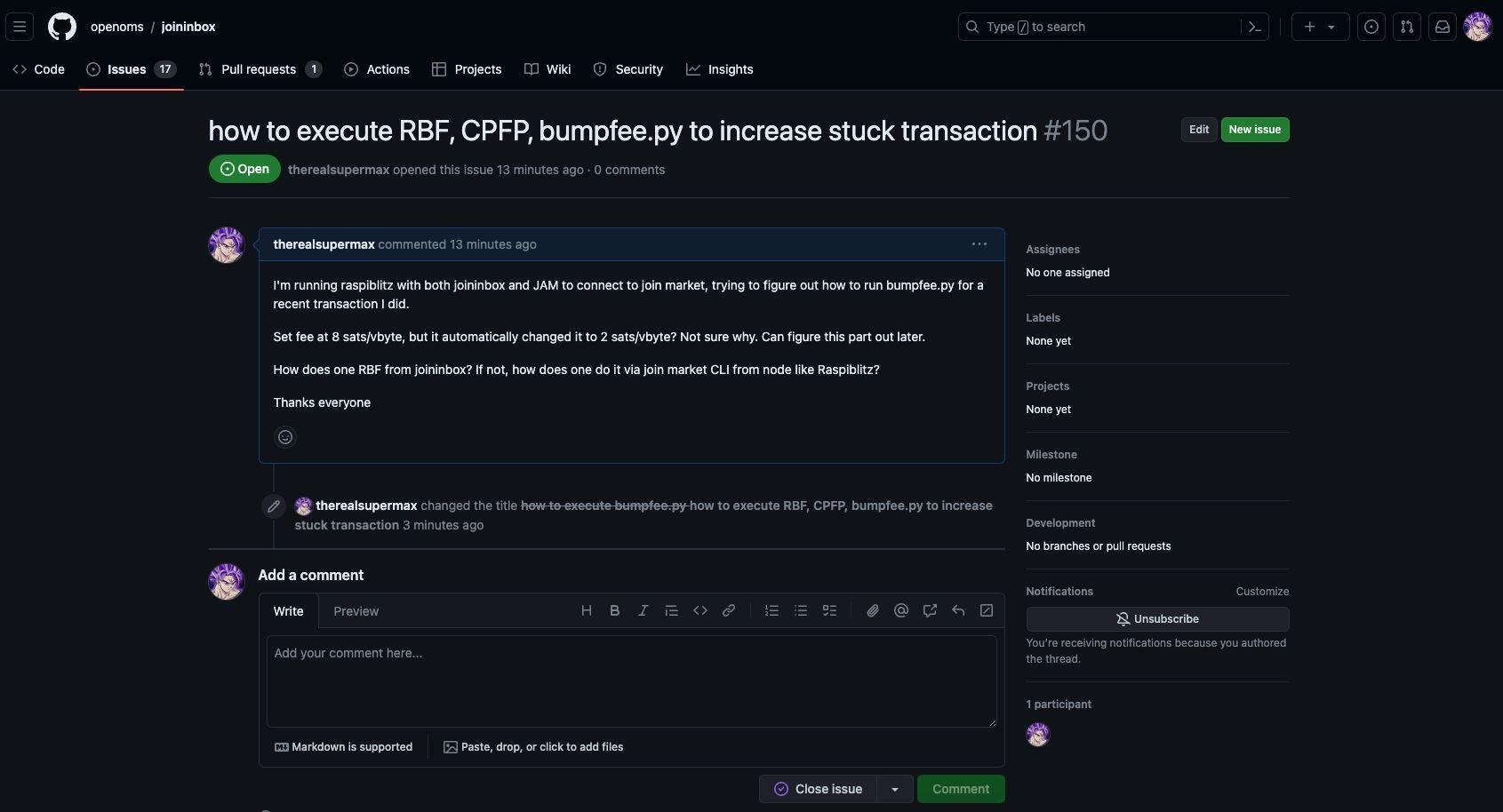
Interesting, not sure how it has not been posted. There is the issue (PR) #149 and just merged #151 so #150 was reserved, but not there.
Let me know if you see this again.
As you said nostr:npub1yu7h0k3sqf065d37gzmpz4d0eq7ehamtw75n0s3n2lelmyhctt9q70g5em, instead of using electrum to recover the wallet & mixdepth, I used nostr:npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2 Sparrow Wallet
Added additional needed accounts, CPFP, done
Worked great
Still want to practice running bumpfee.py in CLI
Enter the JoininBox menu and exit to the terminal. It will put you right into the scripts folder of JoinmMarket with a bash prompt.
GM. Happy Easter! Don't fall for April Fools today.
Can confirm having no audio issues with Graphene on a Pixel5.
I sometimes got random app crashes when Google Services were updated by Google Play.
To check go to the Apps app and reinstall Google Play services if the Available version is lower then your current one.
Should look like this:

Heads up if using the testing / unstable version of Debian, Ubuntu, NixOS or other Linux OS based on these, there is malicious code in the latest xz package: https://www.openwall.com/lists/oss-security/2024/03/29/4
>The malicious injection present in the xz versions 5.6.0 and 5.6.1
>Luckily xz 5.6.0 and 5.6.1 have not yet widely been integrated by linux distributions, and where they have, mostly in pre-release versions.
Running stable versions are fine:
₿ xz --version
xz (XZ Utils) 5.4.1
liblzma 5.4.1
Make sure to check on your Mac-s as well, the xz package is downgraded to xz 5.4.6 from 5.6.1 with the last brew upgrade.
nostr:note1ymdq8ynkvcy7s8d23r9v2kdjq0xsnd7puwwsakyxh9wlxke4dxdqwsah82
Heads up if using the testing / unstable version of Debian, Ubuntu, NixOS or other Linux OS based on these, there is malicious code in the latest xz package: https://www.openwall.com/lists/oss-security/2024/03/29/4
>The malicious injection present in the xz versions 5.6.0 and 5.6.1
>Luckily xz 5.6.0 and 5.6.1 have not yet widely been integrated by linux distributions, and where they have, mostly in pre-release versions.
Running stable versions are fine:
₿ xz --version
xz (XZ Utils) 5.4.1
liblzma 5.4.1
h/t for the early warning nostr:npub1fusn44jf2h4zc7pal32a87qzhu2ruf49kd4vaws97d02jddnhs6s98gatx
Heads up if using the testing / unstable version of Debian, Ubuntu, NixOS or other Linux OS based on these, there is malicious code in the latest xz package: https://www.openwall.com/lists/oss-security/2024/03/29/4
>The malicious injection present in the xz versions 5.6.0 and 5.6.1
>Luckily xz 5.6.0 and 5.6.1 have not yet widely been integrated by linux distributions, and where they have, mostly in pre-release versions.
Running stable versions are fine:
₿ xz --version
xz (XZ Utils) 5.4.1
liblzma 5.4.1
Nope, not hacked, was just testing the page in prod 💪
Hey Nostr,
Please help me with this #bitcoin issue and I can pay sats for your time:
send me bitcoin
send me 21 satoshis
Make an offer on this URL:
#bitcointroubleshoot #asknostr #blink