I currently have an enterprise grade router and am going to replace it with OPNsense.
For my wifi access points, it's OpenWRT, but they don't do any routing, DHCP or anything interesting. It really just converts between ethernet and wifi.
I've heard microtik is pretty decent in terms of security, but I haven't used it nor done any analysis on it personally.
Yeah and it looks like that $2000 only gets you the card, not any storage. "**Additional configurations**, which include pre-installed SSDs... will be available, although their specific pricing details have not yet been disclosed."
Did you read the article I linked which is in support of BIP-47 and says you are dead wrong about it not having worse security for the sender?
TP-link has earned a reputation as a producer of insecure routers. They seem to push things out as soon as the code is functional without any security testing. Yeah, they're absolutely a security risk.
But there's some additional context required here. Pretty much all the other Small Office/Home Office (SOHO) routers do the exact same thing. People want cheap devices and there's no independent security testing reports that consumers can use to tell which ones are actually more secure. So they choose based on price and thus the companies focus on price instead of security.
Second, there's reason to question the threat to national security. These routers aren't secure, but they are also not used in big companies for anything important (if in use at all). Companies are well aware that home offices are not necessarially secure and they keep the data on their server where they have proper protections in place. Attackers getting into home networks is kinda expected and planned for.
Small businesses are at risk, as they generally don't have any cybersecurity. But again, this is not unique to TP-Link nor is a mom & pop shop getting hacked a matter of national security.
Q: Does BIP-47 (reusable payment codes, the successor to silent paments) make privacy worse for the sender?
A: Yes
https://silentpayments.xyz/docs/comparing-proposals/bip47/
There are also advantages to BIP-47.
Know the trade offs that you are making when you choose which technology to use.
Side note: if someone wants to make a diagram of how this works, I think it would really help with educating people on BIP-47 and likely increase its adoption.
For prototyping, OSH Park.
For production runs, it depends on the size of the board. I'll stick with OSH Park if it's a small board, but they're way too expensive for anything bigger than a couple inches. For those I usually go to jlcpcb, but I've also ordered from pcbgogo and a couple others.
Yeah, I'll concede that. But it is heading in that direction. Similar to open source software or the sharing economy.
Bitcoin Heist
https://m.imdb.com/title/tt4911780/
It was made in Vietnam is is everything you'd expect from a foreign Heist film.
We strain ours to ensure it's not too runny. Do you know any tricks to get it to thicken up more?
I'm using an existing project that already wrote an debugged all the code, which is why I went with the nano. After my janky little prototype worked, I designed a hat for this. I'm going to have a buddy review it next. If I get the 👍, I'll order 3 boards & the components, build out one board, possibly repeat this process a few more times, to get a working setup, and submit a merge request to get the KiCAD files upstreamed.
It'll be a while before it's done, but it'll be a good experience to build my first hat (for anything!)
Well, I got the pins baclwards on the first try. Apparently swapping 5V and GND didn't release the white smoke on anything.
"For Those Interested In I2P, Here's A Great Interview By Diva.exchange, featuring idk Of The I2P Project.
Including Info On Recent Attacks On The Network"
https://www.diva.exchange/en/privacy/i2p-interview-with-the-developer-idk-part-1/
Via: https://fosstodon.org/@RTP/112986781257178806
#I2P #networking #infosec #cybersecurity #encryption #privacy #anonymity #anonymous #crypto #banking #e2ee #tech #DivaExchange #proxy
I'd encourage you to listen to the first 3 minutes. If you're not hooked, then it's not for you.
#SelfHosters will love this one:
From the author: "I firmly believe that handling your own data, running your own services, and housing it all on your own hardware is a radical act of anti-capitalism and personal expression."
#Privacy #SelfDetermination
You might think the pins on one end are in the same order as the other end of this cable. Nope.

They're all jumbled up, one of them is missing, and the non-purple end has the plastic alignment pin knocked out, presumably because it was just ever so slightly in the wrong place for a keyboard port.
I don't know what this was supposed to go to, but it sure isn't useful to me.
Okay, that was totally the *wrong* way to wire that to the PC, but I didn't burn anything up nor injure anyone.
In the end, I found out that:
1. **both** of the USB keyboards I was trying to use were bad
2. When connected correctly, my little gadget works!
And I was able to repair my BTC keyboard, but the Microsoft one isn't looking good.
If you never hear from me again, it may be related to this...

🤔 Could the "r" in #nostr be implemented with a #Matrix chatroom? It's just another transport mechanism.
Anyone allowed in the room would be able to fetch messages from that relay.
Anyone authorized to chat in that room would be able to post their signed notes.
It could also provide e2ee so the relay operator can not see the contents of the posts.
I guess it might break search as a result? I'm not sure if search depends on relays to do any filtering or if it all happens locally.
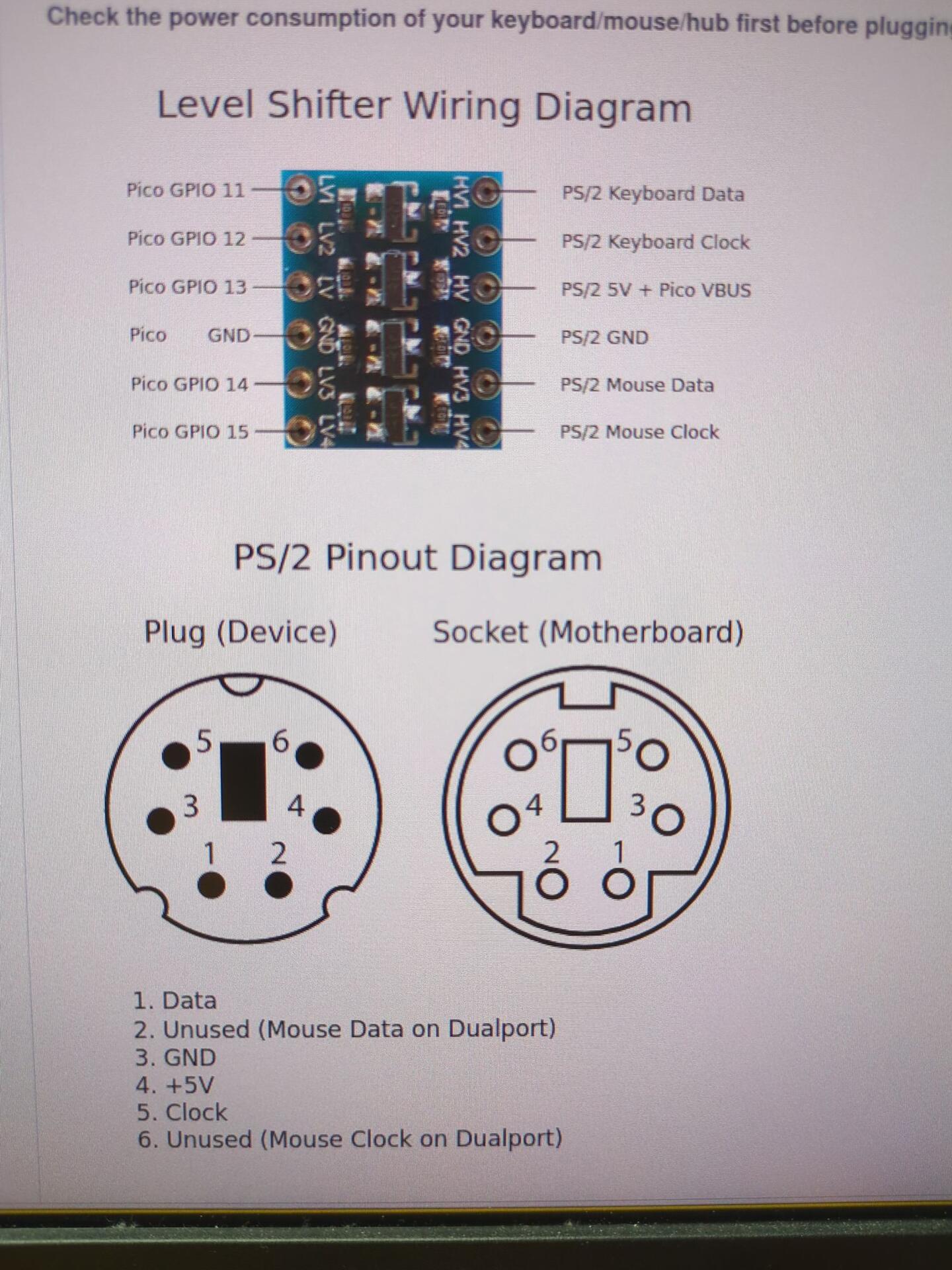
Don't mind me, I'm just over here building custom hardware to make my computer safer.
It occured to me that people here might both enjoy and not know about #PagedOut
"Paged Out! is a free experimental (one article == one page) technical magazine about programming (especially programming tricks!), hacking, security hacking, retro computers, modern computers, electronics, demoscene, and other similar topics."
#hacking #retro #computing #security #infosec #electronics #demoscene #zine #mag #magazine
