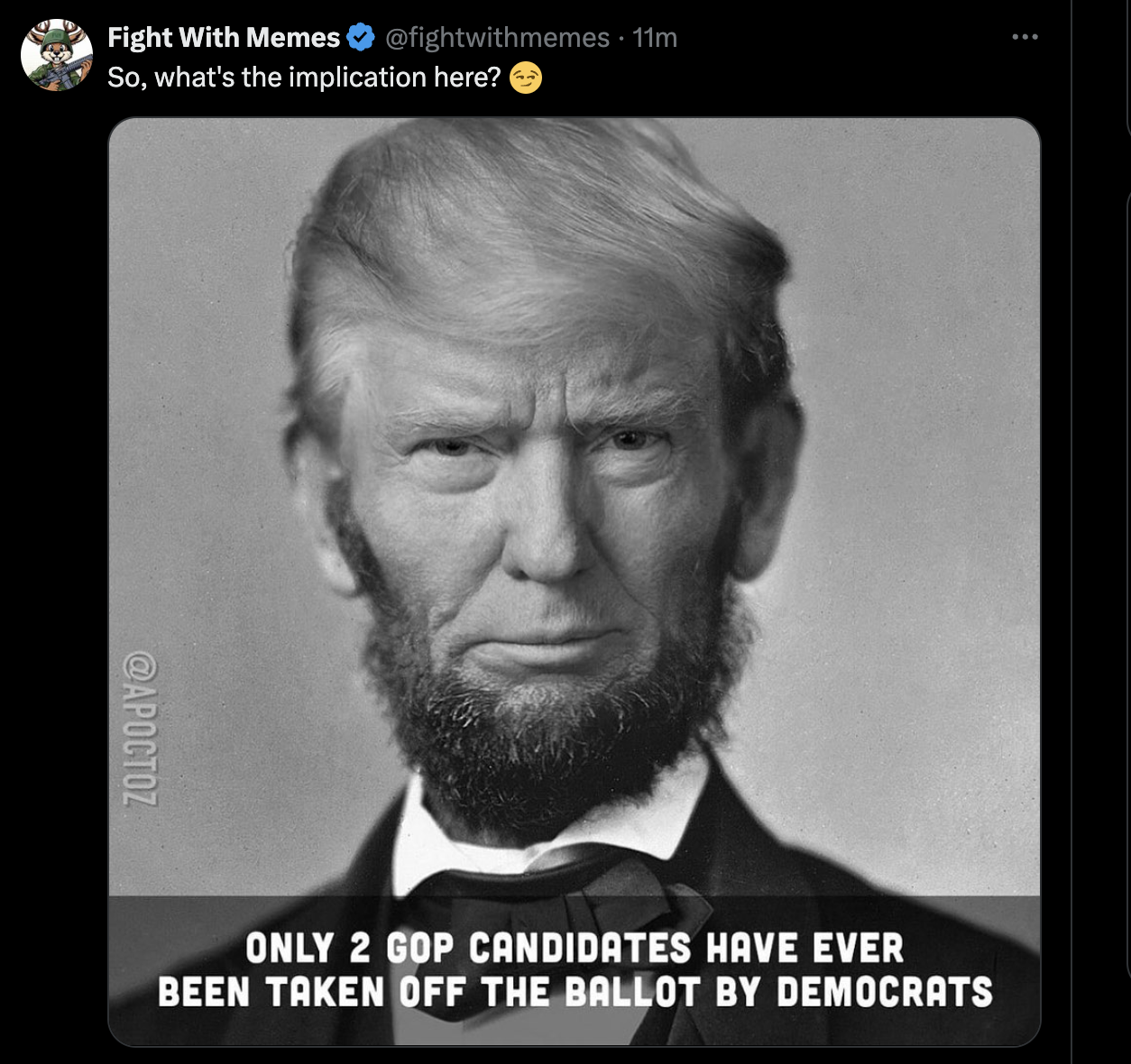
Lincoln was not the greatest person
What model is this? I like the antenna
Was encryption not a thing before?
JUST IN:
🇺🇲 Kamala Harris:
"Trump would invoke Adolf Hitler, the man who is responsible for the death of six million Jews."
The US presidential election has turned into a Jewish election...
https://video.nostr.build/af0fa7309ef75089112075bb634ba81ad3b1c39a2b27a94796b6dea9f14c7488.mp4
Zionmaxxing
Indeeed
All using web flasher?
You could write your own transport. It is in Python and then get that to work if you wanted to.
Yeah I don't recall it using Meshtastic?
Like I never investigated how the RNode's communicate but I never thought they would be using the Meshtastic protocol buffers?
Based. Got some photos?
Also did the Heltec come with no firmware originally?
And then with those borders those who occupy the state, keep enforcing them
That is what my parents tell me at least. I have never bought a television. Nor would I pay a license for one 😂😂, given the context here.
SABC is still around, yes.... 😂
The gift that keeps on giving...
If I hate any state, including Israel.
Am I an anti-semite then?
In ZA they do but I still don't agree with the mechanism. The state broadcaster here did not homestead every channel/band so they can't make a claim to it like that.
Yet, in ZA to buy a TV you must actually have a license. It is bizarre.
Not required for a radio though, I believe.
All a scam
It is filmed kinda weirdly. Maybe fake but to make a point that we all know is worth making.
"Can't pay for something you never signed up for". Merely, saying that my TV could pick it up isn't justification.