Mobile Network Surveillance Tracking Methods and How to Mitigate Against Them
This list is not exhaustive by any means, but it will serve as a good introduction. I am working on a proper longform post to simplify and flesh out this topic with more detailed, actionable advice.
#cybersecgirl #mobile #tracking #privacytechpro
https://techcrunch.com/2023/12/16/google-geofence-warrants-law-enforcement-privacy/
FBI / Cast Cellular Analysis and Geo-Location Guide 2019 (Unclassified)
Mobile Network Surveillance tracking methods include:
Geofencing, Geolocation Trilateration Triangulation
https://tracki.com/pages/how-gps-tracker-works-and-cell-phone-tower-triangulation-accuracy
Stingrays / Aerial Stingrays (Dirtboxes)
https://sls.eff.org/technologies/cell-site-simulators-imsi-catchers
https://puri.sm/posts/taking-the-sting-out-of-stingray/
IMSI
https://www.whonix.org/wiki/Surveillance_Capabilities
Malicious SMS Re-Routing
https://www.kicksecure.com/wiki/Mobile_Phone_Security#Malicious_SMS_Re-routing
Mobile Device Privacy and Security
https://www.kicksecure.com/wiki/Mobile_Phone_Security#Telephony_Protocols
Bluetooth
https://arxiv.org/pdf/2107.05868
Airtags
Full resources:
https://buggedplanet.info/index.php?title=Main_Page
Some Mitigations:
Use GrapheneOS. #GrapheneOS is able to turn off Wifi and bluetooth scanning + GPS.
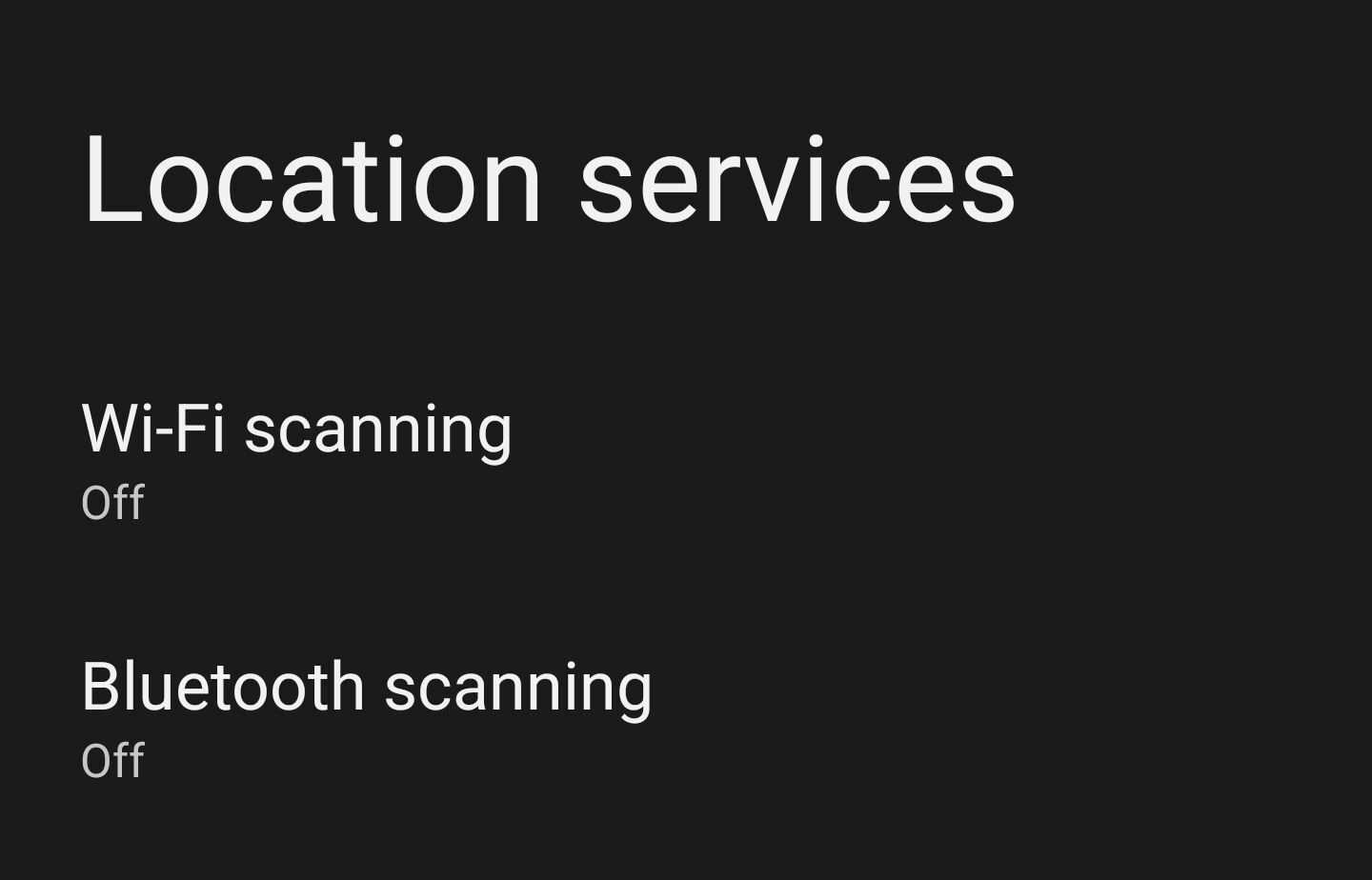
Faraday bags, airplane mode, modem and sensor kill switches, always-on VPN. Do not autoconnect to WiFi or Bluetooth (keep off when not in use)
RFID (keep off when not in use)
IMEI change
https://www.srlabs.de/blog-post/blue-merle
https://github.com/srlabs/blue-merle
Bluetooth
https://github.com/Semper-Viventem/MetaRadar
AirGuard
https://discuss.privacyguides.net/t/airguard-foss-airtag-detector/12391
Hackers only need your phone number to locate where you are instantly (ss7).
Also RSA chips (chips that generate randomness in your CPU) are compromised by the NSA (meaning most end to end encryption can be compromised) and on top of that there is Intel's Management Engine, or AMD's Platform Security Processor.
Not to mention Sim Swapping.
Look at Tucker Carlson, how his Signal app got compromised. Signal has quantum proof encryption, yet a sim swap is enough to "break it". They did add usernames to make that method not work anymore, but there are other methods.
Not being tracked is impossible, only thing you can do is make it harder and blend in. But for most people, you're not important enough for the government to care about you. Unless you do something illegally, you shouldn't be too paranoid.
The best thing most people can do (the 20% that do the 80%) is not have social media, use Linux with an encrypted drive, use burner phone numbers, and use old tech like a Thinkpad.
For those interested look at Mental Outlaw on YouTube. Also don't fall into honeypots like this post 😂