Myth: Browsers can Fool AI by “Spoofing”
Reality: Spoofing is just lying with your words.

Even back in 2016, Google could detect spoofing:

Google gives your client a challenge to draw. This image is from their (now ancient tech) 2016 whitepaper: [12]
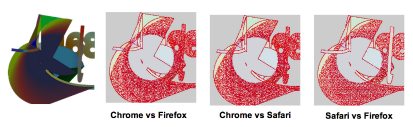
Then these drawings are analyzed at the pixel level,
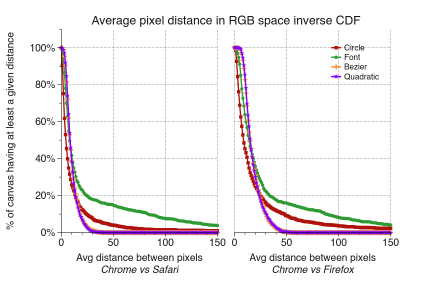
And compared to what that browser, OS, and hardware can normally produce,

This is why the Chameleon Browser Extension whitelists Google and Cloudflare [14]

Because their app, and those like it, just LIE with “user-agents” (their words)

You can’t hide the fundamental nature of browsers,
For example, when someone asked if they should block the specific type of JavaScript (that hides your screen size), the GrapheneOS dev said: [10]

In other words, they fingerprint you based on what you choose to block,

And if you turn off JavaScript,


Enjoy the rest of the fun meme slideshow or get sources:
https://simplifiedprivacy.com/myths-of-privacy/fake-or-unrealistic-solutions-smashed.html


