Yup.
And we will continue to be here with a compelling alternative model, that requires much less trust in manufacturers and distributors. 
Yup.
And we will continue to be here with a compelling alternative model, that requires much less trust in manufacturers and distributors. 
How many various manufacturers hardware kits can nostr:npub17tyke9lkgxd98ruyeul6wt3pj3s9uxzgp9hxu5tsenjmweue6sqq4y3mgl run on today?
As of right now, just one, but progress on more is ongoing. But you're missing the point, it's not worth it to target the entire RPi supply chain at this point, and even if you wanted to target individuals, less than 0.01% of RPi products likely will end up as SeedSigners, so who knows which ones to pick. Whereas, at a certain point in a HWW's life, it's known that the device will be used to store PKs, and an attacker further knows that just about every device is going to someone who will potentially use it for that purpose. Different tradeoffs.
You know, honestly, I'd consider an iso. Just like tails.
There's no difference really between a hardware wallet (which is a general purpose) and a laptop (which is a general purpose computer).
Stick in a usb, boot into seed signer, and reboot.
Tails has been doing this for a long time. It's a proven security approach.
This is the same as our approach. Boot from attached storage, then remove the storage device to show the system is probably running from RAM. SeedSigner is just a single purpose, hardened, verifiably offline computer.
Love this approach, and I am a fan of SS.
Have yall given an expert cold eyes review further consideration?
https://github.com/SeedSigner/seedsigner/issues/391#issuecomment-1599256650
It's almost like you can't trust hardware!
I'll eventually tire of saying this but not yet.
I can’t trust the manufacturer of the generic pi board and chips either
We trust the manufacturer to do a lot less. We don't trust the device to validate software, we don't trust it to persistently store keys, and we don't trust it to make wireless or wired connections with other devices. We just trust it to execute SeedSigner code.
Pi’s don’t have secure elements and since you can’t verify the quality of board, the chip and the cameras how do you prevent side channel attacks?
All side channel attacks I am aware of require running software that has been maliciously modified. So to avoid that, run our released code.
Even if you run fully verified and open-source software, side-channel attacks focus on how the software interacts with the hardware, particularly during sensitive operations like cryptographic computations.
You are vulnerable to
1. Hardware Backdoors
2. Timing Attacks
3. Power Analysis
4. Electromagnetic Emanations
Even with verified software, side-channel attacks can exploit weaknesses in pre-installed chips or the board itself. The software may perform securely from a logical perspective, but the physical properties of the hardware can leak information through side channels. To defend against these attacks, both the software and hardware need to be carefully designed with side-channel resistance in mind. Devices with secure hardware elements and robust physical defenses are more resistant to such attacks.
I'm just going to agree to disagree with you here. I strongly disagree with what you’re saying, but I just don’t have the time to refute every far fetched exotic attack scenario. Have a great afternoon.
They’ve certainly not open sourced their hardware.
The guy running their organization is an ex cop (Technical Surveillance Officer to be exact), the company also lost its mind defending the hire
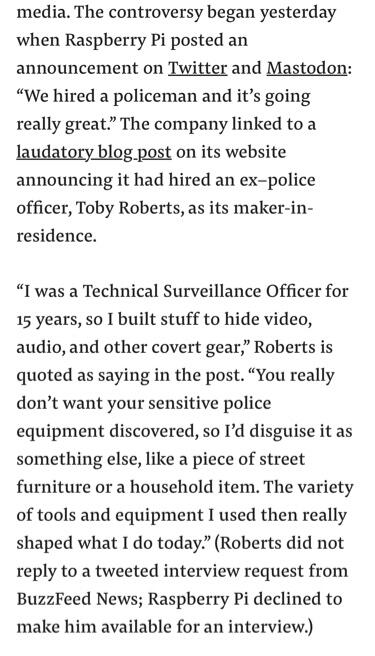
Just so you know, that is not me. No idea who "Roberts" is. I was an LEO however, but have been very candid that digital forensics was my specialty. You should really double check it your sources, would have been easy to find this out.
The fuck are you talking about. I wasn’t saying shit about you.
I have great respect for your work and of other projects too. But all y’all frame your products as ideal and the one thing you need. And then fight amongst each other when there’s opportunity to help and grow with each other.
I guess I feel like I've tried to talk about tradeoffs a lot and have always been willing to admit there are some use cases where a conventional hardware wallet makes a lot of sense. Meanehile some manufacturers constantly misrepresent our project for seemingly self serving reasons. But I understand it can be frustrating from someone with your perspective. I just don't know what the answer is.
I can see the dilemma but I have a serious question. Do seedsigners run on any other hardware other than rasberrypi? If not, can this be an issue with distributing manufacturers? I’m a novice when it comes to computers and the technical side of bitcoin software. All I know is to stack sats.