Just FYI #qubes
Just FYI #qubes

Tails is so money
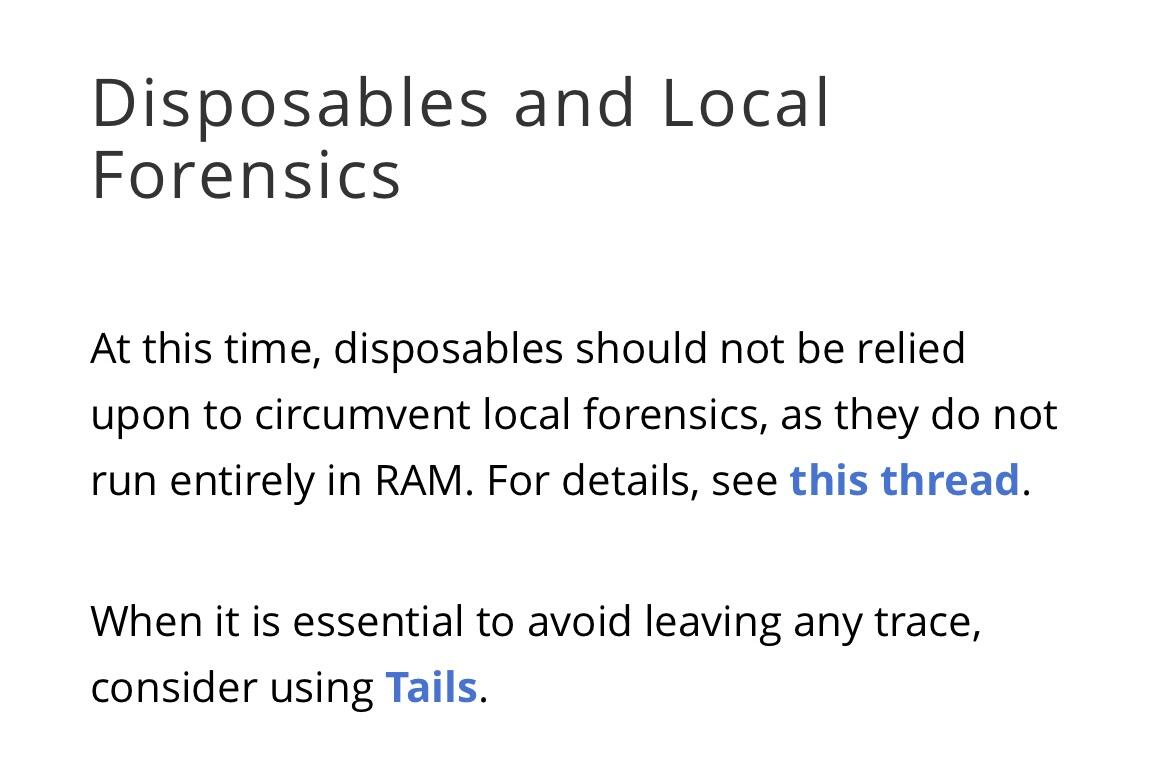
If your doing extremely "sensitive" stuff and your threat model involves the likelyhood of forensics, a second laptop + tails is a very good option for those activities. It's not really designed for daily driving like Qubes.
It is best OPSEC practice to always turn off and OS, including a hardened one like QubesOS when not in use. Qubes sys-usb VM protects against evil-mail attacks and the like, but as with any OS...
If an adversary has the ability to perform forensics and has access to your daily driver, compromise should be assumed.
Use Luks for encrypting QubesOS drive with a strong passphrase (remember though people could torture you or family members until you give it up).
Store sensitive files using Veracrypt + hidden volume (you could even go so far as to bind folders that leave forensic footprints to this volume) to provide "plausible deniability". Veracrypt works on both QubesOS and Tails.
It's all about layers and multi-layered encryption (i.e. encrypt the encryption decryption with layers of encryption). The more layers you can put between an adversary and your data, the more time and money or criminal risk it will have to be worth for them to get to your data.
Also, the second laptop should be new and NEVER associated with your identity in any way WHATSOEVER.
if I follow correctly
you mean rather than just using Qubes vms for everything?
Yes, for very sentitive situations/activities where anonymity is of the utmost importance.
Qubes is freaking awesome, but I still recommend a 2nd brand new device that has never been associated with your actual identity in any way, including having never logged in from your home network.
This is way overkill for most threat models. For the overwhelming majority of people, Qubes offers more than enough security via isolation and compartmentalization, including the ability to virtually airgap VMs, anti-evil maid, and anonymity via its Whonix integration and so much more--it's leaps and bounds over any other daily driver OS.
However, if you are performing extremely sensitive activities or are in extremely sensitive situations and you must use technology, and the likelihood of hardware forensics is in your threat model, then I recommend taking the isolation and compartmentalization to another level by using a completely separate device with an OS like Tails.
There is still the risk of having that 2nd device in your posession, so this is where an OS like Tails shines since it leaves no trace on the computer when shut down.
the thing i never understood about Tails practically,
you then need a yubikey right? gotta keep your priv key somewhere...
I used Qubes as my daily for a while but i got tired of hacking around withirt.
so now I have several devices instead lol
it was easier to just have a few old laptops/multi boot setups.
forensic analysis isn't in my threat model
but curious
Big fan of Yubikeys. Tails would need persistent storage to use one, but you can airgap keys with Veracrypt + hidden volume.
Here's a fun tutorial for generating and airgapping PGP private keys using GnuPG, Tails and YubiKey :)
Old-school with multiple devices does the job too. How long has it been since you used Qubes? There's been a lot of upgrades recently that have improved the UI/UX just over the past year.
Honestly can't imaging daily-driving anything else at this point unless Joanna builds something cooler, but IMO it's going to be hard for her to top Qubes.
Sorry to hear about your boating accident.
HDD can be wiped. SSD get the drill. I don’t know about M.2 but I’m pretty sure I can snap those in half by hand.
💯 Lets not forget about microwaving motherboard chips and simcards :)
Know your wipe ritual!
Fire destroys everything 🫡
In a previous job, one of the guys I worked with got hold of the chemicals to make thermite which we used to destroy some old hard drives! Pretty sure nothing would be recoverable from them after that! 😂
Nice!! Exactly. You've gotta fully make it irrecoverable. Breaking or microwaving only prevents standard means of recovery. Forensics can still retrieve artifacts.
microwaving only prevents standard means of recovery... 😳
imma brb
You need to burn it and/or pulverize it to the point it's turned to ashes. The only way to be certain.
A multiple step process for sure. Microwave is good for simple sd cards and flash memory when time is of the essence. Fire is great, but kinda toxic, still, it works. Hammer, sandpaper, then drill for mechanical drives etc, grind to a pulp or thermite. So many fun ways to destroy data :)
Thermite is just aluminum powder and iron oxide (rust). Pretty sure you have that lying around the house
Is this actually done? Does it ruin the microwave?
We all need an emergency button to wipe everything in few seconds with OliveTin 🚨☢️
https://noted.lol/olivetin-self-hosted-predefined-shell-commands/