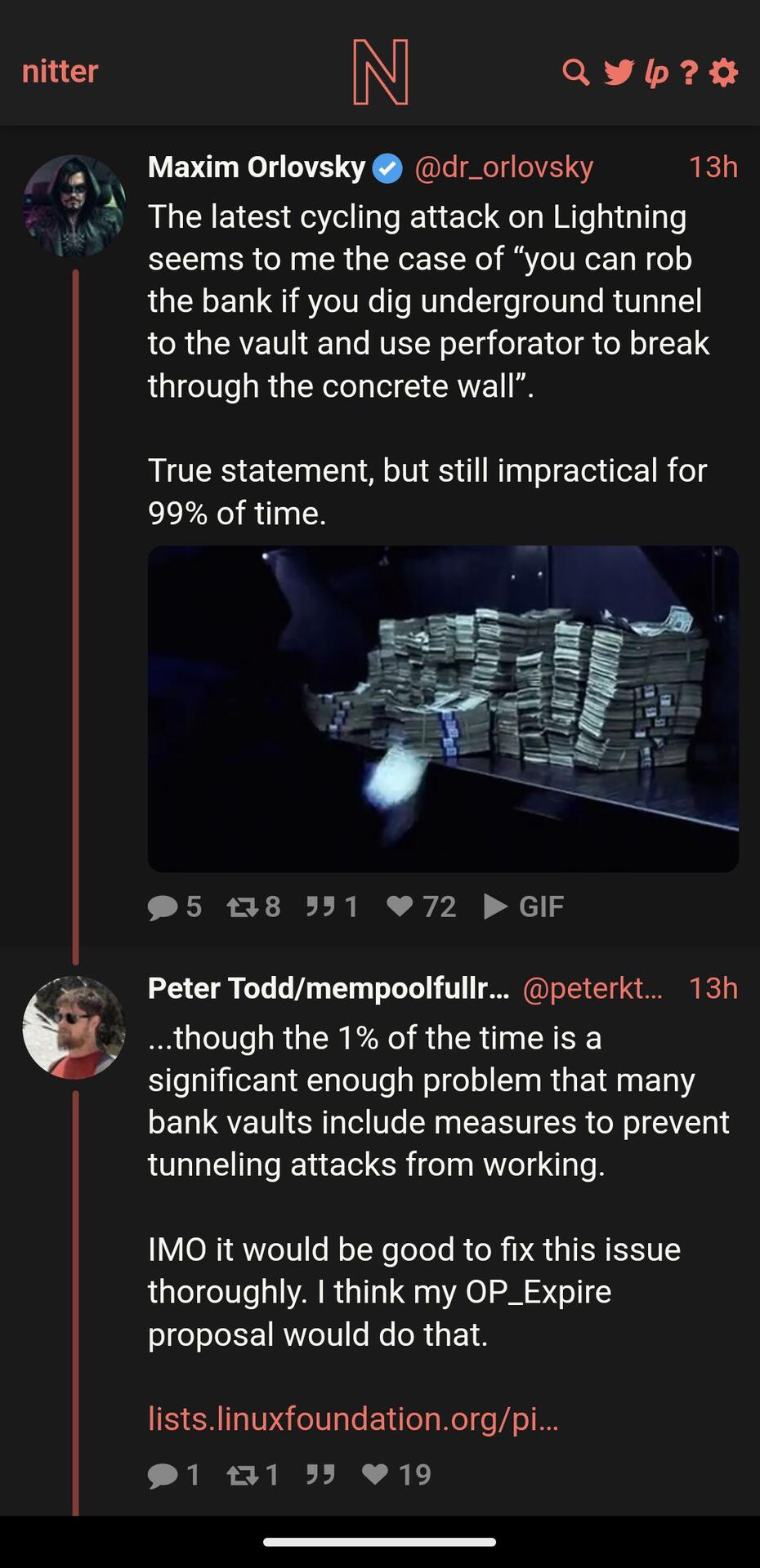
Apparently we may have a good solution to the Lightning Replacement Cycling Attack: https://lists.linuxfoundation.org/pipermail/bitcoin-dev/2023-October/022040.html
How Does a Lightning Replacement Cycling Attack Work - Illustrated Primer
https://www.nobsbitcoin.com/how-does-a-lightning-replacement-cycling-attack-work/
Discussion
Uff 😓 👍
"This attack isn't easy. Pulling it off involves:
- opening two channels with the victim.
- routing a payment through them.
- successfully replacement-cycling the victim's htlc-timeouts for Δ blocks.
- without the victim discovering the htlc-preimage transaction.
Despite that, the attack is also hard to solve completely, explained @mononaut in a thread.
@niftynei also held X Spaces explaining the vulnerability."
What's the best eli5 for the attack and maybe also for the solution if there is one?
My bad, the original link has a pretty good explanation. I only saw the top comment on my feed.
Thread with 2 solutions: https://x.com/peterktodd/status/1716110615607910436
Still refuse to go on X 😂