Is the idea to save the hash publicly on kind0 and then search by it? Because then anyone can just copy the hash and "impersonate" phone numbers. It would be nice to add some proof that they actually control the number.
I’m leaning toward this for the hashed phone number that you could optionally share on your profile so that damus could automatically find all your friends. It would really hard to build a rainbow table for this with a high argon2 security parameter.
What do you think nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z, nostr:npub1n0sturny6w9zn2wwexju3m6asu7zh7jnv2jt2kx6tlmfhs7thq0qnflahe, any other mobile nostr devs ? Should we get a NIP going ? nostr:note1q8kxrrtlat9ezh6evwnqce4mhcqnt6xm5k5vn5xqwmmpeuqa0xusuzl6nc
Discussion
yea that is a problem :/
Sms4sats.com has an API
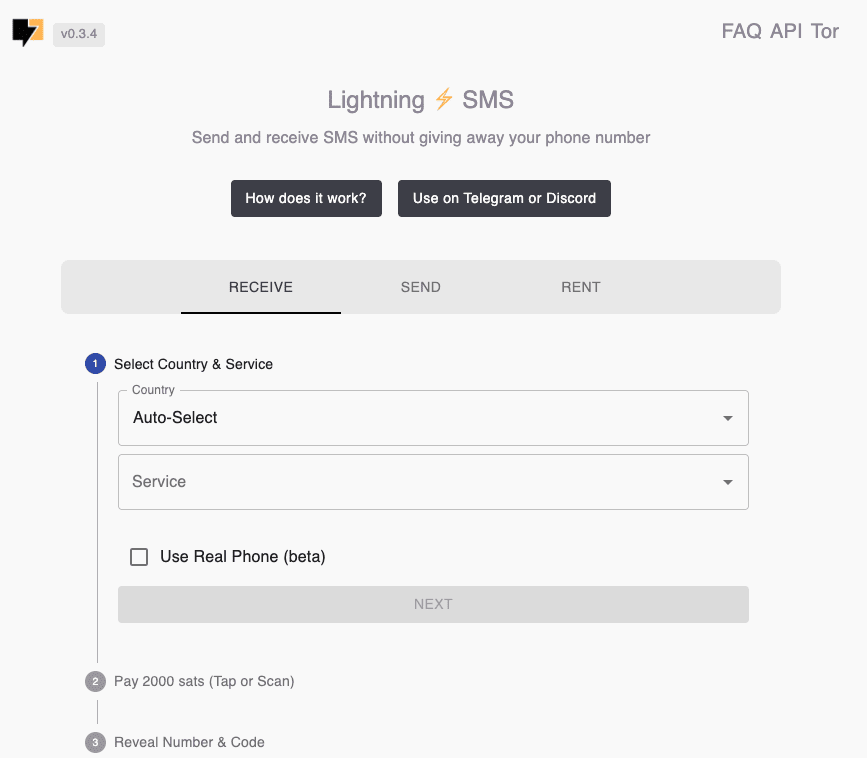
Although signal would carry more privacy benefits, I think, than sms verification
If we rely on a service for verification we might as well do contact lookup via the purple api
I think signal did something with sgx? Could have swore they solved this problem.
What if the hashed phone number is stored as an event signed with a unqiue private key? That private key is stored on the user's behaf by the app which published the event. The app or service that finds matching phone number hashes then publishes a connect request event to the phone numbers public key, signed using the requesting user's private key. The phone number user can then see the connection request, and choose to accept or deny.
I've been thinking about building the general use case for this in AKA Profiles, where badges are always published using a unique private key, allowing badges to be discoverable, but not directly attributable to a user's public key without their permission.



