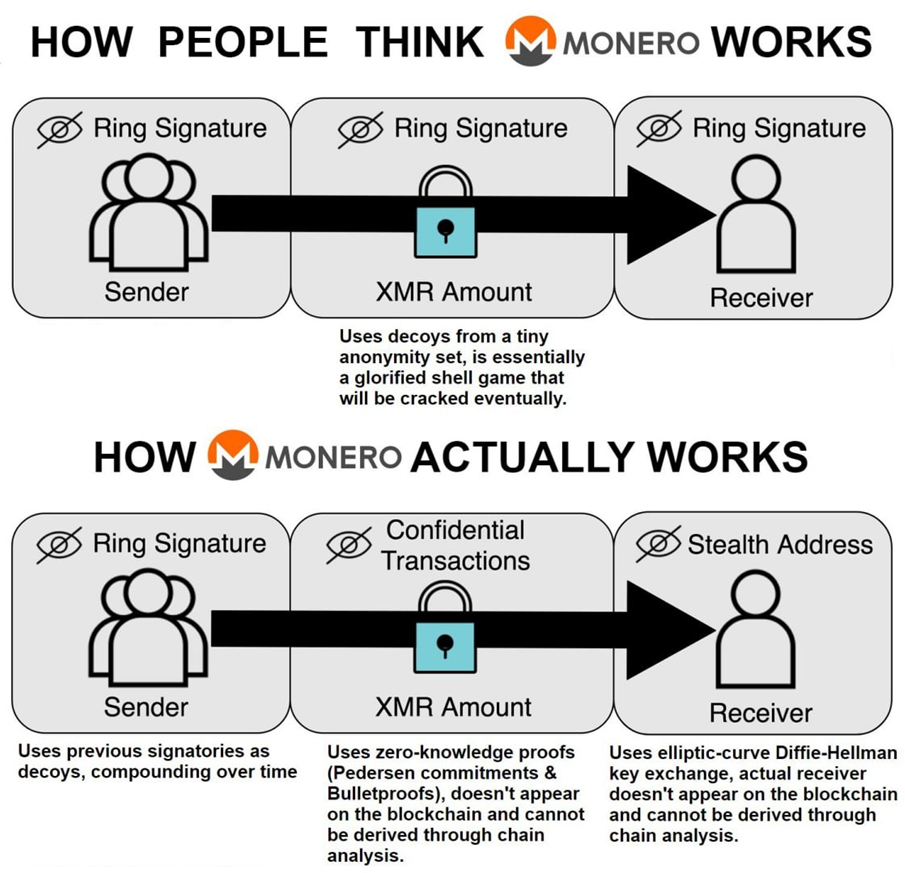
Monero relies on pedersen commitments and range proofs for auditability. Its built on the foundation of sound cryptography from the 80s. True, you cannot just look at the blockchain like Monero and do "simple math" to add everything up.
But then again, what bitcoiner does that? They just run a node and pay no mind just as Monero. No bitcoiner is making sure every new block (all inpus) = (all outputs). So in practice that is a weak point.
RBF has it's own trade offs. Where 0 conf payments use to be pretty safe for small amounts on btc, it makes them way riskier and lowers convienience/useability in that respect.
Monero doesn't only have obfuscation...you are very misinformed sir. Sender is the only part that is obfuscated thru ring sigs. Monero uses ZKPs/encryption for amounts and recievers. There is no connection graph linking senders and recievers. There is no amount analysis either. Simple examples:
Monero: ~6% chance Alice sent $[?] to [?]
Bitcoin Coinjoin:
[Alice, Bob, and/or Carol] sent [$X, $Y, and/or $Z] to [Dave, Eve, and/or Frank]
Encryption > Obfuscation
Monero privacy is much stronger than merely coinjoining where the range of possible amounts and connections is completely available. There is always potential to combine with future data to deobfuscate a coinjoin tx. And it has happened many times.
https://www.wired.com/story/silk-road-bitcoin-seizure-james-zhong/