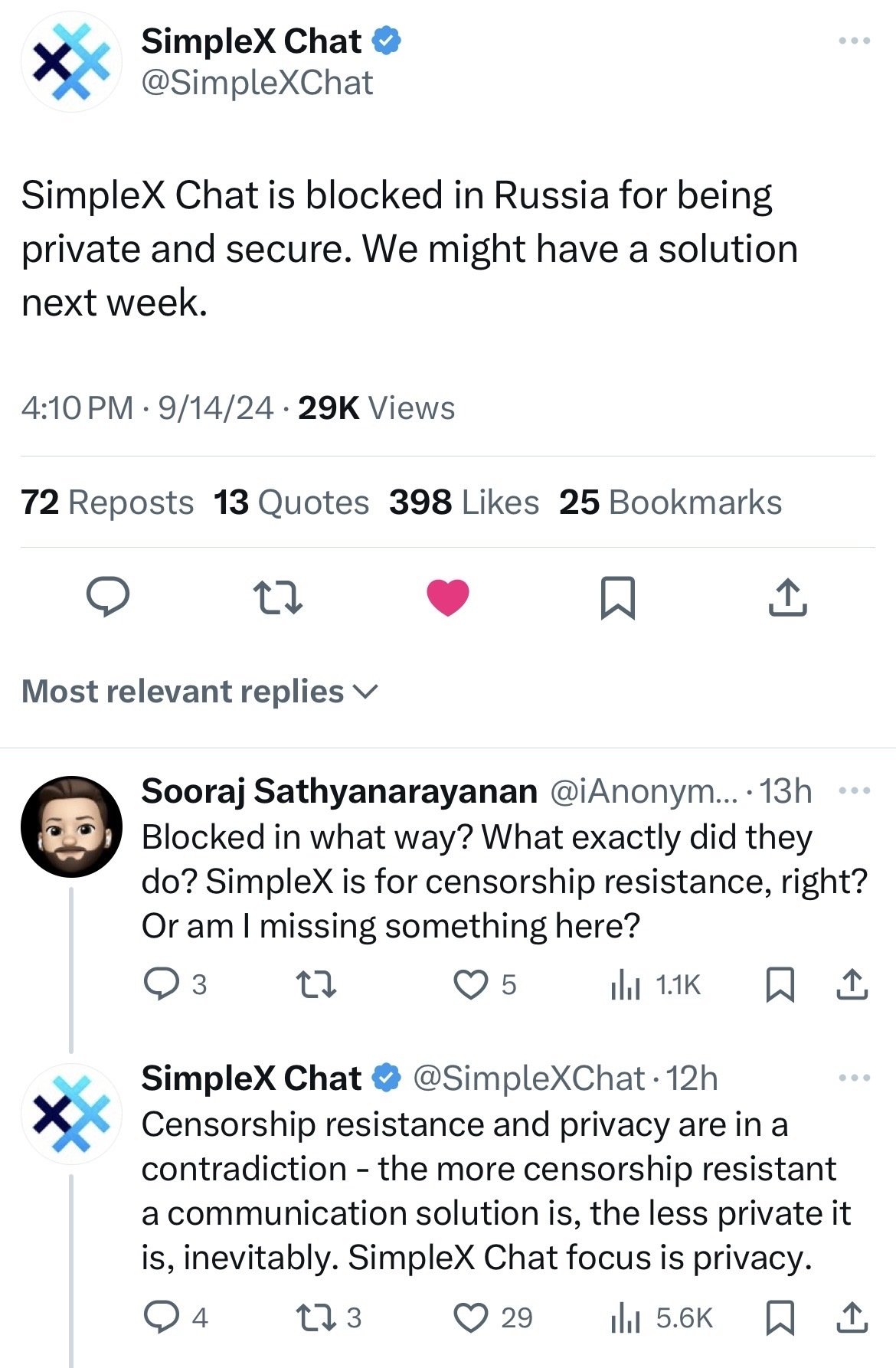
I’d have to read the source code but my guess is since it’s a protocol relying on specific ports and traffic patterns (like BitTorrent) it can be tracked with types of intelligent firewalls and dynamically blocked.
Discussion
Interesting.
Makes sense. That would mean it's not a general tradeoff, but they made problematic design choices.
Likely if SimpleX sends the traffic over Tor or people in Russia used VPNs they might get around the blocks. But the latter would be a temp solution.
In the case of using Tor, their original statement would still be true, wouldn't it? By using Tor, you gain censorship resistance, but you lose privacy by exposing yourself as someone who uses Tor.
Fair point but given that the traffic is completely encrypted at least no one can read what you’re sending. I’m sure there is a technical way to manage the traffic in a block-resistant fashion and maintain privacy at some level but as the SimpleX authors inferred that’s going to be an interesting challenge.
I suppose they're right to some extent, but I think it's possible. Interesting to watch anyway