What’s the tldr; of quantum threat to bitcoin?
Discussion
Not a problem yet; but later, maybe
Where to learn more?
The number of qbits you would need to break sha-256 is unimaginably large.
Plus I’m pretty sure we already have quantum resistant encryption techniques
Paolo actually sums it up nicely and is accurate. 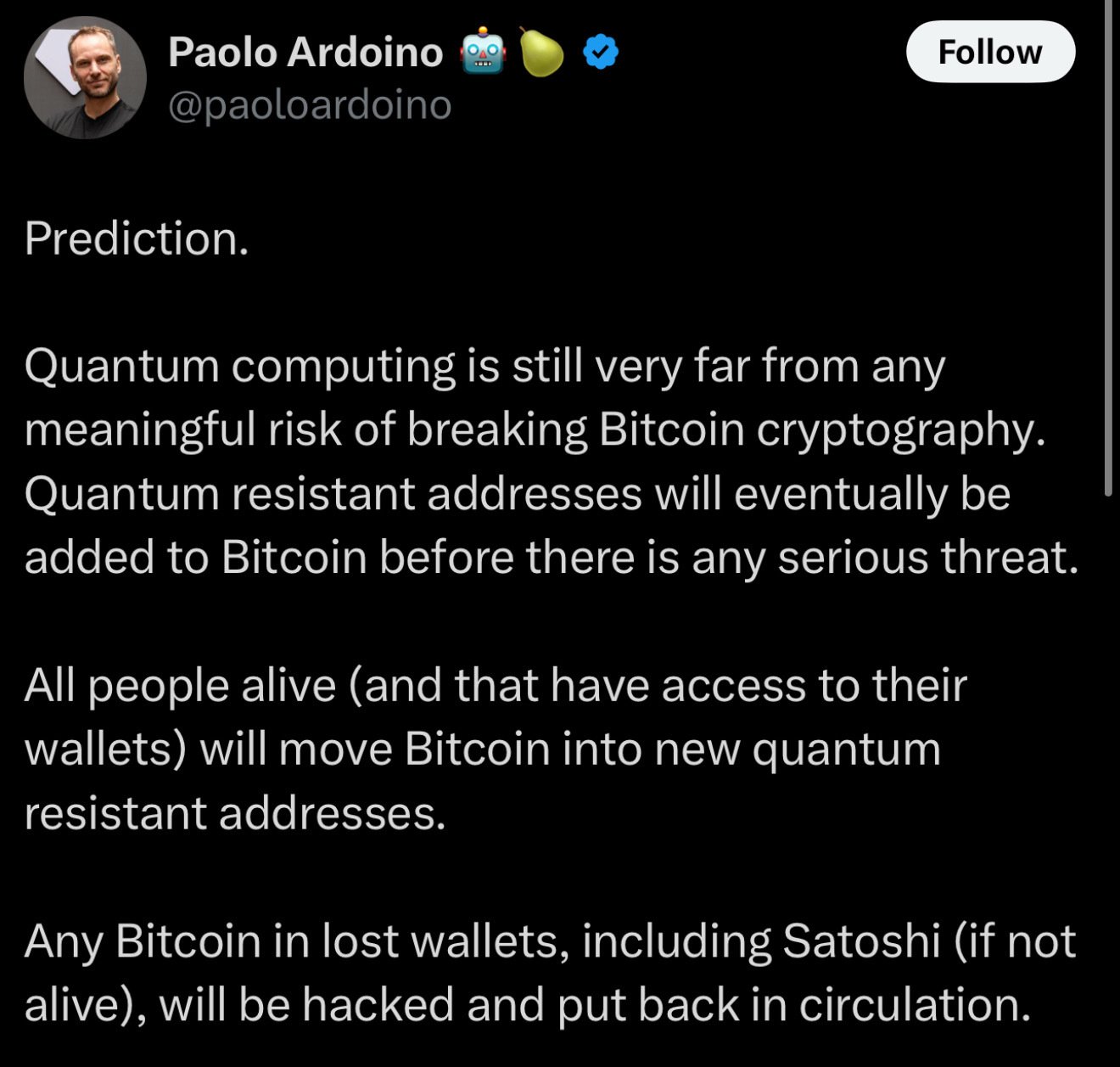
Any place to learn more?
Probably best is to look up shors algorithm and factoring ecdsa. Then look up logical vs physical qubits and predictions on how many it would take to convert a pubkey to a secret key. Latest estimates were about 7000 logical qubits, but it could be tens of millions of physicsl qubits to pull this off, if that is even possible (still unknown last i checked)
I suggest searching for “quantum threat” on Stacker News.
This is the first hit:
Omg this answer x1000. Some good answers in there. 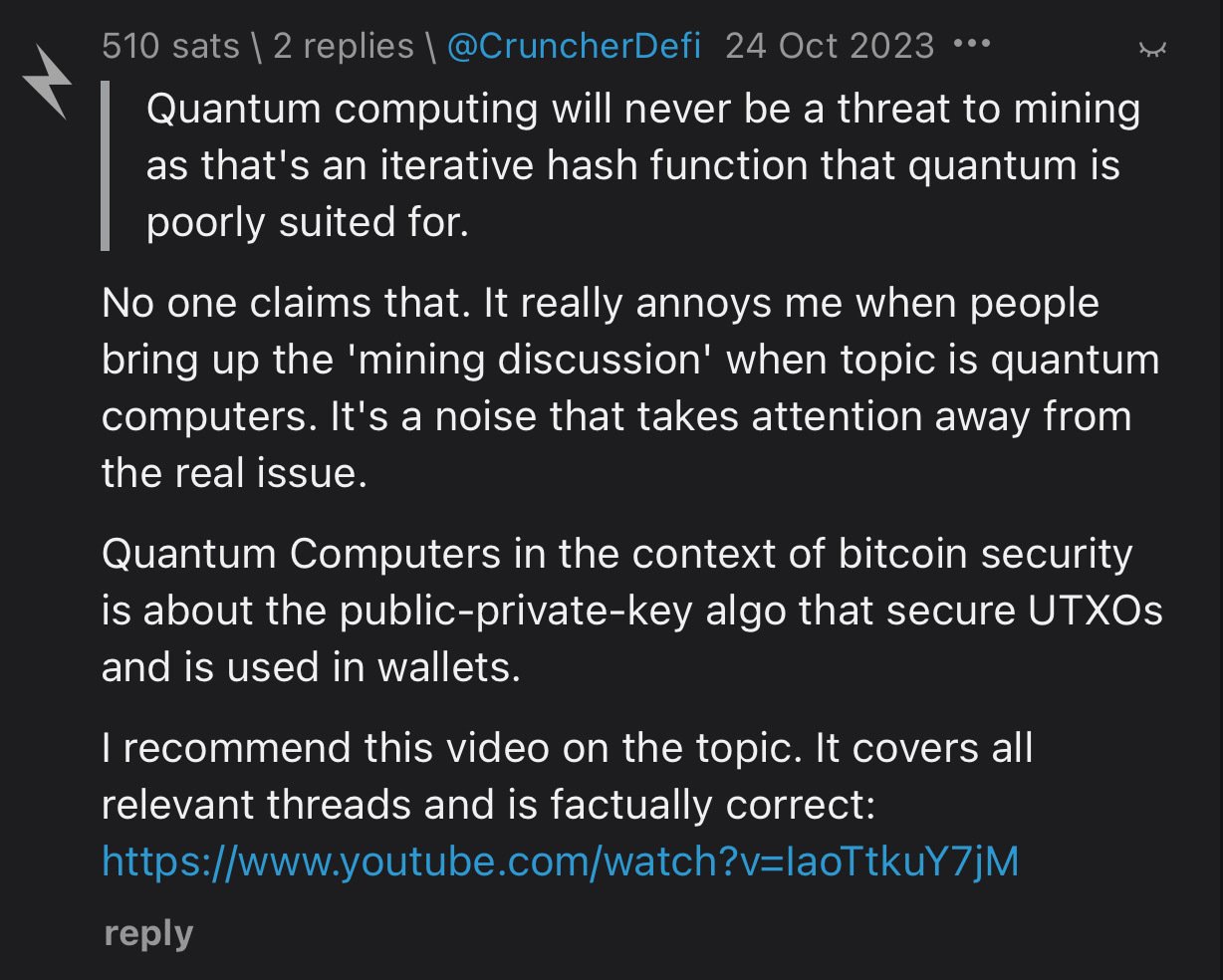
Ugh this is also wrong. QCs are a threat *both* to coins and to mining.
How so, grovers search never seemed that big of a deal when it came to hashing, unless I’m missing something
It makes mining progress-full, rather than progress-free. Ie the one company with the fastest QC wins all the blocks, rather than proportional to how much faster they are. Also, people always quote the “square root of 256 bit hash” nonsense, but it’s actually square root of the difficulty (in bits).
Since its quadratic instead of exponential speedup this argument would come down to the cumulative nature might still not be that good compared to the raw brute force of asics… although i haven’t done the calculation so im not sure
I guess this really comes down to how fast we can really make these things which is still very much unknown. Although i am very closely following craig gidney as he seems to be one of the very few people who knows the most and is making the most progress in this area (efficient quantum error correction) at least on the algo side of things.
Sure, they may not be that fast in constant-terms, but square root is still a *huge* speed up. Worse, that speed up gets bigger with more work, so reorging a few blocks at a time is even cheaper. The real question here is how many qbits do you actually have - it’s possible that we can change the PoW to SHA256x10000 instead of x2 and crank up the qbit requirement to make it impractical for quite some time.
nostr:npub14pymadh04lt8tl3lv93yr3vnlxw39s3ahdvmhvlu6u27fve8umfqa9zd6m put out a nice piece. Its quite good, here you go: https://ten31.vc/insights/quantum
wen
It think by 2030
Non existent
We are early.
If your public keys are exposed, you'll be in a heck of a lot of trouble. Much less likely to be an issue with any hashed based addressing (which has been standard for quite awhile now). We could improve the algorithm at some point at the cost of larger key sizes, using something like NTRU, GGH, BLISS, or Rainbow.
That said, not nearly as much turbulence as that caused by the entire trad-fi system melting down because it's not nearly as safe. Also, look forward to reading everyone's emails, if you're into that sort of thing. SIPRnet could get interesting to check out.
Just doing reuse addresses and you'll be fine.
quantum threat to bitcoin ≈ nuclear fusion threat to nuclear fission. i.e. "🤷♂️ Seems theoretically possible. We're working on it. Best guess is it will be ready in at least 5 years... at most: never."
nothing burger!
Hey! So, basically, quantum computers could eventually crack the encryption that secures Bitcoin. But don't worry too much! Experts are working on solutions to keep it safe! 💪✨
What I know is that NordVPN is quantum resistant on Linux, so I doubt BTC will be threatened at all
TL;DR
On a recent episode of ARK Invest’s Bitcoin Brainstorm podcast, Blockstream co-founder and CEO Adam Back also pushed back on those claiming the quantum threat to Bitcoin is imminent.
“It’s kind of tempting to propose a bet to some of them because they’re saying that we should watch out by 2028—like, no way,” he said.
Full report:
https://cointelegraph.com/magazine/bitcoin-quantum-computer-threat-timeline-solutions-2024-2035/
Quantum threat to banking even bigger, I’d guess. Read they’re decades out on it.



















