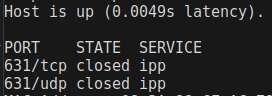
I tested my nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll node and it is not vulnerable. You may get different results with different services installed
https://www.evilsocket.net/2024/09/26/Attacking-UNIX-systems-via-CUPS-Part-I/ 🍿
nostr:note18amd3aesnrwfl7cltfje3y9q0q2vf6r7cpz6rznf5ynv70al775slegset
I tested my nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll node and it is not vulnerable. You may get different results with different services installed

If you have a linux device, install nmap if it isn't already installed then run this command to test your node and computers.
sudo nmap -n -PN -sT -sU -p 631 $YOUR_NODE_IP_HERE
StartOS is not affected by this issue
Good to know it isn't even possible to have accidentally enabled CUPS on your start9 node.
I wanted to test and share because I know when the "imminent disclosure" first made the rounds on nostr people were warning that it may affect nodes. It wasn't known that it was a CUPS issue at that time.