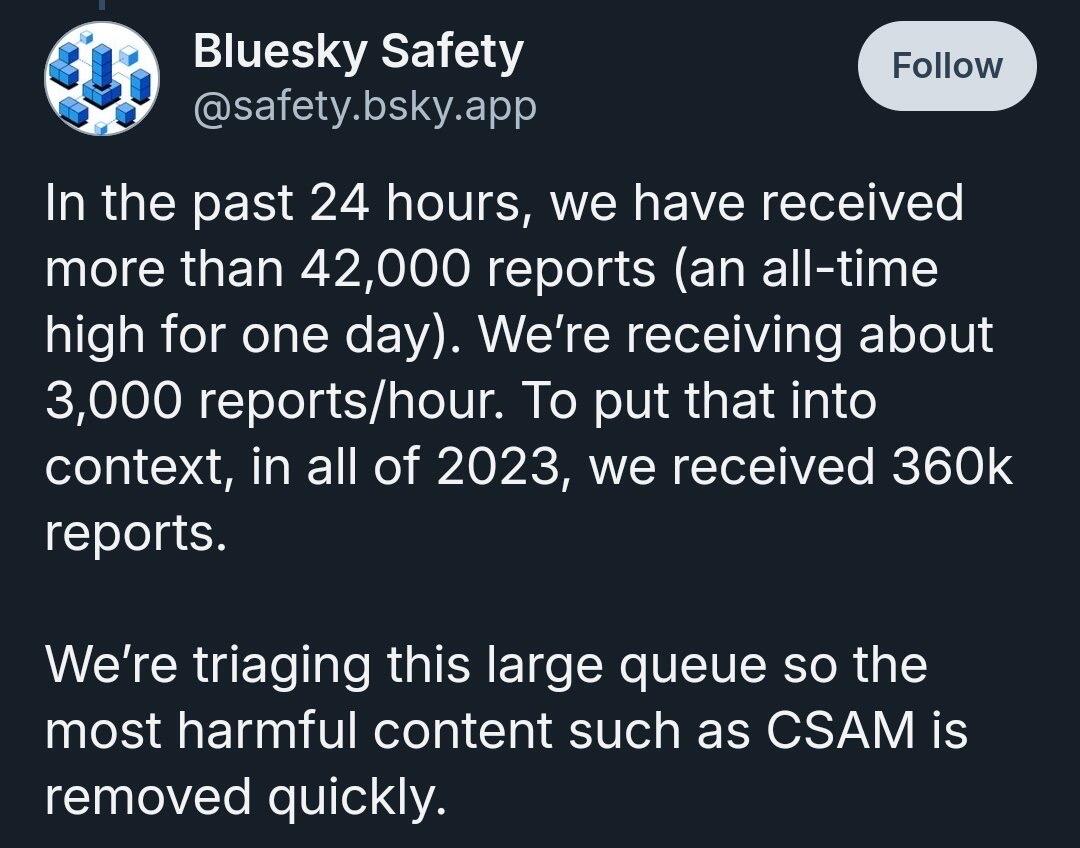
What techniques nostr relays/clients deploy to prevent spreading of csam?
Discussion
It seems to be a combination of reports, WoT, client side and relay filtering. Also pretty stupid to share here with the required cryptographic signing of the crime.
csam?