Could I provably run code in something like that generates an nsec that I never see?
Store your nsec in a secure enclave!
We've spent a big part of 2024 trying to make a reliable non-custodial signer with nsec.app. It hasn't worked out perfectly - remote access to keys stored on a mobile device is still unreliable, especially on iOS.
That's why we got very interested in AWS Nitro Enclaves - h/t nostr:nprofile1qyvhwumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wshszxmhwden5te0deex2mrp0yhxxttnw3jkcmrpwghxuet59uq35amnwvaz7tmjv4kxz7fwdehhxarjvd5x2cmt9ekk2tcpzdmhxue69uhhqatjwpkx2urpvuhx2ue0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qqsgafy9ye4j9p2x8vfmlq6equtpcg4m8ks7v545g0d3f7wwueeq5scudj64l and MapleAI team for inspiration!
The idea is to have an open-source custodial signer and deploy it in an isolated environment that provides attestation for the deployed code. Anyone would be able to reproduce the code build and verify that the signer is running the correct code in a safe environment.
So here it is: https://github.com/nostrband/noauth-enclaved
Each instance of a signer deployed in an enclave announces itself on Nostr. We added some Nostr to attestation provided by AWS - the report is linked to pubkeys of a person building the code image, and a person running it. This way you can choose a signer based on your own preferences.
It's already integrated into nsec.app, go to Settings => Secure enclave and try to upload your keys to the server. The signer API is described in README.
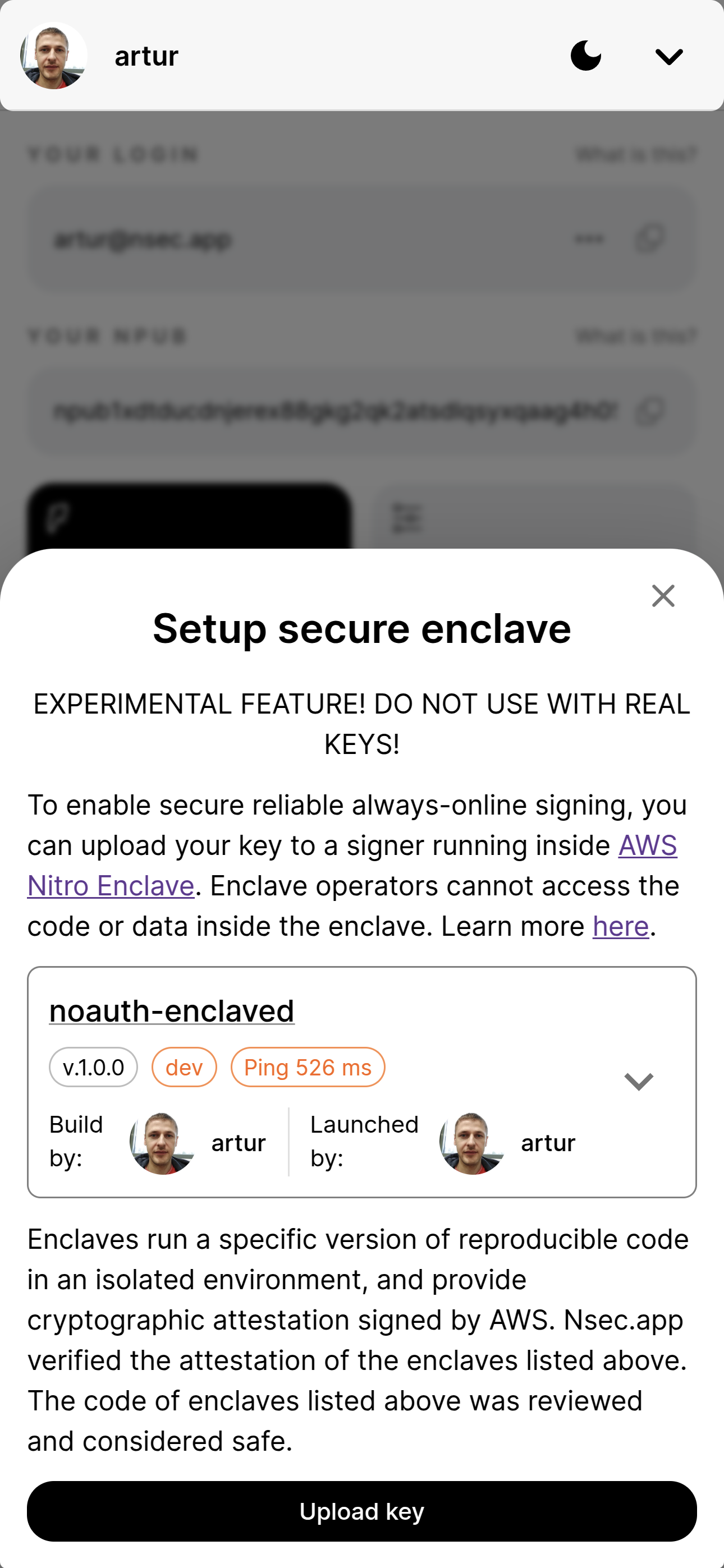
DO NOT deploy your real keys just yet - it's running in a production environment, but the code hasn't been well audited yet. First we need some community members to review the code and reproduce the code image.
The signer can also be used to generate throwaway keys for automated testing of nip46 implementations, check out "generate_test_key" method.
Looking forward to your feedback!
(Signed by my nsec from the enclave)
Discussion
Yes, generate_test_key is an example of exactly that.
Noted ✍️
Has potential that option!!
How would you use it?
To onboard small-ish content creators.
1) create nsec that I don't see
2) publish their stuff + a #communikey around it
3) show them the interactions + zaps
4) hand over*
*eeds a part in the code that you run inside the enclave that lets the onboarded creator export the nsec and proveably tell him this is the first time this happens
Sounds doable on the enclave side. How would creator prove they are who they say they are to the enclave?
Wait, do they need to?
If they can export the nsec, see it its the first that happens, then we don't need a third party, no?
If it's not the first time, well they should ask questions, lol.
So you create an nsec for Taylor Swift and start reposting her insta pics on nostr, those get zapped, eventually you tell her about those sats and invite to take over the nsec. Is that the set up? Wouldn't you want to prove to enclave, somehow, that it's her? Otherwise someone could front-run her?
Also Taylor Swift can sue you out existence for that, lol. Any creator can.
I said small-ish creators.
Not mind-controlled slaves acting on the world stage.
That's a non-starter for any creator of any size. You'd need an explicit contract with them first allowing you to use their image in this way. If not even a tiny creator could sue you for a lot and win.
The creators that care about their IP are :110percent: the wrong ones to onboard.
Wait wait wait, I'd have credentials for accessing the enclave, right?
The point is to pass on those credentials and not the nsec.
Also, if the service provider tries to rug us than we can still see that someone already exported the nsec.
Ah got it, you pass the bunker url to creator, and they try to export and that only succeeds once. Sounds good!
Yup :Check:
If I made a noob error in that logic, tell me por favor :prayinghands:
If not, I can use this!
Sounds fine, will see what I can do. One issue at this point is that if enclave is restarted, all the state is gone, so storage of long term assets is a challenge, especially while it's not yet production ready. But we will solve that, so eventually your idea is gonna work.
Ow damn, yeah didn't think of that, of course.
Yeah, no stress. Def don't need this tomorrow :winkwithtongue:


