nostr:nprofile1qqs04xzt6ldm9qhs0ctw0t58kf4z57umjzmjg6jywu0seadwtqqc75spp3mhxue69uhkyunz9e5k7qgjwaehxw309ahx7um5wgh8vvrv9e5k7qg4waehxw309ahx7um5wghxxmmfdehhxtnfduq3vamnwvaz7tmjwdekccte9ehx7um5wghxuet5qyf8wumn8ghj7un9d3shjtnxxaazu6t0qyw8wumn8ghj7mn0wd68ytfsxyhxymmvwshx7cnnv4e8vetjqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszynhwden5te0wp6hyurvv4cxzeewv4esz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyxhwumn8ghj7mn0wvhxcmmvqyv8wumn8ghj7am9d33k7mt99ehx7um5wgh8w6twv5q3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqzxnhwden5te0wfjkccte9eh8xetrvf6ku6m9wghxxmmdvfm6mp building out my nsecbunker integration, do you have a tutorial or documentation I can follow? So far I'm just trying to reverse engineer the protocol and getting stuck. Right now I'm using an ephemeral key to sign events (which I assume is the "app" key you approve requests for?), and using the pubkey I want to sign the event for as the #p tag and destination of the nip04 encrypted contents. I'm also sending events to relay.nsecbunker.com for testing. But currently the response I'm getting is just the same event I sent, complete with the signature I gave it. Any tips?
Discussion
I’m AFK, but I’ll send you my diff in the morning (or see my fork; it’s running with source maps on and I only changed one file plus the modal so should be super easy to find, just search for ndk 😅)
But yeah, generate one local key (app) which is the one you’ll be approving. That key generates the events and sends it to the bunker to get the signature back.
I have pending to implement a publish_event to sign+publish to save on the round trip too.
sir, took some more time to get around to it but here it is:
quick and dirty implementation of nsecbunker
key points:
* uses a separate relay connection (I think it makes more sense to have the signer connectivity separate since it's useless to push the signing events to pretty much all relays except the ones where nsecbunker is listening to)
* local key, generated locally
https://github.com/coracle-social/coracle/commit/c2cf06ee0101d46cbb08576a4b03fc8c1a7fc3f3
Is there a nip or standard to make it easy to connect with a self hosted nsecBunker, maybe add the relay to the token that is copy pasted?
that's the beauty; you don't connect to the nsecbunker
you discover it
that's why you can easily run a bunker on your umbrel without opening any ports, without fiddling with tor, without any bullshit; it just works
all you need to find the bunker that will serve your npub is that... your npub
Can a Bunker serve multiple npubs with different people granted access to different npubs?
I’m thinking about a company that might have multiple social media “presences”.
yes
nsecBunker already can do that
if you buy/run one now you can already load as many keys as you want 😉
Is this a security vulnerability? IOW, if you log out of Coracle, the browser still has write access via nsecbunker if the same pubkey is re-entered. So you're logged out, but it's trivial to log back in without re-establishing permission. It seems to me the key should be re-generated every login.
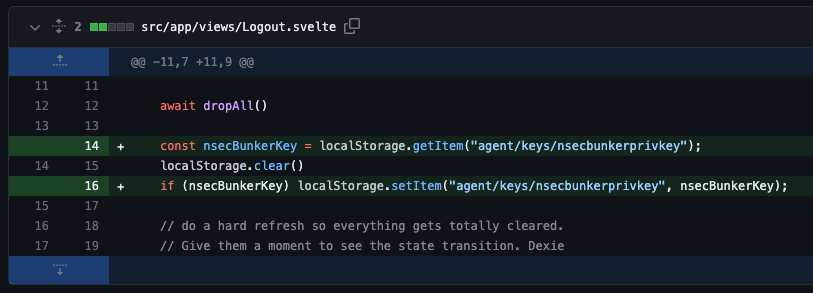
I agree; if you logout from coracle the private key should be destroyed
How does the token work? Do you need that every time, or is that just intended to bypass manual authorization? IOW, authentication depends on the approved app key, right?
Just for manual authorization; the token tells the bunker “I’ve been preauthorized”
Once used you can’t redeem it anymore so you should not save it. Just save the npub from the token



