📢👀 nostr:note1xgg3ltnfapp05v37s7dx4z23hjgxnqfudycatl0q0yrdkf5ty6fsvvjxja
I just created a Python 'safebox' component where it can connect to any relay for proof storage and any mint for issuing/redeeming tokens.
The safebox can receive funds via the mint and send funds to any lightning address.
The only thing 'local' for the safebox is the nsec, which you can pick up and take anywhere. So long as you know the nsec and know the relay(s) you have access to your ecash.
This is based on NIP-60/61 by nostr:nprofile1qqs04xzt6ldm9qhs0ctw0t58kf4z57umjzmjg6jywu0seadwtqqc75spzpmhxue69uhnzdps9enrw73wd9hszynhwden5te0wp6hyurvv4cxzeewv4eszynhwden5te0wfjkccte9enrw73wd9hsxv8qkt and I am adapting for my
own backend requirements of a 'custodial wallet' for a payment system.
What is wild is that the 'wallet' instance can operate and exist contemporaneously across multiple jurisdictions.
Anyway, still early days. Just excited to share my progress and insights. If you want more details, please DM me.
nostr.watch is cool
I can't say enough good things about silent.link I have it on my secondary phone and spend in the single dollars per month for data at no obligation. It made me realize how much we get ripped off by the domestic telcos.
Your brain is a relay.
nostr:npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka This would be easy to test. Auto-write a note to each relay and then follow with a deletion event and then mark the relays 🔴🟢
I might try that, later.
In the #nostr world you need work with a new set of assumptions. For example how to interact with non-cooperative relays. Either avoid them completely, or not publish anything that compromise you.
Awesome! Thanks for sharing. We’ll be going to British Columbia shortly. Promise to send along some pics.
In the late 1960s, my mother went to Woodstock since she knew a doctor and pretended to be a nurse in his medical tent.
In the early 1970s, she went to travel Europe as a backpacker for over a year. And then, she traveled to Morocco through Gibraltar, and Morocco had a coup. https://en.wikipedia.org/wiki/1971_Moroccan_coup_attempt
So my mom got stuck there with little money and few exits. There was a government agent named Mohamed that courted her for a while and would pay her daily; he wanted to marry her and leave. She eventually managed to escape that situation, by befriending a Canadian pot dealer. He was chill, and gave her funds and said to pay him back once she gets home. So she stabilized and was able to get a flight home.
My mother and I are opposite personalities. She mostly didn’t raise me; my father did. And yet in every picture, her right ear is visible but never her left. To this day, I get jokes online about never showing my left ear. Every picture. People say it might not exist.
It’s fun how that works. Maybe I’ll show my left ear only for Nostr.

Great story! If you need help, ask a Canadian pot dealer.
Yup, just posted similar thoughts two seconds ago. I am currently building an ecash wallet where everything is stored as #nostr events.
The only bitcoin stuff that I still pay attention to now is macro from Lyn Alden. I pay attention to ecash and very interested in how that might change the payments game.
By far, the most interesting thing is how #nostr could evolve alongside bitcoin into a new infrastructure.
You could ask the mint to flag one of your proof secrets. If it gets redeemed, it could send a notification. Honestly, I find this a bit scary - pixie dust tokens - and it has got me thinking that anyone should be able to re-blind a proof before they redeem it./cc nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg
I’d characterize this as an attack where a mint and a user can collude to entrap another user. In brief, a user can flag to the mint one of their secrets, and when this secret gets swapped or redeemed, a notification occurs. To mitigate this, the receiver of token(secret) should be able to re-blind. I think this should be pretty straightforward operation. Right now we can take the signature: _C transform to C. Any receiver of a token should be able to transform to C_ with an entirely new secret before presenting for redemption.
You could ask the mint to flag one of your proof secrets. If it gets redeemed, it could send a notification. Honestly, I find this a bit scary - pixie dust tokens - and it has got me thinking that anyone should be able to re-blind a proof before they redeem it./cc nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg
Very cool. I am currently building a Python version of a NIP-60 wallet which I plan to bolt in the back end of my Lightning payment system. I have the basics working and should have something to show in the next few weeks. This approach eliminates the need for the service to store any personal info, including proofs used for lightning payment. Thanks to nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft for this great idea. /cc nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
Indispensable guide. 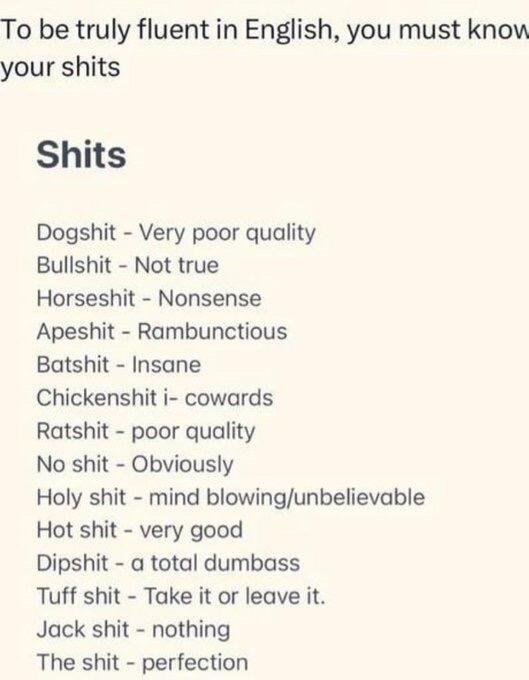
This was the funniest find when I was in #Madeira. Doesn't quite translate well for an English #nostr speaker #controlretard

Sorry, but watching Olympic breakdancing is a painful experience.
Riding through the Experimental Farm. 

 nostr:note15747tth7pcdtypasme5kvx34zss2tt7mpclnmv4tzerxdv4l3puqwkxp4q
nostr:note15747tth7pcdtypasme5kvx34zss2tt7mpclnmv4tzerxdv4l3puqwkxp4q