La Terza Capture The Flag (CTF) di RHC è Pronta! Tra AI, Reti 4G e Stati Nazionali. Sei pronto?
Red Hot Cyber, come ogni anno all’interno della RHC Conference, ospiterà la nuova Capture The Flag realizzata in collaborazione con CyberSecurityUP e Hackmageddon e Fondazione Bruno Kessler. Si tratta dell’arena della Cyber Warfare Ibrida, dove solo i più astuti e determinati hacker etici riusciranno ad emergere.
Questa volta, la sfida sarà più realistica e coinvolgente che mai.
Sarai all’interno di una operazione militare orchestrata da uno stato ostile ai danni dello stato MINZHONG, una tranquilla repubblica orientale che basa la sua prosperità sul commercio di beni alimentari e agricoli. La tua operazione inizierà da una semplice parola: Supply Chain.
Il tuo obiettivo: come di consueto prendere il controllo di tutto, un pezzo alla volta!
La Supply Chain: lo scenario più temuto nella Cybersecurity di oggi
Sì, avete capito bene: questa volta il protagonista è il tanto discusso attacco alla supply chain realizzato in collaborazione con CyberSecurityUP. Una tecnica che negli scenari attuali rappresenta una delle minacce più insidiose per le grandi aziende. Gli attaccanti non colpiscono direttamente il bersaglio principale, ma sfruttano fornitori e partner connessi alla rete per ottenere un primo accesso. Da qui, con tecniche di pivoting e movimenti laterali, è possibile infiltrarsi progressivamente in infrastrutture critiche, eludendo controlli di sicurezza e aumentando il raggio d’azione dell’attacco.
Tutto inizia con un punto di accesso apparentemente marginale: una terza parte, un piccolo fornitore, magari un’azienda di supporto IT o un partner logistico, connesso alla rete del bersaglio. Basta un errore umano, una configurazione errata o una credenziale esposta per fornire agli attaccanti il foothold necessario. Da quel momento, l’obiettivo non è solo mantenere la persistenza, ma esplorare la rete interna, comprendere la struttura dell’infrastruttura e identificare asset sensibili da compromettere.
Il vero gioco inizia quando si passa all’azione: l’escalation dei privilegi, l’uso di tunnel cifrati per evitare il rilevamento, il movimento tra sistemi governativi e servizi critici. Gli attaccanti si muovono silenziosamente, sfruttando connessioni fidate per propagarsi senza destare sospetti. La supply chain diventa così il tallone d’Achille delle organizzazioni, dimostrando come una singola vulnerabilità esterna possa compromettere un’intera infrastruttura.
Gli obiettivi della Capture The Flag 2025
Come ogni anno, le infrastrutture della capture the flag sono realizzate interamente da Red Hot Cyber e i suoi partner tecnologici. Questo anno gli obiettivi strategici in questa nuova capture the flag, saranno i seguenti:
Suppy Chain: Viola il fornitore di terze parti colpevole di una bassa postura cyber
Siti governativi: Viola i portali ufficiali e i sistemi ministeriali.
Infrastrutture critiche: Viola la rete telefonica 4G, La banca, la Rete Idrica, L’ospedale e altro ancora.
Social Engineering: Crea email ed effettua Spear Phishing per convincere il CEO dell’azienda energetica a fornirvi dati di intelligence
Ogni flag conquistata sarà un passo in più verso la vittoria.
Ma non tutto potrà essere fatto online
La sfida si fa sempre più reale di fronte all’operatore nazionale telefonico, una rete 4G radiomobile che andremo a dispiegare presso il teatro italia che dovrà essere violata per conquistare flag fisiche. Ma non sarà solo un gioco di codice e exploit. Per prendere flag fisiche, dovrete anche violare telecamere, reti telefoniche, lucchetti e disinnescare bombe e sfruttare i punti deboli della sicurezza fisica.
Location per le operazioni cibernetiche standard : Online
Location per le operazioni cibernetiche in prossimità: Teatro Italia (Secondo Piano)
Quest’anno, gli scenari fisici saranno differenti rispetto alle edizioni precedenti, offrendo nuove sfide e ambientazioni inedite. Per questa edizione, stiamo lavorando su una serie di prove esclusive, progettate per mettere alla prova le capacità dei partecipanti in un contesto realistico e immersivo.
Tutte le sfide saranno disponibili esclusivamente presso il Teatro Italia, che, a differenza dello scorso anno, metterà a disposizione non solo la terza balconata, ma anche l’intera sala al secondo piano per tutta la durata della Capture The Flag. Questo garantirà spazi più ampi rispetto alla scorsa edizione e un’esperienza di gioco ancora più coinvolgente. Alcune delle challenge in prossimità saranno:
Disinnesca la bomba
Viola la rete 4G
Tre metri sopra al cielo
Accedi alla banca di stato
L’operatore radiomobile 4G di MINZHONG
All’interno degli scenari fisici, quest’anno porteremo una vera rete radiomobile 4G, offrendo un ambiente realistico e avanzato per test di sicurezza sulle telecomunicazioni. I partecipanti avranno l’opportunità di interagire con una infrastruttura di rete, mettendo alla prova le proprie competenze nell’analisi e nell’attacco di sistemi di telecomunicazione in un contesto controllato e altamente tecnico.
L’accesso all’IMS di fonia e a internet sarà una componente chiave di questa esperienza, permettendo ai partecipanti di sperimentare in prima persona le vulnerabilità e le criticità delle reti mobili. L’obiettivo è quello di esplorare i potenziali punti deboli delle reti LTE, comprendere i meccanismi di autenticazione e propagazione del segnale, e individuare eventuali falle di sicurezza che potrebbero essere sfruttate da un attaccante reale.
Porteremo una rete 4G dedicata, fornendo ai partecipanti delle apposite SIM per connettersi al nostro operatore e testare direttamente la sicurezza della rete. Durante la challenge, sarà possibile raccogliere le flag violando la Radio Access Network (RAN) e propagarsi verso la core network e gli elementi di rete. Questo scenario offrirà un’esperienza unica e immersiva, con la possibilità di mettere in pratica tecniche avanzate di attacco e difesa in un ambiente realistico.
Nota Bene: L’irradiazione della rete radiomobile avverrà in prossimità, con un raggio indicativo di circa 7/10 metri, garantendo un’area di sperimentazione sicura e controllata.
Intelligenza artificiale e phishing
All’interno della competizione dovrete anche affinare le vostre abilità di social engineering. Non sempre è necessario un exploit o una vulnerabilità, potrebbe bastare convincere qualcuno a cliccare sul link sbagliato. Avrete infatti la possibilità di hackerare un fornitore di energia nazionale tramite vere e proprie campagne di phishing mirate a rubare dati sensibili per lo svolgimento delle operazioni statali.
A differenza delle altre sfide non dovrete fare affidamento su delle vulnerabilità o mancate configurazioni, bensì vi sarà richiesto di recuperare informazioni e indizi per creare delle mail convincenti. All’interno delle mail potrete includere domande, link o allegati malevoli, ma il risultato finale dipenderà dalle vostre abilità nel rendere la mail credibile. Per recuperare tutte le flag nascoste nell’infrastruttura sarà fondamentale anche la capacità di interpretare le informazioni recuperate dai vari dipendenti, ciascuno con la propria personalità e con i propri dispositivi aziendali.
Questa parte sarà gestita da un sistema automatizzato basato su Intelligenza Artificiale generativa sviluppato dal Centro per la Sicurezza Informatica della Fondazione Bruno Kessler (FBK) di Trento, in collaborazione con l’Università degli Studi di Trento. L’uso dell’IA non si limita solo a rispondere alle mail ricevute, ma alla totalità dell’interazione con il contenuto dei messaggi ricevuti. Tutte le parti dell’infrastruttura saranno create e gestite attraverso un sistema di Infrastructure as a Code (IaaC). Questo sistema sarà reso disponibile tramite un dominio pubblico, in modo da consentire la partecipazione sia ai team fisicamente al Teatro Italia che a quelli remoti. I dati raccolti dalla CTF saranno utilizzati in maniera aggregata e anonima per scopi di ricerca.
Nota bene: Per la durata della competizione sarà messa a disposizione una VPN al fine di rendere possibile l’uso di dispositivi personali come “server malevoli”: ciascun team avrà a disposizione un singolo utente per l’autenticazione.
Il testing della soluzione è stato svolto tra la Fondazione Bruno Kessler (FBK) di Trento e il team di HackerHood di Red Hot Cyber.
Iscrizioni alla Capture The Flag
La CTF avrà inizio con l’accoglienza presso il teatro Italia alle 15:00 dell’8 di Maggio e terminerà orientativamente alle 17:00 del giorno 9 Maggio. Le «Flag Fisiche» questo anno saranno disponibili presso il Teatro Italia per entrambe le giornate.
Tutti i partecipanti dovranno registrarsi all’indirizzo redhotcyber.com/ctf.redhotcybe… (al momento non ancora disponibile) e per accedere al teatro Italia per le flag fisiche, dovranno effettuare la registrazione all’evento dell’8 Maggio su eventbrite: rhc-conference-2025-workshop.e…. Di seguito il programma dell’evento ospitato all’interno della Red Hot Cyber Conference 2025:
Giovedì 8 Maggio ore 15:00 : Per i partecipanti alle «flag fisiche», Check-in presso il teatro Italia (necessaria la registrazione su Eventbrite)
Giovedì 8 Maggio ore 15:20 : Check in presso la sala adibita alla Capture the Flag al secondo piano entrando sulla destra (Necessaria la registrazione su CTFD)
Giovedì 8 Maggio ore 15:30 : Avvio della CTF
Giovedì 8 Maggio ore 15:30 : Avvio delle «flag fisiche» in collaborazione con CyberSecurityUp e Hackmageddon.world;
Venerdì 9 maggio ore 17:00 : Chiusura della Capture The Flag
Gli organizzatori dell’evento accoglieranno i team e forniranno informazioni e supporto tecnico-organizzativo. Una chat Discord sarà inoltre disponibile sin dall’avvio della competizione sul sito della CTF per dialogare con gli organizzatori.
Il supporto on-site e on-line sarà attivo dalle 15:30 alle 20:00 del 9 Maggio e dalle 10:00 alle 17:00 del 9 Maggio.
Cosa occorre portare per le flag fisiche
Si raccomanda ai partecipanti che verranno presso il teatro Italia di dotarsi di:
laptop e cavo di alimentazione (inclusi adattatori se necessari);
ciabatta multi-presa;
Prolunga di 5 metri;
Smartphone connesso ad internet;
Dongle Bluetooth (se non supportato dal computer portatile);
Dongle Wi-Fi (se non supportato dal computer portatile);
Dispositivo NFC;
SDR solo in modalità RX.
Smartphone 4G rottato compatibile con VoLTE (consigliata distribuzione lineageos)
I partecipanti sono liberi di utilizzare qualsiasi software o attrezzatura a loro scelta (ad esempio disassemblatori, Kali, macchine virtuali, schede SD, proxmark…) purché non danneggino i target, l’infrastruttura o gli altri partecipanti (vedi sezione Norme di comportamento).
Il Regolamento
Per ulteriori informazioni vi rimandiamo alla lettura del regolamento della capture the flag che trovate a questo indirizzo online
Buona caccia a tutti!
L'articolo La Terza Capture The Flag (CTF) di RHC è Pronta! Tra AI, Reti 4G e Stati Nazionali. Sei pronto? proviene da il blog della sicurezza informatica.




Here’s A Spy Movie-Grade Access Card Sniffing Implant
Some of our devices look like they’re straight out of hacker movies. For instance, how about a small board you plant behind an RFID reader, collecting access card data and then replaying it when you next walk up the door? [Jakub Kramarz] brings us perhaps the best design on the DIY market, called The Tick – simple, flexible, cheap, tiny, and fully open-source.
Take off the reader, tap into the relevant wires and power pins (up to 25V input), and just leave the board there. It can do BLE or WiFi – over WiFi, you get a nice web UI showing you the data collected so far, and letting you send arbitrary data. It can do Wiegand like quite a few open-source projects, but it can also do arbitrary clock+data protocols, plus you can just wire it up quickly, and it will figure out the encoding.
We could imagine such a board inside a Cyberpunk DnD rulebook or used in Mr Robot as a plot point, except that this one is real and you can use it today for red teaming and security purposes. Not to say all applications would be NSA-catalog-adjacent pentesting – you could use such a bug to reverse-engineer your own garage door opener, for one.
hackaday.com/2025/03/03/heres-…
 ?w=800
?w=800
Deep Space DX Hack Chat
Join us on Wednesday, March 5 at noon Pacific for the Deep Space DX Hack Chat with David Prutchi!
In the past 70-odd years, the world’s space-faring nations have flung a considerable amount of hardware out into the Void. Most of it has fallen back into Earth’s gravity well, and a lot of what remains is long past its best-by date, systems silenced by time and the harsh conditions that rendered these jewels of engineering into little more than space flotsam.
Luckily, though, there are still a few spacecraft plying the lonely spaces between the planets and even beyond that still have active radios, and while their signals may be faint, we can still hear them. True, many of them are reachable only using immense dish antennas.
Not every deep-space probe needs the resources of a nation-state to be snooped on, though. David Prutchi has been listening to them for years using a relatively modest backyard antenna farm and a lot of hard-won experience. He’s been able to bag some serious DX, everything from rovers on Mars to probes orbiting Jupiter. If you’ve ever wanted to give deep space DX a try, here’s your chance to get off on the right foot.
Our Hack Chats are live community events in the Hackaday.io Hack Chat group messaging. This week we’ll be sitting down on Wednesday, March 5 at 12:00 PM Pacific time. If time zones have you tied up, we have a handy time zone converter.
hackaday.com/2025/03/03/deep-s…
 ?w=190&h=174
?w=190&h=174
 ?w=800
?w=800
12VHPWR Watchdog Protects You From Nvidia Fires
The 12VHPWR connector is a hot topic once again – Nvidia has really let us down on this one. New 5080 and 500 GPUs come with this connector, and they’re once again fire-prone. Well, what if you’re stuck with a newly-built 5080, unwilling to give it up, still hoping to play the newest games or run LLMs locally? [Timo Birnschein] has a simple watchdog solution for you, and it’s super easy to build.
All it takes is an Arduino, three resistors, and three thermistors. Place the thermistors onto the connector’s problematic spots, download the companion software from GitHub, and plug the Arduino into your PC. If a temperature anomaly is detected, like one of the thermistors approaching 100C, the Arduino will simply shut down your PC. The software also includes a tray icon, temperature graphing, and stability features. All is open-source — breadboard it, flash it. You can even add more thermistors to the mix if you’d like!
This hack certainly doesn’t just help protect you from Nvidia’s latest creation – it can help you watch over any sort of potentially hot mod, and it’s very easy to build. Want to watch over connectors on your 3D printer? Build one of these! We’ve seen 12VHPWR have plenty of problems in the past on Nvidia’s cards – it looks like there are quite a few lessons Nvidia is yet to learn.
hackaday.com/2025/03/03/12vhpw…
 ?w=800
?w=800
Mobile malware evolution in 2024
These statistics are based on detection alerts from Kaspersky products, collected from users who consented to provide statistical data to Kaspersky Security Network. The statistics for previous years may differ from earlier publications due to a data and methodology revision implemented in 2024.
The year in figures
According to Kaspersky Security Network, in 2024:
A total of 33.3 million attacks involving malware, adware or unwanted mobile software were prevented.
Adware, the most common mobile threat, accounted for 35% of total detections.
A total of 1.1 million malicious and potentially unwanted installation packages were detected, almost 69,000 of which associated with mobile banking Trojans.
The year’s trends
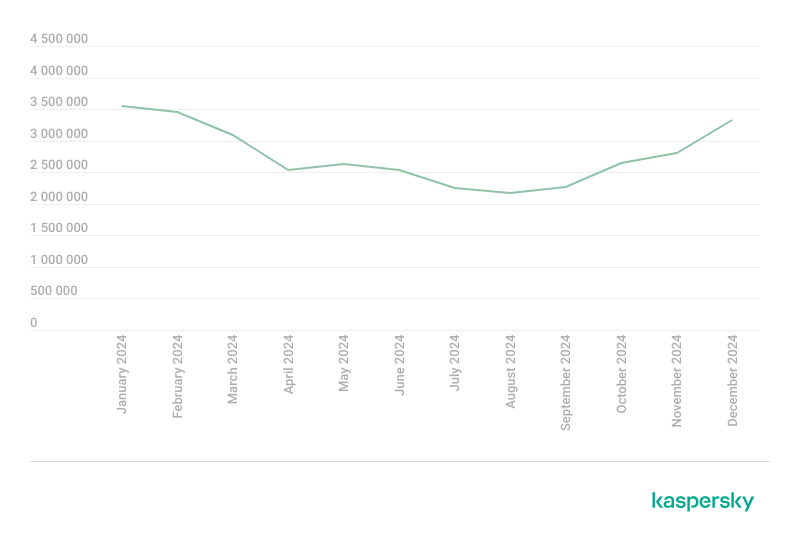
In 2024, cybercriminals launched a monthly average of 2.8 million malware, adware or unwanted software attacks targeting mobile devices. In total, Kaspersky products blocked 33,265,112 attacks in 2024.
Attacks on Kaspersky mobile users in 2024 (download)
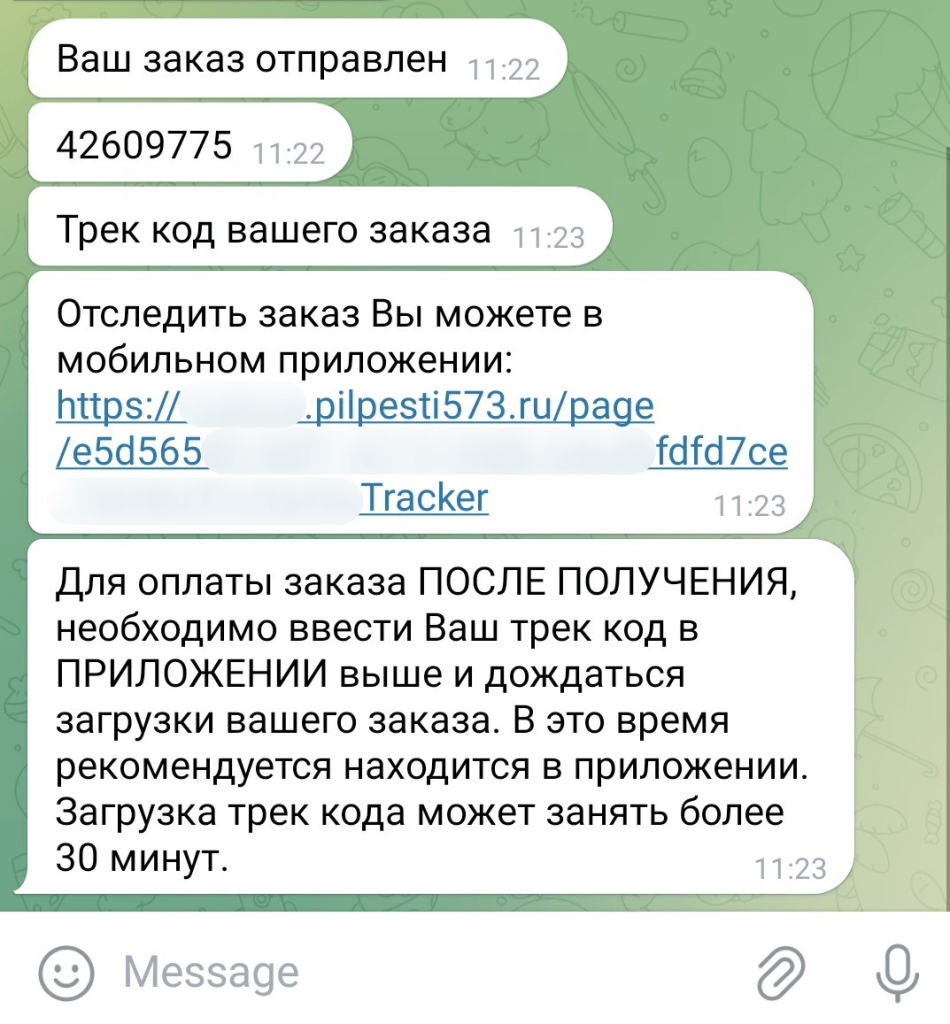
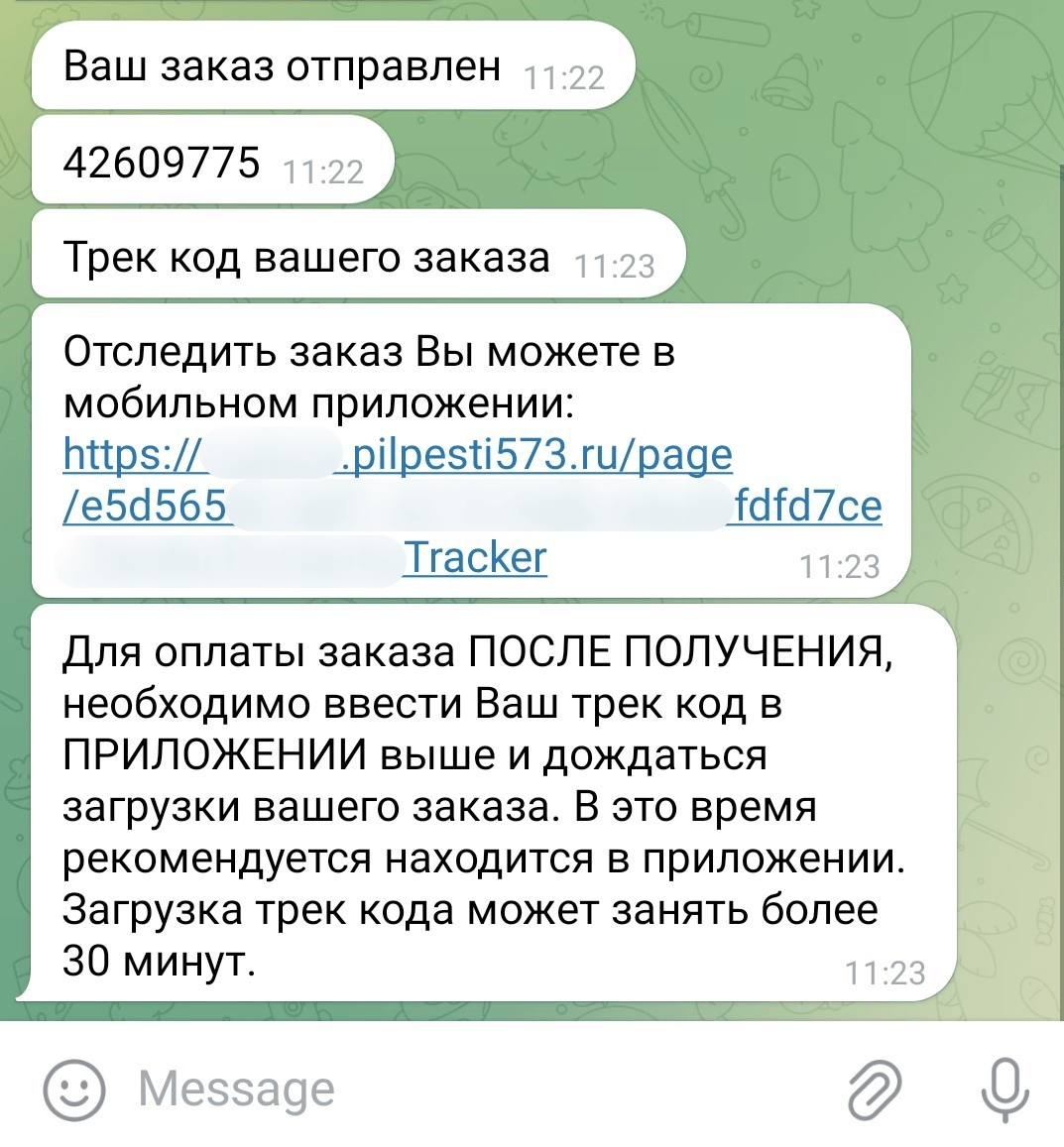
At the end of 2024, we discovered a new distribution scheme for the Mamont banking Trojan, targeting users of Android devices in Russia. The attackers lured users with a variety of discounted products. The victim had to send a message to place an order. Some time later, the user received a phishing link to download malware disguised as a shipment tracking app.
The phishing link as seen in the chat with the fraudsters
See translation
Your order has shipped.
42609775
Your order tracking code.
You can track your order in the mobile app:
https://.pilpesti573.ru/page/e5d565fdfd7ce
Tracker
To pay for your order AFTER YOU RECEIVE IT, enter your tracking code IN THE APP above and wait for your order details to load. We recommend keeping the app open while you are doing so. Loading the track code may take more than 30 minutes.
In August 2024, researchers at ESET described a new NFC banking scam discovered in the Czech Republic. The scammers employed phishing websites to spread malicious mods of the legitimate app NFCGate. These used a variety of pretexts to persuade the victim to place a bank card next to the back of their phone for an NFC connection. The card details were leaked to the fraudsters who then made small contactless payments or withdrew money at ATMs.
A similar scheme was later spotted in Russia, where malware masqueraded as banking and e-government apps. The SpyNote RAT was occasionally used as the malware dropper and NFC activator.
A screenshot of the fake mobile app
See translation
Hold your card against the NFC contactless payment module for verification.
Ready to scan
Also in 2024, we detected many new preinstalled malicious apps that we assigned the generalized verdict of Trojan.AndroidOS.Adinstall. A further discovery, made in July, was the LinkDoor backdoor, also known as Vo1d, installed on Android-powered TV set-top boxes. It was located inside an infected system application com.google.android.services. The malware was capable of running arbitrary executables and downloading and installing any APKs.
On top of the above, we discovered several apps on Google Play, each containing a malicious SDK implant named “SparkCat”, which began to spread at least as early as March 2024. Infected apps were deleted by the store in February 2025: nevertheless, our telemetry data shows that other apps containing SparkCat are distributed through unofficial sources.
This SDK received a C2 server command with a list of keywords or dictionaries to search the gallery on the device for images to exfiltrate. Our data suggests that the Trojan was aimed at stealing recovery phrases for cryptocurrency wallets of Android users primarily in the UAE, Europe and Asia.
It is worth noting that the same implant for iOS was delivered via the App Store, which makes it the first known OCR malware to sneak into Apple’s official marketplace. Apple removed the infected apps in February 2025.
Mobile threat statistics
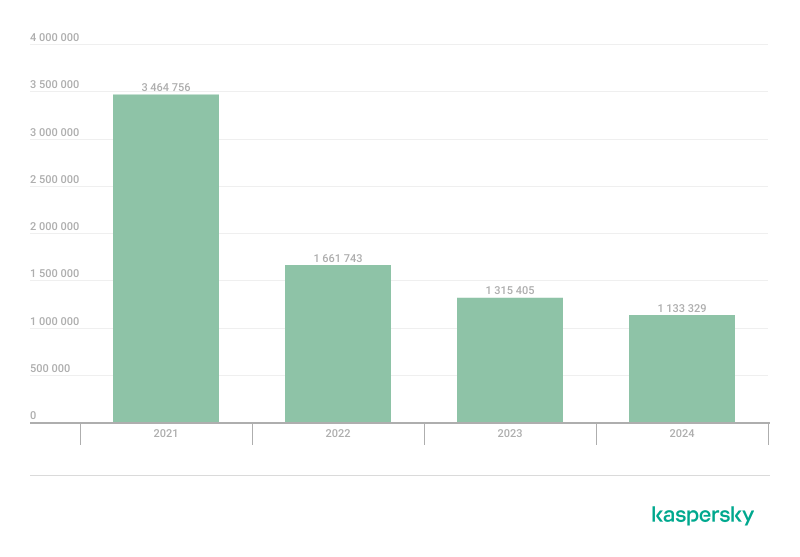
We discovered 1,133,329 malicious and potentially unwanted installation packages in 2024. This was below the 2023 figure, but the difference was smaller than the year before. The trend in the number of new unique malware installation packages appears to be plateauing.
Detected Android-specific malware and unwanted software installation packages in 2021–2024 (download)
Detected packages by type
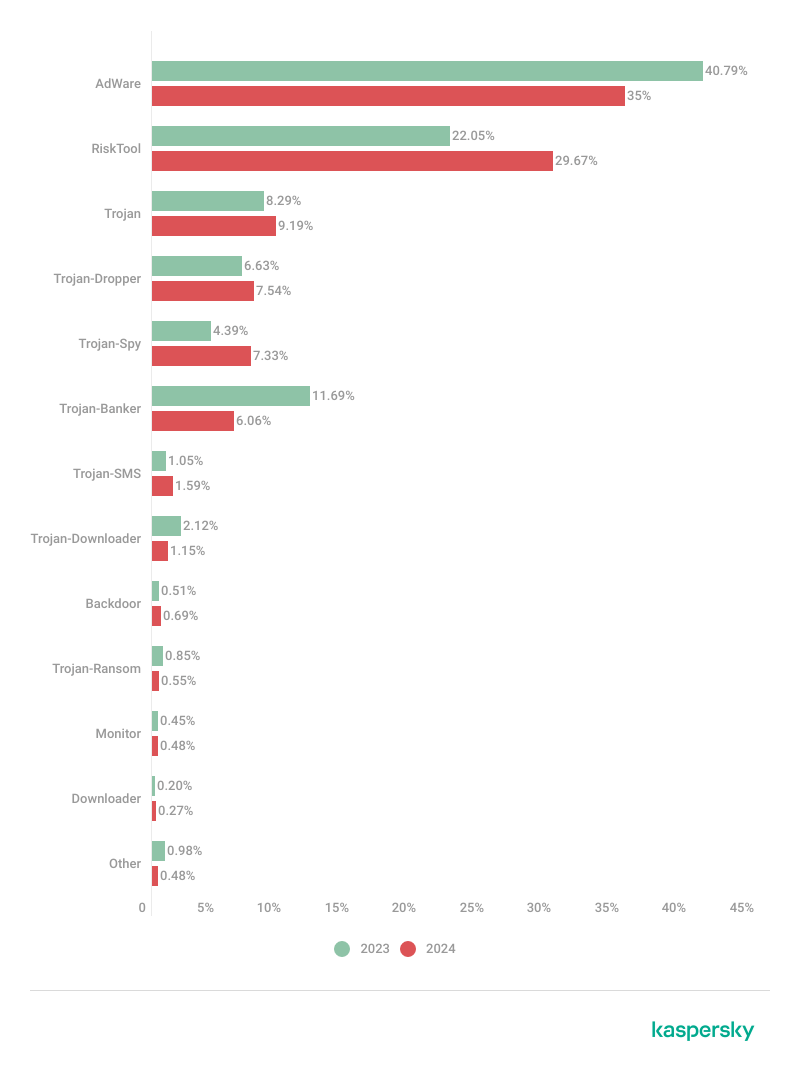
Detected mobile apps by type in 2023 and 2024 (download)
Adware and RiskTool apps continued to dominate the rankings of detected threats by type. The BrowserAd (22.8%), HiddenAd (20.3%) and Adlo (16%) families accounted for the largest number of new installation packages in the former category. RiskTool’s share grew largely due to an increase in the number of Fakapp pornographic apps.
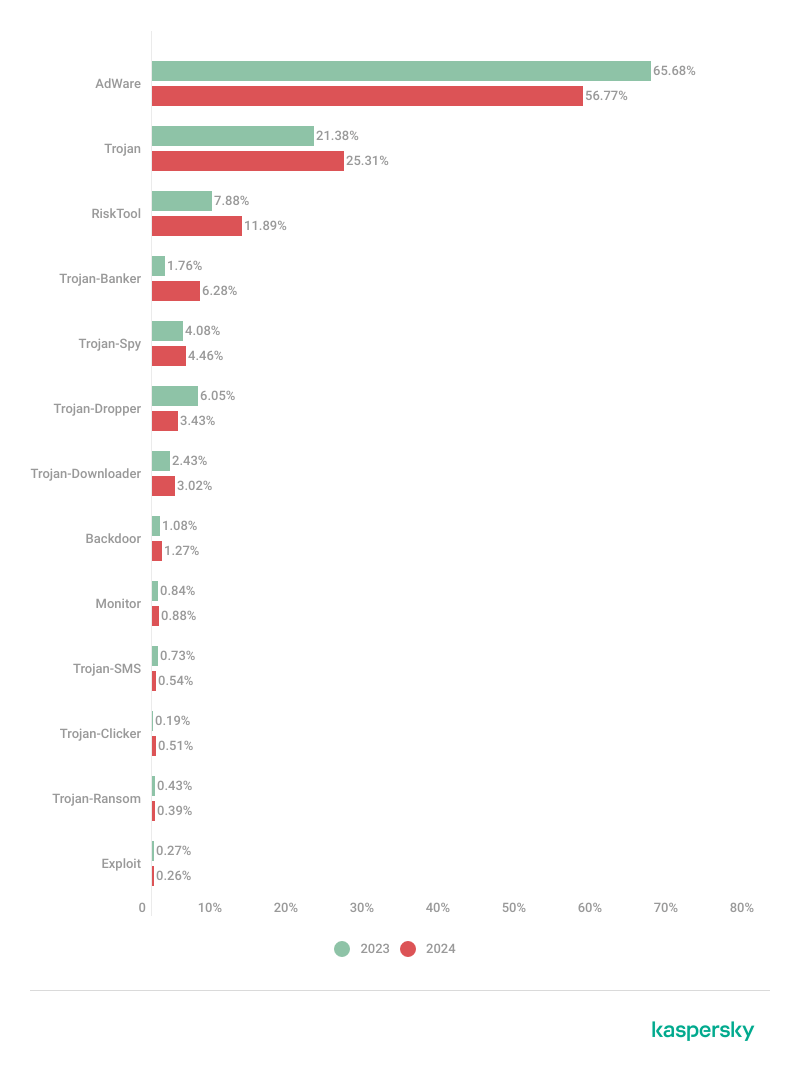
Share* of users attacked by the given type of malware or unwanted software out of all targeted Kaspersky mobile users in 2023–2024 (download)
*The total may exceed 100% if the same users experienced multiple attack types.
Banking Trojans gained three positions as compared with 2023 to occupy fourth place, following the usual leaders: adware, Trojans, and RiskTool.
TOP 20 most frequently detected types of mobile malware
Note that the malware rankings below exclude riskware and potentially unwanted apps, such as adware and RiskTool.Verdict%* 2023%* 2024Difference in p.p.Change in rankingTrojan.AndroidOS.Fakemoney.v11.7616.64+4.88+2DangerousObject.Multi.Generic.14.8211.13–3.70–1Trojan.AndroidOS.Triada.ga0.006.64+6.64Trojan-Banker.AndroidOS.Mamont.bc0.005.36+5.36Trojan.AndroidOS.Boogr.gsh6.814.71–2.10–3Trojan.AndroidOS.Triada.fd1.164.45+3.29+19DangerousObject.AndroidOS.GenericML2.394.35+1.96+3Trojan-Downloader.AndroidOS.Dwphon.a0.773.59+2.82+26Trojan-Spy.AndroidOS.SpyNote.bz0.433.40+2.97+48Trojan-Spy.AndroidOS.SpyNote.bv0.372.69+2.32+57Trojan.AndroidOS.Fakeapp.hk0.002.51+2.51Trojan.AndroidOS.Triada.gs0.002.50+2.50Trojan.AndroidOS.Triada.gn0.002.02+2.02Trojan-Downloader.AndroidOS.Agent.mm1.461.91+0.45+6Trojan.AndroidOS.Triada.gm0.001.84+1.84Trojan.AndroidOS.Generic.3.631.83–1.80–8Trojan.AndroidOS.Fakemoney.bw0.001.82+1.82Trojan-Banker.AndroidOS.Agent.rj0.001.63+1.63Trojan.AndroidOS.Fakemoney.bj0.001.61+1.61Trojan-Spy.AndroidOS.SpyNote.cc0.061.54+1.47
* Share of unique users who encountered this malware as a percentage of all attacked Kaspersky mobile users
Fakemoney, a family of investment and payout scam apps, showed the highest level of activity in 2024. Third-party WhatsApp mods with the Triada.ga embedded Trojan were third, following the generalized cloud-specific verdict of DangerousObject.Multi.Generic. Many other messaging app mods in the same family, namely Triada.fd, Triada.gs, Triada.gn and Triada.gm, hit the TOP 20 too.
Mamont banking Trojans, ranking fourth by number of attacked users, gained high popularity with cybercriminals. These malicious apps come in a multitude of variants. They typically target users’ funds via SMS or USSD requests. One of them spreads under the guise of a parcel tracking app for fake online stores.
Various malware files detected by machine learning technology ranked fifth (Trojan.AndroidOS.Boogr.gsh) and seventh (DangerousObject.AndroidOS.GenericML). They were followed by the Dwphon Trojan that came preinstalled on certain devices. The SpyNote RAT Trojans, which remained active throughout the year, occupied ninth, tenth and twentieth places.
Region-specific malware
This section describes malware types that mostly affected specific countries.VerdictCountry*%**Trojan-Banker.AndroidOS.Agent.nwTurkey99.58Trojan.AndroidOS.Piom.axdhTurkey99.58Trojan-Banker.AndroidOS.BrowBot.qTurkey99.18Trojan-Banker.AndroidOS.BrowBot.wTurkey99.15Trojan.AndroidOS.Piom.baylTurkey98.72Trojan-Banker.AndroidOS.BrowBot.aTurkey98.67Trojan-Spy.AndroidOS.SmsThief.wpIndia98.63Trojan-Banker.AndroidOS.Rewardsteal.faIndia98.33Trojan.AndroidOS.Piom.bbfvTurkey98.31Trojan-Banker.AndroidOS.BrowBot.nTurkey98.14HackTool.AndroidOS.FakePay.cBrazil97.99Backdoor.AndroidOS.Tambir.dTurkey97.87Trojan.AndroidOS.Piom.bcqpTurkey97.79HackTool.AndroidOS.FakePay.iBrazil97.65Backdoor.AndroidOS.Tambir.aTurkey97.62Trojan-Banker.AndroidOS.Coper.bTurkey97.45HackTool.AndroidOS.FakePay.hBrazil97.39Trojan-Spy.AndroidOS.SmsThief.yaIndia97.09Trojan-Spy.AndroidOS.SmsThief.wmIndia97.09Trojan-Banker.AndroidOS.Rewardsteal.hiIndia96.68
* Country where the malware was most active
* Share of unique users who encountered the malware in the indicated country as a percentage of all Kaspersky mobile security users attacked by the malware
Turkey and India accounted for the majority of region-specific threats in 2024. A variety of banking Trojans continued to be active in Turkey. Piom Trojans were associated with GodFather and BrowBot banker campaigns.
Users in India were attacked by Rewardsteal bankers and a variety of SmsThief SMS spies. Our quarterly reports have covered FakePay utilities widespread in Brazil and designed to defraud sellers by imitating payment transactions.
Mobile banking Trojans
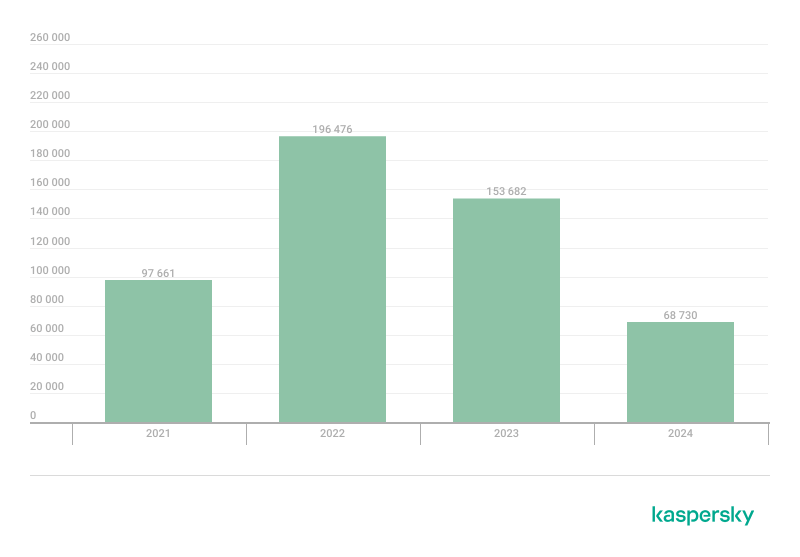
The number of new banking Trojan installation packages dropped again to 68,730 as compared to the previous year.
The number of mobile banking Trojan installation packages detected by Kaspersky in 2021–2024 (download)
The total number of banker attacks increased dramatically over 2023’s level despite the drop in the number of unique installation packages. The trend has persisted for years. This may suggest that scammers began to scale down their efforts to generate unique applications, focusing instead on distributing the same files to a maximum number of victims.
TOP 10 mobile bankersVerdict%* 2023%* 2024Difference in p.p.Change in rankingTrojan-Banker.AndroidOS.Mamont.bc0.0036.70+36.70Trojan-Banker.AndroidOS.Agent.rj0.0011.14+11.14Trojan-Banker.AndroidOS.Mamont.da0.004.36+4.36Trojan-Banker.AndroidOS.Coper.a0.513.58+3.07+30Trojan-Banker.AndroidOS.UdangaSteal.b0.003.17+3.17Trojan-Banker.AndroidOS.Agent.eq21.793.10–18.69–4Trojan-Banker.AndroidOS.Mamont.cb0.003.05+3.05Trojan-Banker.AndroidOS.Bian.h23.133.02–20.11–7Trojan-Banker.AndroidOS.Faketoken.z0.682.96+2.29+18Trojan-Banker.AndroidOS.Coper.c0.002.84+2.84
* Share of unique users who encountered this malware as a percentage of all users of Kaspersky mobile security solutions who encountered banking threats
Conclusion
The number of unique malware and unwanted software installation packages continued to decline year to year in 2024. However, the rate of that decline slowed down. The upward trend in mobile banking Trojan activity persisted despite the years-long decrease in unique installation packages.
Cybercriminals kept trying to sneak malware into official app stores like Google Play, but we also discovered a fair number of diverse preinstalled malicious apps in 2024. Speaking of interesting techniques first spotted last year, the use of NFC for stealing bank card data stands out.
securelist.com/mobile-threat-r…




Un Patch Tuesday leggero quello di febbraio 2025, ma con quattro zero-day corrette
Gli aggiornamenti Microsoft per il mese di febbraio 2025 correggono solo 63 vulnerabilità, ma tra queste ci sono anche quattro zero-day di cui due già attivamente sfruttate in rete. Ecco tutti i dettagli e i consigli per mettere in
Grave vulnerabilità in OpenSSL: rischio di attacchi Man-in-the-Middle
Scenari di sfruttamento con successo di questa vulnerabilità rendono possibile per l'attaccante fare da intermediario tra le azioni del cliente verso il server. Importante aggiornare tempestivamente
L'articolo Grave vulnerabilità in OpenSSL: rischio di attacchi
Laser Cut Acrylic Provides Movie-Style Authentication
Here at Hackaday, we pride ourselves on bringing you the latest and greatest projects for your viewing pleasure. But sometimes we come across a creation so interesting that we find ourselves compelled to write about it, even if it’s already been hanging around the Internet for years. This may or may not be due to the fact that we just re-watched Crimson Tide, and found ourselves on a self-imposed dive into a very particular rabbit hole…
If you’ve seen Crimson Tide, or the first few minutes of WarGames, you might already know what this post is about. Both films prominently make use of a one-time authentication device which the user snaps in half to reveal a card that has some secret code printed on it — and as it turns out, there are at least two different projects that aim to replicate the props used in the movies.
The props were inspired by the real-world “Sealed Authenticators” used by the United States to verify commands regarding the launch of nuclear weapons. As shown in the films, once a launch order, known as an Emergency Action Message, is received, its validity could be confirmed by breaking open one of the Authenticators and comparing the code sequence printed on it to what was sent along with the message. Supposedly the real ones are more like foil envelopes that would be torn open, but presumably that wasn’t cool enough for Hollywood.
So how do you make your own film-quality Authenticator? The two projects take slightly different approaches, but the basic idea is to create a three layer acrylic stack. The top and bottom pieces are identical, and scored in the middle so they’ll break along a clean line. The center piece is cut in half and largely hollowed out to create the compartment for your printed message. It’s perhaps best described as two “C” shapes that have slight gap where they meet, which provides some room for the top and bottom layers to flex. With the acrylic pieces aligned and the message inside, everything is solvent welded together.
Of course, the question now is what to do with them. We can think of all sorts of games and challenges that could make use of this kind of thing, but if you’re looking for something a little more practical, these would be an awesome way to store your two-factor authentication recovery codes. With the proper software, you could even use these for secure file storage via QR code.
hackaday.com/2025/02/12/laser-…
 ?w=800
?w=800
 ?w=400
?w=400

NIS2 e clausola di salvaguardia, chi può derogare alla normativa e chi no: che c’è da sapere
In Gazzetta Ufficiale del 10.02.2025 è uscito l’atteso DPCM sulla clausola di salvaguardia per la NIS2, regolamentandone i criteri di applicazione. Vediamo cosa devono fare le organizzazioni interessate da questi parametri di
Come Zuckerberg ha seguito le orme di X
Facebook ha sempre fatto il minimo sul fronte trasparenza. Ma nell’era Trump-Musk ha scelto lo scontro con l’UE.
L'articolo Come Zuckerberg ha seguito le orme di X proviene da Guerre di Rete.
L'articolo proviene da #GuerreDiRete di nostr:nprofile1qy2hwumn8ghj7un9d3shjtnddaehgu3wwp6kyqpq60nwkhpxvsxyh4vh75qeg0ar2xzcj4ywys4y4uzm2e375h046aus9nfw8x
guerredirete.it/come-zuckerber…
A Twin-Lens Reflex Camera That’s Not Quite What It Seems
The Camp Snap is a simple fixed-focus digital camera with only an optical viewfinder and a shot counter, which has become a surprise hit among photography enthusiasts for its similarity to a disposable film camera. [Snappiness] has one, and also having a liking for waist-level viewfinders as found on twin-lens reflex cameras, decided to make a new Camp Snap with a waist-level viewfinder. It’s a digital twin-lens reflex camera, of sorts.
Inside the Camp Snap is the little webcam module we’ve come to expect from these cameras, coupled with the usual microcontroller PCB that does the work of saving to SD card. It’s not an ESP32, but if you’ve ever played with an ESP32-CAM board you’re on a similar track. He creates a 3D-printed TLR-style case designed to take the PCB and mount the camera module centrally, with ribbon cable extensions taking care of placement for the other controls. The viewfinder meanwhile uses a lens, a mirror, and a Fresnel lens, and if you think this might look a little familiar it’s because he’s based it upon his previous clip-on viewfinder project.
The result, with an added “Snappiflex” logo and filter ring, is a rather nice-looking camera, and while it will preserve the dubious quality of the Camp Snap, it will certainly make the process of using the camera a lot more fun. We think these cheap cameras, and particular their even less expensive AliExpress cousins, have plenty of hacking potential as yet untapped, and we’re keen to see more work with them. The full video is below the break.
youtube.com/embed/6lx6p_pr80E?…
hackaday.com/2025/02/09/a-twin…
 ?w=800
?w=800
Your Chance to Get A Head (A Gnu Head, Specifically)
The Free Software Foundation is holding an auction to celebrate its 40th anniversary. You can bid on the original sketch of the GNU head by [Etienne Suvasa] and [Richard Stallman’s] Internet Hall of Fame medal.
There are some other awards, including the FSF’s 1999 Norbert Wiener Award. There’s even a katana that symbolizes the fight for computer user freedom.
The FSF has done a lot of important work to shape the computing world as we know it. We hope this sale isn’t a sign that they are running out of money. Maybe they are just funding their birthday party in Boston.
If you use Linux (even if it is disguised as Android, a Raspberry Pi OS, or hiding on a web server you use), you can thank the FSF. While we commonly call them “Linux systems,” Linux is just the kernel. Most of the other things you use are based on either GNU-sponsored code or builds on that GNU-sponsored code. If you want to know more about the history of the organization, you can catch [ForrestKnight’s] video below.
Without the GNU tools and the Linux kernel, you have to wonder what our computers would look like. While [Richard Stallman] is a sometimes controversial figure, you can’t argue that the FSF has had a positive impact on our computers. Maybe we’d all be on BSD. It is worth noting that the FSF even certifies hardware.
youtube.com/embed/sQDvkd2wtxU?…
hackaday.com/2025/02/09/your-c…
 ?w=800
?w=800
Guerre di Rete - Paragon puntava all’America. E si è impantanata in Italia
Approfondimento sul caso dello spyware che scuote la politica italiana.
#GuerreDiRete è la newsletter curata da nostr:nprofile1qy2hwumn8ghj7un9d3shjtnddaehgu3wwp6kyqpq60nwkhpxvsxyh4vh75qeg0ar2xzcj4ywys4y4uzm2e375h046aus9nfw8x
guerredirete.substack.com/p/gu…
Moving Power Grids In A Weekend, The Baltic States Make The Switch
A significant event in the world of high-power electrical engineering is under way this weekend, as the three Baltic states, Lithuania, Latvia, and Estonia, disconnect their common power grid from the Russian system, and hook it up to the European one. It’s a move replete with geopolitical significance, but it’s fascinating from our point of view as it gives a rare insight into high voltage grid technology.
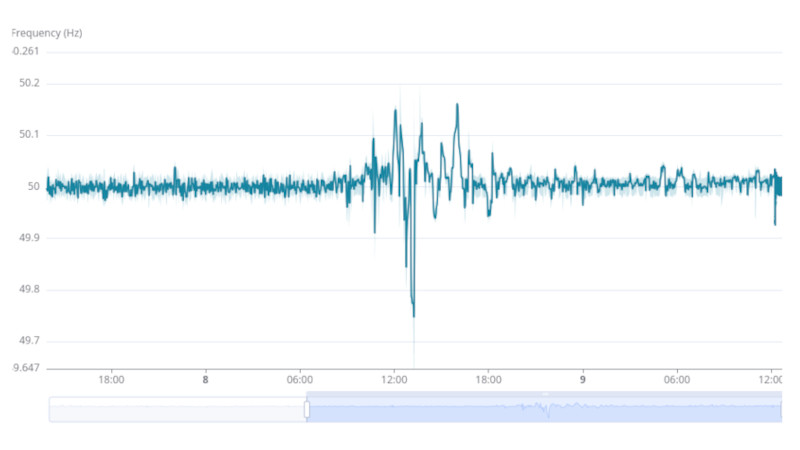
There are a few news videos in the air showing contactors breaking the circuit, and even a cable-cutting moment, but in practice this is not as simple a procedure as unplugging an appliance from a wall socket. The huge level of planning that has gone into this move is evident in the countrywide precautions in case of power loss, and the heightened security surrounding the work. As we understand it at the moment the three countries exist as a temporary small grid of their own, also isolating the Russian exclave of Kaliningrad which now forms its own grid. The process of aligning the phase between Baltic and European grids has been under way overnight, and an online monitor shows significant frequency adjustments during that time. At some point on Sunday a new connection will be made to the European grid via Poland, and the process will be completed. We imagine that there will be a very relieved group of electrical engineers who will have completed their own version of a Moon landing when that has happened.
If you happen to live in either region, there’s still some time to watch the process in action, by monitoring the supply frequency for yourself. It’s not the first time that geopolitics have affected the European grid, as the continent lost six minutes a few years ago, and should you Americans think you are safe from such problems, think again.
hackaday.com/2025/02/09/moving…
 ?w=800
?w=800
Paragon: come funziona lo spyware Graphite, scandalo di Stato
Lo spyware Graphite sviluppato dall'israeliana Paragon è stato usato per sorvegliare un centinaio tra giornalisti e attivisti, tra questi anche diversi italiani. Tuttavia, anche se del caso specifico si sa ancora poco, il pericolo è attuale e reale, rendendo etica una questione che è soprattutto
This Week in Security: Medical Backdoors, Strings, and Changes at Let’s Encrypt
There are some interesting questions afoot, with the news that the Contec CMS8000 medical monitoring system has a backdoor. And this isn’t the normal debug port accidentally left in the firmware. The CISA PDF has all the details, and it’s weird. The device firmware attempts to mount an NFS share from an IP address owned by an undisclosed university. If that mount command succeeds, binary files would be copied to the local filesystem and executed.
Additionally, the firmware sends patient and sensor data to this same hard-coded IP address. This backdoor also includes a system call to enable the eth0 network before attempting to access the hardcoded IP address, meaning that simply disabling the Ethernet connection in the device options is not sufficient to prevent the backdoor from triggering. This is a stark reminder that in the firmware world, workarounds and mitigations are often inadequate. For instance, you could set the gateway address to a bogus value, but a slightly more sophisticated firmware could trivially enable a bridge or alias approach, completely bypassing those settings. There is no fix at this time, and the guidance is pretty straightforward — unplug the affected devices.Reverse Engineering Using… Strings
The Include Security team found a particularly terrifying “smart” device to tear apart: the GoveeLife Smart Space Heater Lite. “Smart Space Heater” should probably be terrifying on its own. It doesn’t get much better from there, when the team found checks for firmware updates happening over unencrypted HTTP connections. Or when the UART password was reverse engineered from the readily available update. It’s not a standard Unix password, just a string comparison with a hardcoded value, and as such readily visible in the strings output.
Now on to the firmware update itself. It turns out that, yes, the device will happily take a firmware update over that unencrypted HTTP connection. The first attempt at running modified firmware failed, with complaints about checksum failures. Turns out it’s just a simple checksum appended to the firmware image. The device has absolutely no protection against running custom firmware. So this leads to the natural question, what could an attacker actually do with access to a device like this?
The proof of concept attack was to toggle the heat control relay for every log message. In a system like this, one would hope there would be hardware failsafes that turn off the heating element in an overheat incident. Considering that this unit has been formally recalled for over 100 reports of overheating, and at least seven fires caused by the device, that hope seems to be in vain.
youtube.com/embed/CuahxZOOqbs?…
AMD Releases
We wrote about the mysterious AMD vulnerability a couple weeks ago, and the time has finally come for the full release. It’s officially CVE-2024-56161, “Improper signature verification in AMD CPU ROM microcode patch loader”. The primary danger seems to be malicious microcode that could be used to defeat AMD’s Secure Encrypted Virtualization-Secure Nested Paging (SEV-SNP) technology. In essence, an attacker with root access on a hypervisor could defeat this VM encryption guarantee and compromise the VMs on that system.
This issue was found by the Google Security Team, and there is a PoC published that demonstrates the attack with benign effects.
The Mirai Two-fer
The Mirai botnet seems to have picked up a couple new tricks, with separate strains now attacking Zyxel CPE devices and Mitel SIP phones. Both attacks are actively being exploited, and the Zyxel CPE flaw seems to be limited to an older, out-of-support family of devices. So if you’re running one of the approximately 1,500 “legacy DSL CPE” devices, it’s time to pull the plug. Mitel has published an advisory as well, and is offering firmware updates to address the vulnerability.
Let’s Encrypt Changes
A service many of us depend on is making some changes. Let’s Encrypt is no longer going to email you when your certificate is about to expire. The top reason is simple. It’s getting to be a lot of emails to send, and sending emails can get expensive when you measure them in the millions.
Relatedly, Let’s Encrypt is also about to roll out new six-day certificates. Sending out email reminders for such short lifetimes just doesn’t make much sense. Finally from Let’s Encrypt is a very useful new feature, the IP Address certificate. If you’ve ever found yourself wishing you didn’t have to mess with DNS just to get an HTTPS certificate, Let’s Encrypt is about to have you covered.
Bits and Bytes
There’s a Linux vulnerability in the USB Video Class driver, and CISA has issued an active exploit warning for it. And it’s interesting, because it’s been around for a very long time, and it was disclosed in a Google Android Security Bulletin. It’s been suggested that this was a known vulnerability, and was used in forensic tools for Android, in the vein of Cellebrite.
Pretty much no matter what program you’re using, it’s important to never load untrusted files. The latest application to prove this truism is GarageBand. The details are scarce, but know that versions before 10.4.12 can run arbitrary code when loading malicious images.
Ever wonder how many apps Google blocks and pulls from the app store? Apparently better than two million in 2024. The way Google stays mostly on top of that pile of malware is the use of automated tools, which now includes AI tools. Which, yes, is a bit terrifying, and has caused problems in other Google services. YouTube in particular comes to mind, where channels get content strikes for seemingly no reason, and have trouble finding real human beings at Google to take notice and fix what the automated system has mucked up.
And finally, echoing what Kee had to say on the subject, cryptocurrency fraud really is just fraud. And [Andean Medjedovic] of Canada found that out the hard way, after his $65 million theft landed him in jail on charges of wire fraud, computer hacking, and attempted extortion.
hackaday.com/2025/02/07/this-w…
 ?w=800
?w=800
Caso Graphite e spyware di Stato: una questione etica il loro uso indiscriminato
Lo spyware Graphite dell'israeliana Paragon è stato usato per sorvegliare un centinaio tra giornalisti e attivisti, tra questi anche diversi italiani. Tuttavia, anche se del caso specifico si sa ancora poco, il pericolo è attuale e reale, rendendo etica una questione che è
Split-Flap Clock Makes a Nice Side Quest in Larger Project
Sometimes projects spawn related projects that take on a life of their own. That’s OK, especially when the main project is large and complex, In that case, side-quest projects provide a deliverable that can help keep the momentum of the whole project going. The mojo must flow, after all.
That seems to be what’s going on with this beautiful split-flap clock build by [Erich Styger]. It’s part of a much larger effort which will eventually see 64 separate split-flap units chained together. This project has been going on for a while; we first featured it back in 2022 when it was more of a prototype. Each unit is scratch-built, using laser-cut fiberboard for parts like the spool and frame, thin PVC stock for the flip cards, and CNC-cut vinyl for the letters and numbers. Each unit is powered by its own stepper motor.
To turn four of these displays into a clock, [Erich] milled up a very nice enclosure from beech. From the outside it’s very clean and simple, almost like something from Ikea, but the inside face of the enclosure is quite complex. [Erich] had to mill a lot of nooks and crannies into the wood to provide mounting space and clearance for the split-flap mechanism, plus a thinned-down area at the top of each window to serve as a stop for the flaps. The four displays are controlled by a single controller board, which houses an NXP K22FN512 microcontroller along with four stepper drivers and interfaces for the Hall-effect sensors needed to home each display. There’s also an RS-485 interface that lets the controllers daisy-chain together, which is how the big 64-character display will be controlled.
We’re looking forward to that, but in the meantime, enjoy the soft but pleasant flappy goodness of the clock in the brief video below.
youtube.com/embed/s_7kXFjp-Rs?…
hackaday.com/2025/02/07/split-…
 ?w=800
?w=800
DeepSeek, le conseguenze geopolitiche dell’IA cinese
Oltre alla questione della privacy, DeepSeek appare come un nuovo strumento modellato per diffondere la narrativa del Partito comunista cinese (Pcc) e alterare la percezione globale su questioni sensibili, a vantaggio delle strategie di sorveglianza e di propaganda di Pechino
L'articolo DeepSeek, le
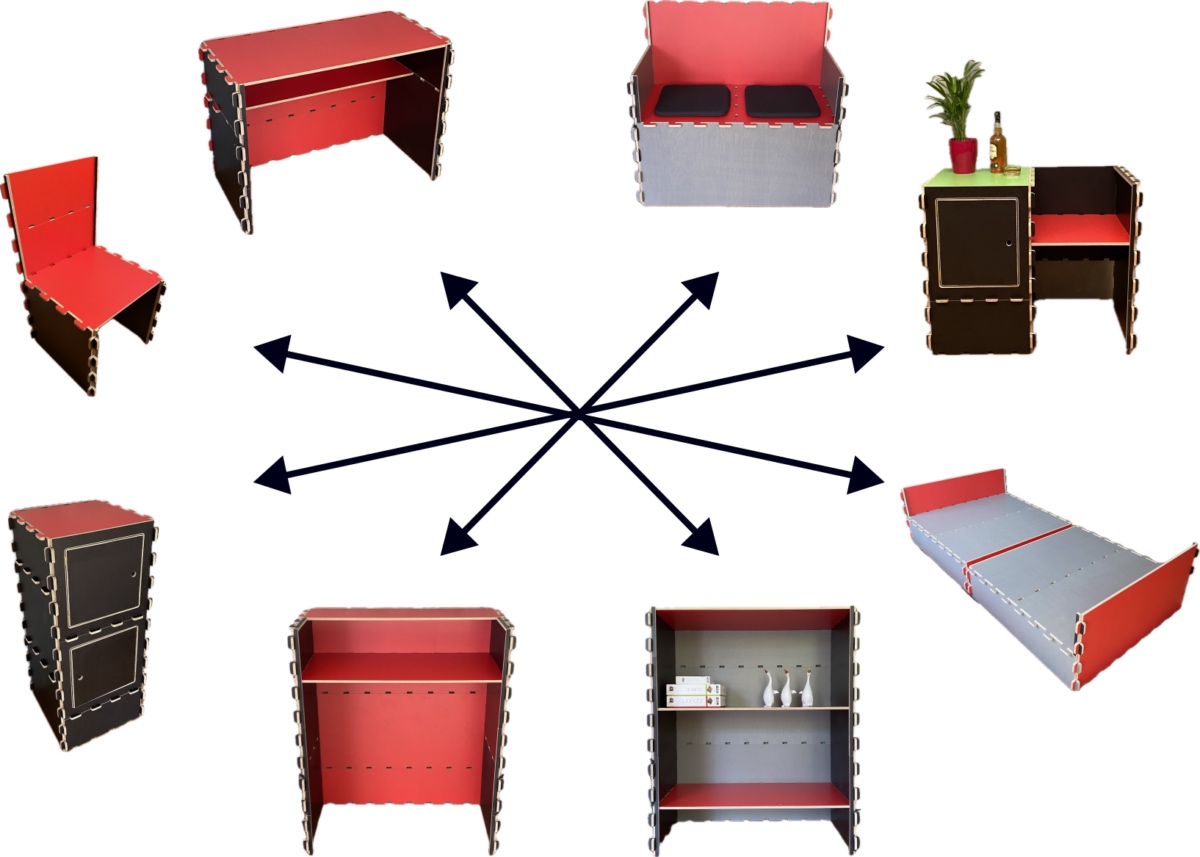
Quix Furniture for Modular Furniture Fun
If you’re someone who moves a lot, or just likes to change your decor, the limitations of conventional furniture can be a bit of a pain. Why not build your furniture modularly, so it can change with you?
QUIX is a modular building system designed for furnishings developed by [Robert Kern]. Giving people the ability to “build any kind of furniture in minutes with no tools,” it seems like a good gateway for people who love building with LEGO but find the pegs a little uncomfortable and expensive for full-sized chairs and couches. Anything that makes making more accessible is an exciting development in our book.
Featuring a repeating series of interlocking hooks, the panels can be produced via a number of techniques like CNC, laser cutter, or even smaller 3D printed models. Dowels and elastic bands serve as locks to prevent the furniture from tilting and since you have such a wide variety of panel materials to choose from, the color combinations can range from classic plywood to something more like a Mondrian.
If you’re looking for more modular inspiration for your house, how about gridbeam or Open Structures? If you’re wanting your furniture more musically-inclined, try Doodlestation instead.
youtube.com/embed/4Mp2zrYkJNk?…
Thanks to [DjBiohazard] for the tip!
hackaday.com/2025/02/07/quix-f…
 ?w=800
?w=800
