ick

This is what i dug up about poisoned transactions:
Transaction poisoning refers to an attack on the Ethereum network where a malicious actor manipulates data within a transaction to cause unintended consequences. This can include altering the recipient address or changing the value of the transaction, effectively stealing funds or causing other disruptions.
Let's consider a vulnerable smart contract that uses an unsafe method for transferring funds:
pragma solidity ^0.6.0;
contract VulnerableContract {
function sendEth(address payable recipient) public {
// Unsafe method: directly sending Ether without validating the recipient's balance or safeTransfer logic
recipient.transfer(msg.value);
}
}
In this example, the 'sendEth' function of the 'VulnerableContract' is susceptible to a transaction poisoning attack. If an attacker were to modify the recipient address and send a poisoned transaction with a large amount, the contract would unknowingly transfer funds to the wrong address, leaving users like you at risk of losing their funds.
Here's an example of how an attacker could exploit the vulnerable 'sendEth' function in our previous example:
pragma solidity ^0.6.0; // Exploit Code
contract ExploitContract {
address public hacker; // Store the hacker's address as a public variable
constructor() public {
hacker = 0xabcdef123; // Set the hacker's address to the contract when it's deployed
}
function sendEth(address payable recipient) public {
// Unsafe method: directly sending Ether without validating the recipient's balance or safeTransfer logic
recipient.transfer(msg.value);
// Poisoned transaction with modified recipient and amount
ExploitContract(hacker).sendEth(0xfakeaddress456);
}
}
In this example, an attacker could deploy their own contract (ExploitContract) and pass it as a parameter when deploying the vulnerable 'VulnerableContract'. By doing so, the hacker can manipulate the 'sendEth' function within the 'VulnerableContract', effectively stealing funds from legitimate users.
am not a solidity guy but this is what I found on quick dig
No vinney. I am dead serious . the market is not what you think it is. Its an entropy pump just like every competitive environment is. Its just too much to explain with thumbs. Plus now you decided to be rude so you can suss it yourself or not whatevs.
Bruh. That's what an unmolested market is. If I believed as you do I couldn't do what I do. The market is not what you think. Levels bro.
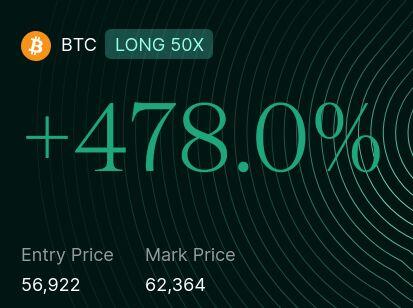
GM
Back at office
Let's do this

Illegals Swarm California Beach Town By Boat
From Infowars
If this isn’t an invasion, what is? Footage out of Newport Beach, California, shows 24 illegal migrants driving a boat up to a marina, exiting, and running through a nearby neighborhood. The incident took place in a beautiful and affluent area as seen in the footage. WATCH: Approximately two dozen migrants were caught on film […]
May 3rd 2024 4:55am EDT
Source Link: https://www.infowars.com/posts/illegals-swarm-california-beach-town-by-boat/
Share, promote & comment with Nostr: https://dissentwatch.com/boost/?boost_post_id=762766
Its not an invasion. You are being harvested. The workers are arriving.
Because I don't need the market to give me pleasure and inefficiencies are what I trade to extract value. Just because I am profiting doesn't mean its fair or right or that I am not being skimmed.
Almost done anyway. If we don't blow ourselves up it will be irellevant. Universe is huge. Nothing is scarce.
Amen bro. nobody coming to save us. we gotta do it.
somehow I think Uncle Brian would love that answer.
I had no answer btw. I took a hard pass. so buddy has no answer for uncle brian to give IDF kid and I have answer for buddy and yeeesh family problems
bro, why you leavin? I mean refresh the npub but dont leave.
I got this note from a jewish friend yesterday. He and family have been helping organize anti zionist rallies.
What say you Nostr?
My nephew from the IDF flew from Jerusalem to Columbus, Ohio on Friday to introduce his fiancée to his family and friends. Ohio state university is between the airport and his home and the streets were blocked by American white kids, his age of 22, waiving green Hamas flags and shouting from the river to the sea.
His base is on the Gaza border and was devastated on October 7.
He says “ uncle Brian, what’s happening ?” I have no answer
humanity lost a step since then bro.


