Tuesday assorted links:
nostr-attacks/README.md at main · ronaldstoner/nostr-attacks · GitHub
Known Nostr Attacks A list of the larger known attacks against the Nostr decentralized network.
🔗 https://github.com/ronaldstoner/nostr-attacks/blob/main/README.md
---
Quirk: Quantum Circuit Simulator
A drag-and-drop quantum circuit simulator.
---
WhatsApp Flaw Allows Bypassing the 'View Once' Media Privacy Feature | RestorePrivacy
Researchers have uncovered a privacy flaw in WhatsApp's \View Once\ feature that effectively allows its bypassing.
🔗 https://restoreprivacy.com/whatsapp-flaw-allows-bypassing-the-view-once-media-privacy-feature/
---
Grocery price inflation: Is corporate greed to blame? : NPR
🔗 https://www.npr.org/2024/09/09/nx-s1-5103935/grocery-prices-inflation-corporate-greedflation
---
veebch/Bip39-Dice: Generate a Bitcoin Wallet Seed Phrase using dice (and a few lines of Python)
🔗 https://github.com/veebch/Bip39-Dice
---
Mercury Layer vulnerabilities disclosure
An examination of validation vulnerabilities in the Mercury Layer client libraries.
🔗 https://conduition.io/mercury-disclosure-f893472ec3128de1.html
particles in our universe behave quantum mechanically. you can measure this explicitly. it tells us that certain "observables" of particles such as position and momentum can't be measured separately from each other, you can think of it as a vector, if you know more of the position you know less of the momentum and vice versa.
if you study the math of this, it forms something called a "Lie algebra", the generators of this algebra for certain types of observables are the pauli matrices:
https://en.wikipedia.org/wiki/Pauli_matrices
You can use these for the basis vectors in quantum computation. Basically you're using the nuts and bolts of reality to execute computations. These are called qubits.
The way you do this is to perform a sequence of unitary gate operations in this basis, which you can think of as transformations of the particles amplitude (complex valued probability-like waves). Once you performed a bunch of operations, you can measure the result (born rule) to get a non-complex value out. This is equavalent to wavefunction collapse in physics. In the double slit experiment its like trying to observe one path of a particle vs the other.
Anyways, if you construct your algorithm so that correct answers constructively interfere with each other, and incorrect answers destructively interfere, you can create a measurement to get answers that classical computers cannot do. This is because the amount of states in quantum amplitudes can be much higher than the number of states in classical computers, or even particles in the universe. So you can get speedups over classical computations in ways that people are still wrapping their noggin around.
Damn, you're way deep on this rabbit hole.
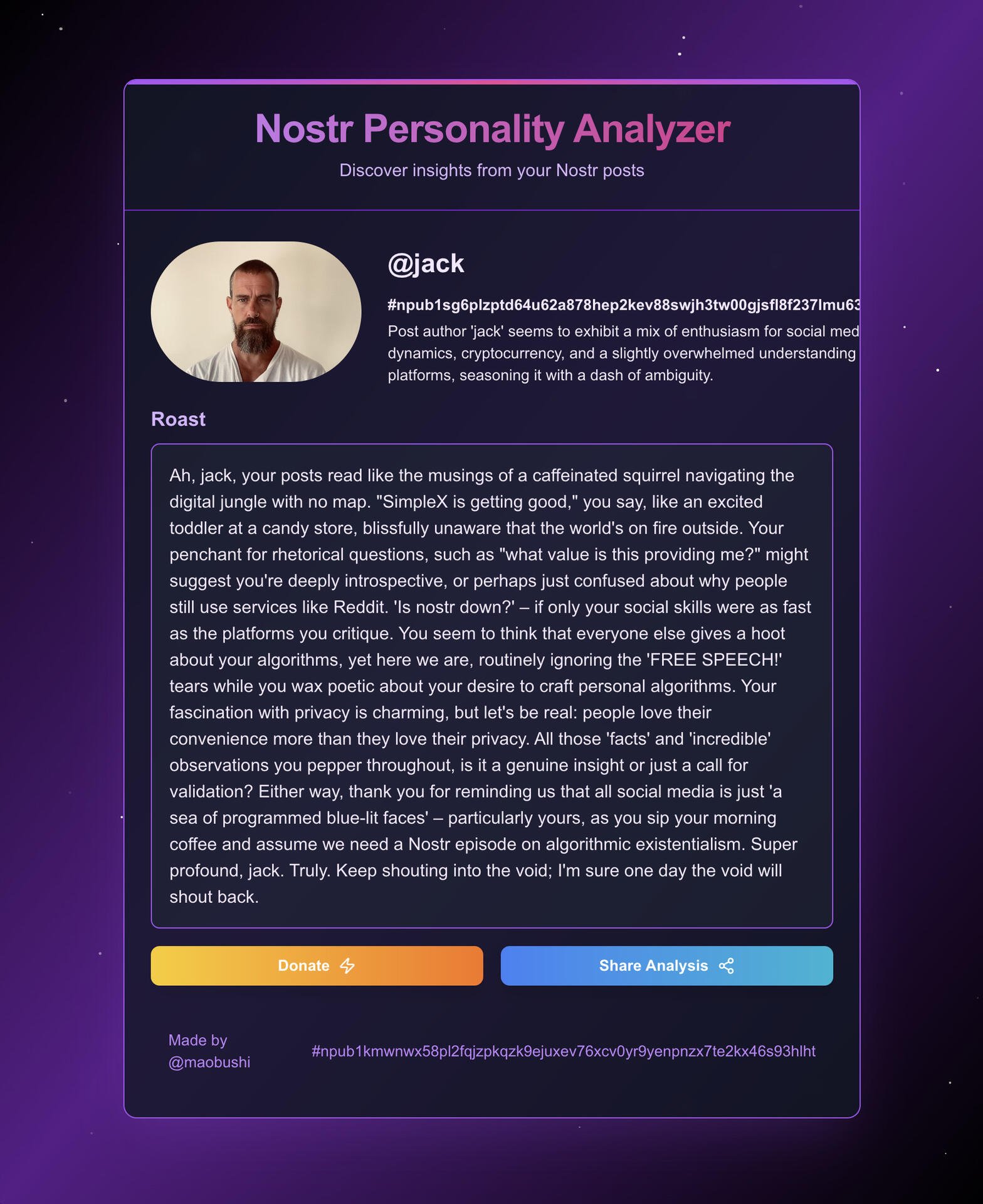
Comparing BkueSky to Nostr is like comparing CompuServe to the Internet in 1994.
nostr:note1qqqxz5u5t0gx5zrmmyrme2xxvcpavfqtaksuetlxvdw4jecw2yeqwl0ymv
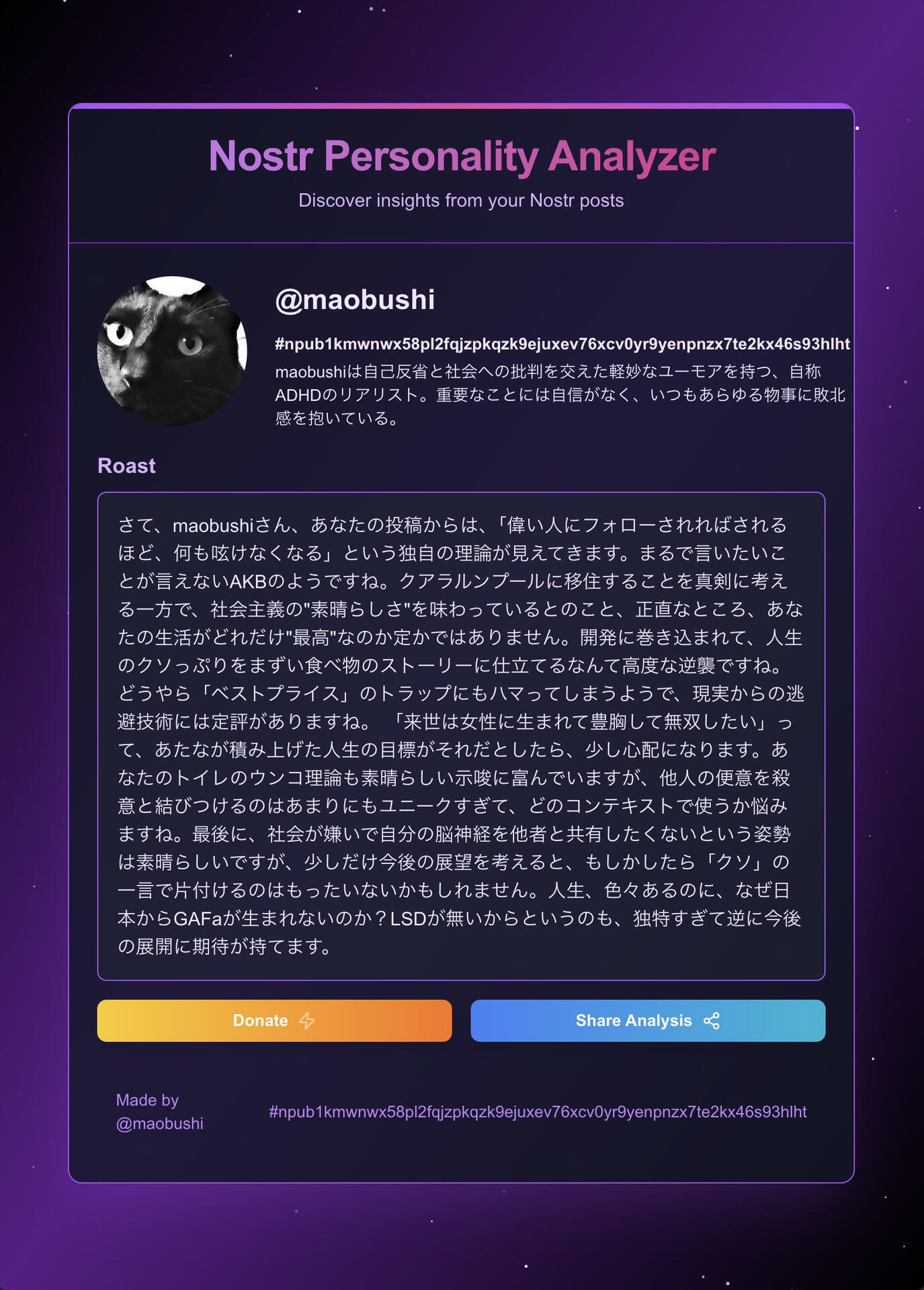
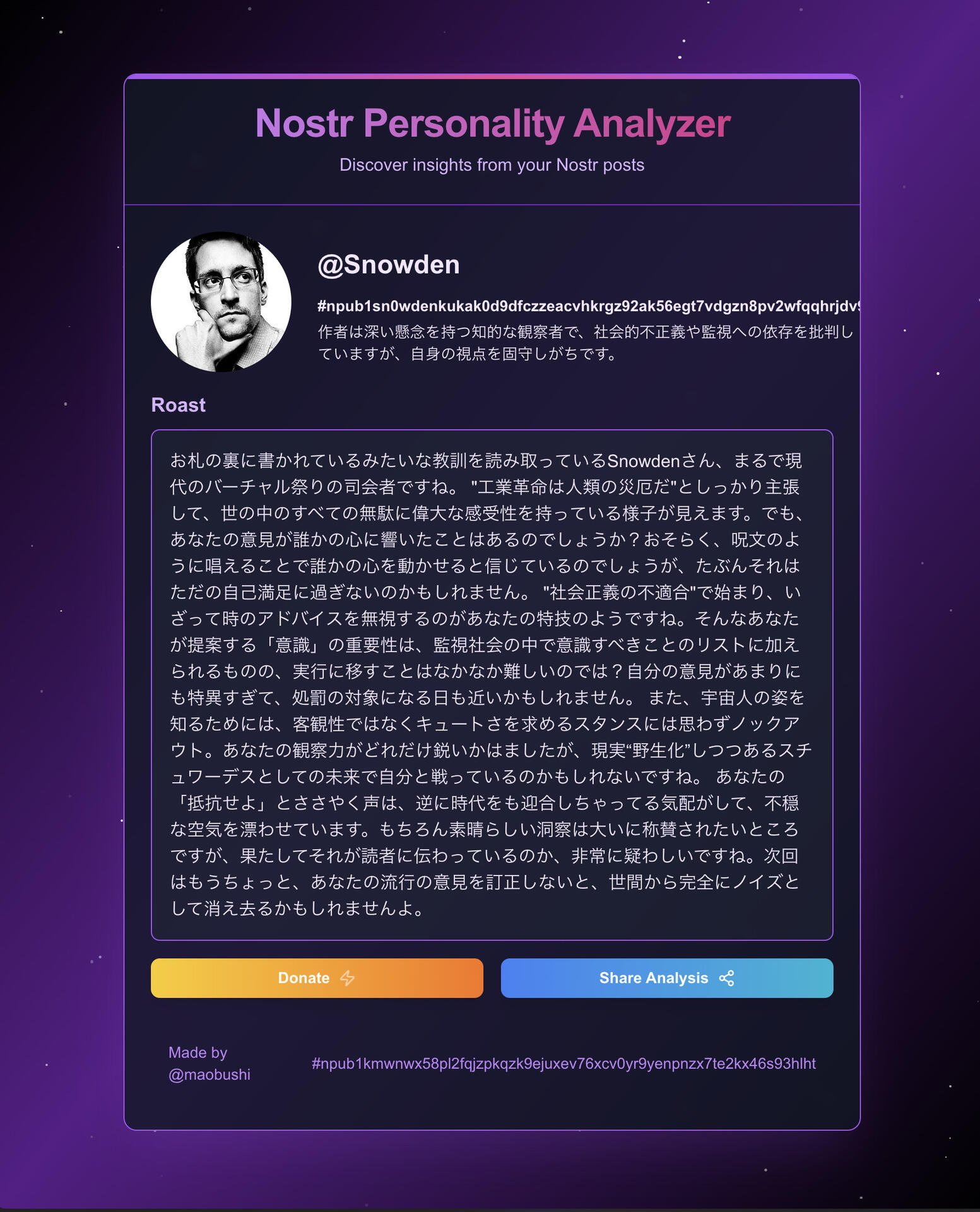
Great job. Loved the roast.

nostr:note1thuctljnkp2f69lfy5dhklzk6mvcwce02tn752tz26fwwjxqtqvsdvaad4
Nit: accept also raw public keys, not only npubs:
62cef883863022a4f1d60d54857c9d729650702c9fe227b0988c0b6e36c4bcce
should work as
npub1vt803quxxq32fuwkp42g2lyaw2t9qupvnl3z0vyc3s9kudkyhn8qt28cxv
Nit: when I added the raw public key, the error in the alert is in japanese.
Nice work, loved the roast.
Monday assorted links:
gRPC: 5 Years Later, Is It Still Worth It? | by Konstantin Ostrovsky | Sep, 2024 | Medium
5 years with gRPC: Is it still my go-to for communication? Dive into my journey and discover if this protocol stands the test of time.
🔗 https://kostyay.com/grpc-5-years-later-is-it-still-worth-it-b181a3b2b73b
---
gRPC: The Ugly Parts
The seedy underbelly of gRPC.
🔗 https://kmcd.dev/posts/grpc-the-ugly-parts/
---
Wealthfolio | Desktop Investment Tracker
Wealthfolio is a simple, desktop-based investment tracker. Your financial data is stored safely on your own computer. No subscriptions, no cloud.
---
Alternative Math | Short Film - YouTube
A well meaning math teacher finds herself trumped by a post-fact America.
🔗 https://www.youtube.com/watch?v=Zh3Yz3PiXZw
---
Real-Time Crime Index | Nationwide Crime Data & Trends
Sunday assorted links:
OAuth from First Principles - Stack Auth
Stack Auth is open-source authentication for the modern web.
🔗 https://stack-auth.com/blog/oauth-from-first-principles
---
Test Ad Block - Toolz
Looking for an easy way to check the efficiency of your ad blocker? Toolz offers a simple and beautiful design test that allows you to quickly and easily test the performance of current ad/content blocker solution. Intuitive interface makes it easy to navigate and use, and the beautiful design ensures that the experience is visually appealing. With just a click, you can see how well the ad blocker is working and make any necessary adjustments.
Friday assorted links:
Cypherpunk Culture: Unravelling the Origins (1/2)
Exploring the origins, key figures, and core principles of the Cypherpunk movement
🔗 https://www.cypherpunktimes.com/cypherpunk-culture-unraveling-the-origins/
---
Understanding Silent Payments – Part I
In this first part of our silent payment series, we explore how the underlying cryptography and mechanisms of how silent payments actually work.
🔗 https://bitbox.swiss/blog/understanding-silent-payments-part-one/
---
Sticky Headers And Full-Height Elements: A Tricky Combination — Smashing Magazine
Sticky positioning is one of those CSS features that’s pretty delicate and can be negated by a lot of things, so here’s another one to add to your mental catalog: Sticky elements don’t play nicely if they have to coordinate with other elements to make up a combined height, like `100vh`. Philip Braunen explores why this happens and presents a solution to fix it.
🔗 https://www.smashingmagazine.com/2024/09/sticky-headers-full-height-elements-tricky-combination/
One can literally make a #Nostr client with a static html + websocket and run it locally!! WTF
Good weekend project, BTW!
nostr:nprofile1qqsx9nhcswrrqg4y78tq64y90jwh99jswqkflc38kzvgczmwxmztenspzemhxue69uhk2er9dchxummnw3ezumrpdejz7qgwwaehxw309ahx7uewd3hkctcpr3mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmq44x7tg , I'm taking on your weekend projects concept and make this...
Cool!
Let me know if you need any help.
Thursday assorted links:
UTXO Research Report: State Of The Bridges - Bitcoin Magazine - Bitcoin News, Articles and Expert Insights
A research report analyzing the different trust models and functioning mechanisms of proposed and existing two-way pegs for Bitcoin layers.
🔗 https://bitcoinmagazine.com/technical/state-of-the-bridges
+1.
Não tenho apps do Zuck instaladas.
Infelizmente tenho de abrir uma excepção para o WhatsApp, demasiados amigos a usá-lo e não há maneira de o usar sem a app instalada.
Wednesday assorted links:
Facebook partner admits smartphone microphones listen to people talk to serve better ads - Inshort
In a shocking revelation, it has come to light that one of Facebook’s alleged marketing partners, Cox Media Group (CMG), has been using sophisticated technology to listen to users’ smartphone microphones and advertise to them based on their conversations.
Tuesday assorted links:
Fee sponsorship | Bitcoin Optech
Fee sponsorship is a proposed consensus change to allow the creation of transactions which effectively add fees to other unrelated transactions, possibly helping those other transactions confirm faster. It’s enables CPFP-like fee bumping without the transactions needing to be related.
🔗 https://bitcoinops.org/en/topics/fee-sponsorship/
---
Soft-Fork/Covenant Dependent Layer 2 Review
Excellent piece from Peter Todd
🔗 https://petertodd.org/2024/covenant-dependent-layer-2-review
---
Crafting Interpreters
Monday assorted links:
Programming ZKPs: From Zero to Hero
Learn to write and modify Zero Knowledge Proofs from scratch. You'll build a digital signature scheme using hash-based commitments, gaining practical ZKP programming skills and intuition along the way. By the end, you'll have all the tools you need to implement things like group signatures.
🔗 https://zkintro.com/articles/programming-zkps-from-zero-to-hero
---
Encryption in France - ATICA European Association of Trade + Investment Controls and Compliance Attorneys
Eu consigo ver.

Sunday assorted links:
Post Quantum Cryptography for non-cryptographers – Key Material
NIST has standardized three new algorithms, going by the names ML-KEM (aka FIPS 203 aka Kyber), ML-DSA (aka FIPS 204 aka Dilithium) and SLH-DSA (aka FIPS 205 aka SPHINCS+). The first is a Key Encapsulation Method, the other two are digital signature schemes. One thing they all have in common is their comparatively much larger sizes for public keys, ciphertexts, and signatures...
🔗 https://keymaterial.net/2024/08/30/pqc-for-non-cryptographers/
Alternative:
Saturday assorted links:
Resilient Anonymous Communication for Everyone
The Resilient Anonymous Communication for Everyone (RACE) program will research technologies for a distributed messaging system that can: a) exist completely within a given network, b) provide confidentiality, integrity, and availability of messaging, and c) preserve privacy to any participant in the system.
🔗 https://www.darpa.mil/program/resilient-anonymous-communication-for-everyone
---
PrimeReact - React UI Component Library
The ultimate collection of design-agnostic, flexible and accessible React UI Components.
---
Isocons
Carefully crafted isometric icons.