I thought it was self evident and desirable that relays censor notes. Else how could curate out what you don’t want. (Porn, etc)
I had always assumed relays needed reputations of a kind.
Linux uses LUKS to encrypt partitions and disks for security and privacy. To unlock LUKS-encrypted disks remotely, we can use the Dropbear SSH server on Debian, Ubuntu, or any other Linux distro. See How to unlock LUKS using Dropbear SSH keys remotely in Linux https://www.cyberciti.biz/security/how-to-unlock-luks-using-dropbear-ssh-keys-remotely-in-linux/
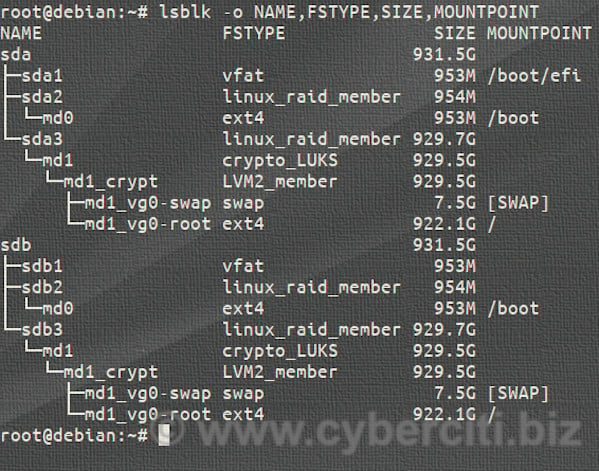
I’d rather go with custom initramfs plus zfsbootmenu.
Can make it even a bit better by only letting ssh listen on a wireguard tunnel.
BOOM
Search static vs dynamic linking.
tl;dr it depends on the language.
Python, Java Script, are dynamically linked.
Golang and some others are statically linked.
C, C++ no simply answer, goes both ways.
This is a good time to mention that there is https://unifiedpush.org/ and that it is supported by #Amethyst, #Element, #SchildiChat, #Tusky, #Fedilab, and other open source #mobile apps.
If you care about this data collection, #OptOut of #centralized push notifications where you can.
How would this help? The problem is not Apple the problem is apps that don’t E2E encrypt their push notification payload.
fyi - Google has the same problem, they just didn’t admit it once they were free to like Apple did.
This is conceptually exactly what Apple Private Relay does. But Apple only does it for select Apps at TCP and UDP layer. This is IP layer.
Apple Relay has some benefits. One example is b/c Apple will not allow IP location spoofing they get blocked a lot less.
I like Apple Private Relay but am definitely looking forward to a generalized solution like this.
bahh. IPv6 is horribly over engineered. It’s like the ISIS gal and telco guys went to town.
It’s not even really IP. If it was they would have bumped the verizon field to 6. nope. Whole different ethertype.
This really is crazy good.
I was kinda of skeptical about no IDs as a user experience. But once you think about decoupling user IDs from pairwise communication channels underneath, the possibilities are endless.
Everything you get from blinded emails and more. You could even make a bridge from an email domain and get exactly that.
Please start thinking about ID layers on top.
Rein In The FBI: Put An End To Their Gestapo Tactics https://www.zerohedge.com/political/rein-fbi-put-end-their-gestapo-tactics
tbh I am a bit confused how the FBI catches all the flack and DOJ gets almost none. DOJ is just as bad if not worse.
wow. now this sounds like progress!! As much as rec.gov app doesn’t suck for a gov app it still takes LOTS of time to plan.
There are already datacenter designs that are in containers.
Only difference would be higher power density of ASICs.
Still working over Safari iCloud+ Anon relay.
LinkingLion: An entity linking Bitcoin transactions to IPs?: https://b10c.me/observations/06-linkinglion/
Use ToR!! Ideally use ToR over a VPN.
well i hadn’t really planned on reading his book so how about citing at least one example.
#[0]
Very important.
What is the correct verb for posting to Nostr / Damus / whatever client ?
The NYDFS at the direction of someone higher up. The NYDFS doesn’t buy a FDIC regulated bank a cup of coffee without permission.
I mostly care because as total shit “crypto” is, it is still not up to these fuckwits to decide.
Why is it so bad for people in Latin America that WhatsApp is extensively used for business? As opposed to any other messenger App?
So by my estimation
Shitcoin strike one: All your banks got knee capped. All the rest got “the message”.
Shitcoin strike two: Ripple will soon be declared a security and you will all be getting nice little notes on SEC letterhead.
Shitcoin strike three: ?? Anyone care to hazard a guess.