There is no "turning on E2EE" with email. It's SSL, like regular websites. Unless you're saying using PGP, which most people are not doing and the metadata is cleartext.
When you say "there are simpler solutions out there", yes Mailu is open source email. We are setting it up for people who do not want to read technical docs. And setting up other services on the same VPS, so you get the most out of having one.
Your argument is unclear. Are you suggesting people should NOT be self-sovereign and have a digital home?
Thanks for your time in writing in for an educational opportunity.
First, Proton is NOT end-to-end encrypted. As per own their blog:
https://proton.me/support/proton-mail-encryption-explained
(Please note, I only changed the CAPS)
Quote:
"The email is encrypted in transit using TLS. It is THEN UNENCRYPTED and re-encrypted (by us) for storage on our servers using zero-access encryption. Once zero-access encryption has been applied, no-one except you can access emails stored on our servers (including us). It is NOT end-to-end encrypted, however, and might be accessible to the sender’s email service"
Second, they do scan it for spam and phising.
They repeat this with:
Source: https://proton.me/blog/encrypted-email-spam-filtering
"Emails that come from third party email providers obviously CANNOT be delivered with end-to-end encryption, but upon reaching our mail servers, we will encrypt them with the recipient’s public key before saving the messages(new window). All this is done in memory so that by the time anything is permanently stored to disk, the email is already un-readable to us. This gives us a very limited window to perform spam filtering on incoming messages."
Then they further elaborate,
"Secondly, the message is passed through our customized Bayesian filters which marks suspicious messages as spam.
Next, we generate checksums of incoming messages and check them against a database of known spam messages. If there is a match, we mark the message as spam. The checksums are done in such a way that it is also effective against mutating spam emails."
So they claim to have it unencrypted, then have a "limited time" to stop spam, but then also claim to encrypt it, and then after compare the hash to spam hash. If their own claims were true, then why do they only have a limited time?
Third, they hand over huge amounts of data. If it's encrypted, then what do they have to hand over?
From their own transparency report:
https://proton.me/legal/transparency
"2023
Number of legal orders: 6,378
Contested orders: 407
Orders complied with: 5,971
2022
Number of legal orders: 6,995
Contested orders: 1,038
Orders complied with: 5,957"
Fourth, you imply that I am not trustworthy but proton with a World Economic Forum board member is. It's not logical to trust a government regulated and registered entity to resist government, over a pure crypto provider. We've registered our PGP key with XMRBazaar so no customer funds are risked when all customers are given a receipt.
What you're really saying is you wish to attempt to haze and oppress alternatives that aren't registered with the government.
If so, why do you have bitcoin glowies on your eyes? As there is no purpose in bitcoin if you still only trust government money.
If you email someone on gmail, that one email is compromised yes. But not the entire sum of all your activity.
So you're protecting against someone seeing everything you're doing.
And further, the vast majority of websites will force you to register using email. So just controlling that email is all the stuff you own. Traditional social media accounts, fiat banking, websites, forums, crypto exchanges, dexes, ect
Also you can use something like anonaddy to hide that it's even you that's emailing gmail. So gmail would only see each conversation in isolation, and not even know your real domain
And tell google what you're buying and where you live?
If you have a self-host, easily one of the many addresses can be for junk.
Yes picking a good VPS provider is important, and that is a flaw with email.
We could re-word your statement as "Email isn't good for active threats, but if the provider wastes money, then information can be obtained"
However, you do not present an alternative.
Email ain't designed for selling fuckin cocaine.
I promote the idea of self-hosting email on a VPS, to stop passive surveillance. Meaning:
No AI is scanning this stuff. Then you can use aliases like anonaddy to hide from services that it's even your email
Proton openly admits to scanning btw. So without a VPS, you got Cloudflare, Gmail, Proton, and the WEF glow boys shoving the AI scan up your rectum, and seeing the SUM of your online activity, because almost every service out there demands an email.
Is it air-tight end-to-end-quantum-nuclear-shelter? No. But it's a little digital home for your work (docs, files, content):
The line between personal and means of production gets blurred to become meaningless. For example even right now I'm talking in a personal sense, but I'm also selling a business.
I am not willing to comply with your call to action, so it's pure violence if you get your way. I will resist to the best of my ability and try to kill you.
If your violence does work, then
To get around your violent call to action, I would declare everything personal. And then use barter trades to avoid money. Everything is personal.
Agreed. But if you control your identity, why would you pick the Rook over the Queen or King?
Microsoft’s latest security update has ruined dual-boot Windows and Linux PCs
Just when you thought you could try Linux out, and still have Windows with dual-boot as a back-up for some use-cases, Microsoft is out to screw you over again. Their new update to "secure boot", which fixed their previous issues with GRUB and Windows together, which Microsoft allowed to be abused by hackers for 2 years before finally patching, now is breaking Linux machines.
"Ars Technica reports that multiple Linux dual-boot users are seeing “security policy violation” messages, along with “something has gone seriously wrong” errors. There are reports of issues across Reddit, Ubuntu forums, and elsewhere. Distributions including Ubuntu, Debian, Linux Mint, Zorin OS, and Puppy Linux have all been affected by Microsoft’s patch."
It looks like you may have to finally pull the plug and wipe even your back-up Windows that you left for compatibility. Microsoft is so corrupt and worthless, they can not even be trusted as an alternative at boot time.
Sources:
https://www.theverge.com/2024/8/21/24225108/microsoft-security-update-windows-linux-dual-boot-errors
Joe Biden pushing forward rapid "Digital ID" program.
According to NOTUS, they previewed a draft executive order that Joe Biden is trying to push through on his way out, [1]
This unconstitutional, insecure, and objectively-invasive program would force states to issue digital identification on smart phones instead of physical driver licenses. What is not mentioned in any of these articles, is how they are going to deal with hackers only having to steal a file. And then once the "file" is stolen, there would be rampant fraud that would be difficult or impossible to stop.
Are you going to tie it to only be used by that physical phone? That would force US citizens to buy certain phone brands, which a US Federal Court already ruled unconstitutional with Obamacare attempting to force young people to buy private insurance. [2] In fact, with health insurance, even with the fines, millions of US citizens preferred to pay the fines than take action. [3]
So how will sleepy Joe Biden force compliance, as he's forced out of office, due to being too senile to speak in a debate? He could not even maintain the illusion of being in charge, while his puppet masters were really in charge.
Here’s an idea: Let’s Phone-Digital ID the White House, so we can see who is really pushing the buttons. Because to say Biden is in-charge, is fraud.
Sources:
Yeah I thought so too. I'm big on composability, and I've never been keen on every social type client needing it's own image viewer, media player built in, I like to click something and have it open in it's own thing, I already have a dedicated media player on my machine. And I'm big on leveraging existing tools to solve problems. I'm also not big on web apps, I loathe them.
Actually I was brainstorming with nostr:npub14slk4lshtylkrqg9z0dvng09gn58h88frvnax7uga3v0h25szj4qzjt5d6 and came up with the idea trying to help him solve a problem and loved the idea so much I started working on it. I haven't talked much about it with anyone outside of that and I wanted to have it done a few months ago, but I've got the software right now to a point where it's doing all the nostr stuff, I've got the options and command line arguments specced out and partially implemented, now I just have to interface with a torrent daemon and do the torrent stuff, creating torrents, seeding, connecting to remote daemons over RPC, publishing to trackers and DHT, that whole part. Once that's done and it is working I'm gonna publish it and begin shilling it here.
excited for this
Ha, I guess. But why would they trust me over just saving up in a wallet they own? It's sort of like a weightloss deal to themselves? "I will become private"
nostr:npub14slk4lshtylkrqg9z0dvng09gn58h88frvnax7uga3v0h25szj4qzjt5d6 have you ever considered layaway for your phones and such?
For a phone being shipped for monero, how would that work? Because we're not collecting credit info the way those companies do. It's not like I'm gonna show up at your frontdoor
"Google Play is axing its Security Reward Program"
The program paid devs up to 20k to locate vulnerabilities in popular Android apps. Google says they’re "winding down the program due to a decrease in actionable vulnerabilities reported by security researchers"
In other words, they no longer give a shit if there's malware on Google Play, because now they changed the legal liability to be on the app dev. Over a year ago, they changed the legal wording so the dev has to self-report what permissions are used. This shifts responsibility away from the Play Store onto the dev.
But if Google shifts the responsibility on the dev for the bad side, but they keep the good side (collecting user data), then why do we even need them? We don't. Avoid Google Play... switch to F-Droid, APKs, and Obtainium.
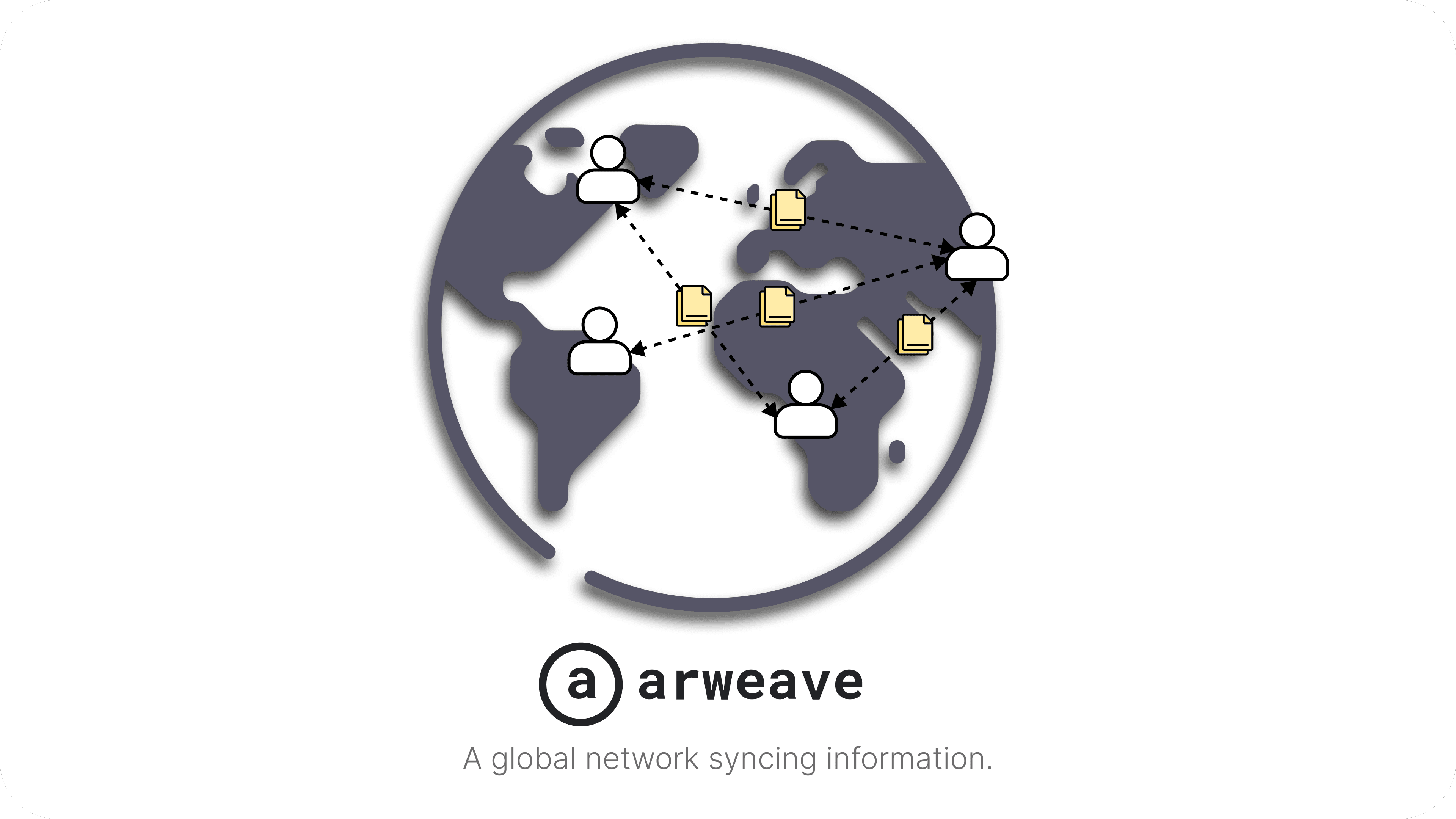
Bitcoin has no binding contract, so Arweave is required. Do not think of it as money, but a decentralized service that takes in revenue. It's more like a coupon.
Why should I care about Arweave websites?
Arweave offers unprecedented freedom for both the website visitor and the content creator.
For the website visitor, it’s unprecedented privacy. Never before in the history of the internet has the website VISITOR been able to pick the location, ISP, and jurisdiction where they want to RECEIVE the content FROM. In other words, you pick what gateway (and therefore under what terms) you will look at their stuff.
Normally, you’re forced to submit to whatever server the content creator wants. Which usually means forced Cloudflare and AWS.
Even better, once it moves out of testnet, you’ll be able to self-host your own gateway. In other words, you can SELF-HOST THEIR website, and then only you see your VPN/Tor exit.
Creator
For the content creator, it’s unparalleled power with: censorship resistance, a CDN, a DNS identity, with no clear-path to a take-down. You can do whatever you want, and governments can’t control you. Even better than that, because it’s permanent, it can serve up unmodified code in a Github type situation, or it can be a legally binding contract for full-blown crypto-anarchy.
How’s it work?
It’s file storage directly on the layer-1 blockchain, so it works like Bitcoin Ordinals but it scales. It can store anything, including websites or videos. And it has gateways around the world, acting as a CDN.
Who cares about this CDN?
The problem with the regular internet is Cloudflare acts as the middle-man for all websites and sees all passwords. However, to not use centralized CDNs exposes one to DDoS. By putting it on the blockchain and having different gateways serve it up, it frees the visitor and the creator from Big Tech, censorship, and having Cloudflare own all passwords.
How’s the blockchain work?
So there’s two aspects to this, first is how is it stored on the blockchain (Proof of Work). And second is how is it distributed to the website viewer (Proof of Stake).
Proof of Work Storage

The storage runs on modified Proof of Work using RandomX (Which Monero also uses). Just like Monero, Arweave uses RandomX to force mining to be done on regular computer hardware, and keep out abuse that can rig the way data is put into blocks. But unlike Monero which is just cash, Arweave is a decentralized business that generates revenue.
BitTorrent Pool
Customers pay for 100 years of storage which goes into a pool (they use the word “endowment”, but it’s not controlled like that). This pool pays out nodes to store the data. They share data with each other using BitTorrent, in a way that incentivizes them to share it with as many other nodes as possible. Then they are randomly asked to produce data, to prove that they have it.
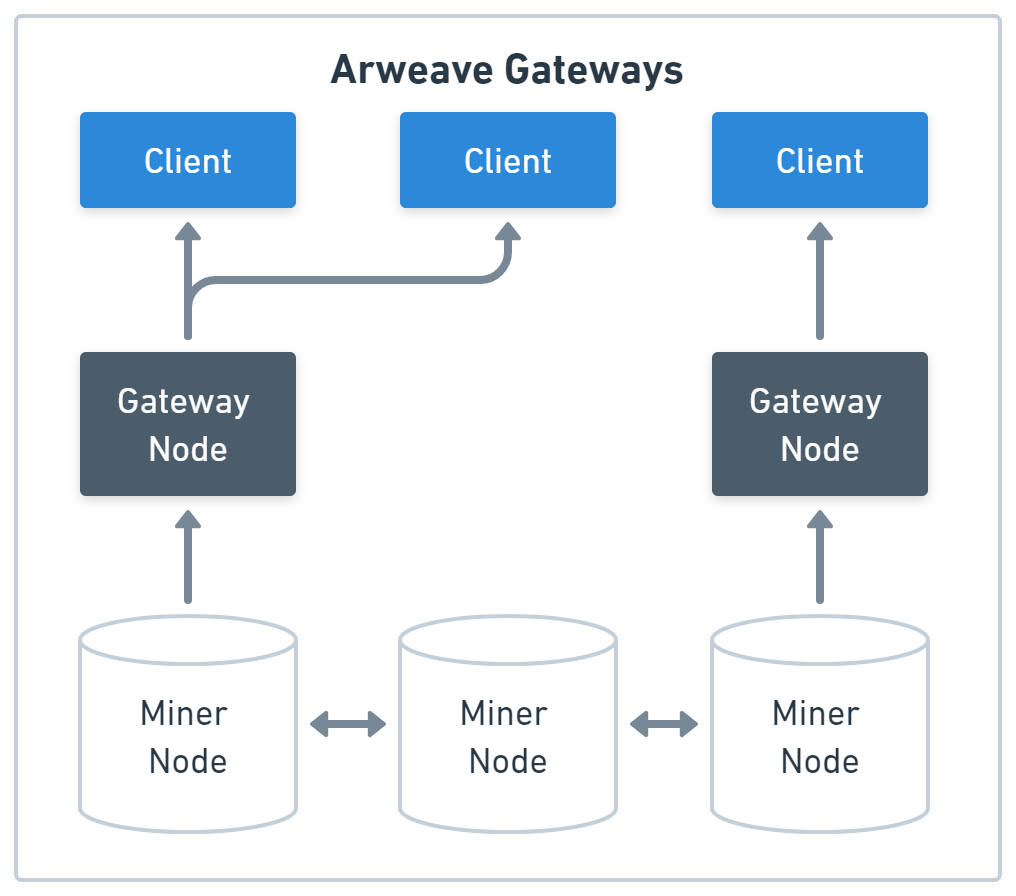
Proof of Stake CDN
The CDN gateways are run by a different project, ar.io (IO tokens) which are Proof of Stake. The gateways stake IO, which gets slashed if they serve malicious fake content. Like say you put up your Monero wallet or PGP Key, and they serve up their own wallet or key. The other gateways can decide what defines malicious content in a vote, and so having the coin be Proof of Stake keeps out malicious attacks. One CAN run a gateway WITHOUT staking, but then the gateway doesn’t get rewarded.
PoS debate
Proof of Stake is controversial, because you’re raising the requirements to scale new locations. However, if there was 0 barrier to entry, then the government could run unlimited malicious gateways with no defense mechanism. The main part of this system I disagree with is the subjective and unclear deciding of what defines malicious gateways. In my personal opinion, it should be mathematical comparison of the files, done in a purely systematic method, without voting.
End Flow Chart
It's possible you had issues with a Monero node, sure. It's possible.
But without a doubt, the end user using a Monero wallet is easier than self-custody Bitcoin lightning, especially if we're talking self-liquidity. And this is why it's more easily controlled, because the end users give up custody/control, to make it easier.
There are other reasons as well, such as privacy, censorship, and legal complexity of layer 2 middlemen.
Thanks for your time. Yeah XMRBazaar is glitched on the 2-of-3 multi-sig, so we offered an alternative and they were down
Simplified Privacy is now regulated...
Just not by the government.
People pay the government to register a business, but when the customer is cheated, does the customer get any of those corporate registration funds? No, the gov squanders it, and then more must be collected via violent threats.
Even worse, "privacy" companies register to get fiat investments, which then forces them to compromise their product at arbitrary corrupt request. Their "innovative" technology can't resist the violent registration, and so they have no purpose.
But how can customers be protected if cryptocurrency transactions are irreversible? Today we present a new path.
Simplified Privacy deposited 2 Monero with an arbitrator from XMRBazaar and registered it with our PGP key. Regardless of if you use XMR, Bitcoin, or a different currency: All customers get a PGP signed receipt for decentralized email combo clouds, private DeGoogled phones, or other tech services. And this is regardless of if you use the the Bazaar website, Nostr, or any messenger. In the future, I am open to doing a Bitcoin deposit as well to bridge the gap.
If we fail to deliver on our promises, you can contact the arbitrator (AilliA), and show your PGP signed receipt. If we fail to respond or provide proof of delivery within 2 weeks, AilliA will pay you XMR from our deposit. My message is clear:
You are not defined by the dirt upon which you stand.
But by the value you add to society.
Deposit info: https://simplifiedprivacy.com/how-pgp-insurance/index.html
Learn how to verify PGP: https://simplifiedprivacy.com/how-to-verify/index.html
Big Win for Freedom:
Federal Appeals Court Finds Geofence Warrants Are “Categorically” Unconstitutional
Up to one third of all inquires to Google are for user geolocation data. This is where law enforcement asks for the data on all phone users in a given geographic area, because they want to know who might have done a crime. The issue with this is that it violates the fourth amendment, as they are getting a huge amount of other data on other people, completely unrelated to the crime.
This is the exact type of stuff we advocate avoiding with Simplified Privacy’s educational materials on DeGoogled Phones, WiFi hotspots, and VoIP. However, it appears we are not the only ones against the practice. In the Fifth Circuit case of the United States v. Smith, the Federal Court ruled that geofence warrants, which involve blanket requests for all user data in a given geographic area, are unconstitutional and violate the 4th amendment.
Now will this stop the practice? Maybe, but I wouldn’t cancel your VoIP subscription yet.
