ermmmm... i hope they ain't series 5s
https://www.yubico.com/support/security-advisories/ysa-2024-03/
here is some reticulum + cashu work by juraj some time ago, code linked in the video description
pitch:
fork Insular
https://secure-system.gitlab.io/Insular/
Find way for it to run only in RAM with extremely limited functionality
Make the container amnesic with forced refresh and routine RAM rewriting
Discover the nightmare fuel that is the Android stack
???
not-profit
The most cypherpunk as fuck podcast.
I highly recommend listening through it from the beginning. Smuggler and nostr:nprofile1qqsxd7rasz53jav2vjlq6twg5wj68lgvm0t4lj79skkka9jju8qfv3cpzpmhxue69uhnzdps9enrw73wd9hszxthwden5te0v9j82mr59ccnsurvw4ejuum0vd5kzmqpzfmhxue69uhhqatjwpkx2urpvuhx2uc9a2xcy are two legendary builders, strategists, and philosophers. Their mindset and articulation is inspiring.
+1
cashuAeyJ0b2tlbiI6W3sibWludCI6Imh0dHBzOi8vbWludC5taW5pYml0cy5jYXNoL0JpdGNvaW4iLCJwcm9vZnMiOlt7ImlkIjoiMDA1MDA1NTBmMDQ5NDE0NiIsImFtb3VudCI6MSwic2VjcmV0IjoiMDcxOTMyNWRjNzY1NTAwODA0MmNjN2Y4MTYzNGQxNDdlNzJkMDBkNDdiNjJmNGJiZDQyMWI1MDBiYTY0NDA3YiIsIkMiOiIwMjRhNTlhNmUyOWQxNDgyM2JiMmExNWI2ZDAwYjk3YzQ0MjY2ZjczZjAxMGIyZGRjZDUyZjdkOTY0N2E3MjZlYzcifSx7ImlkIjoiMDA1MDA1NTBmMDQ5NDE0NiIsImFtb3VudCI6NCwic2VjcmV0IjoiMjc5ZDM3OGFlOTQ3MWFlMmI1MjU0MjcyZmNjNTFlNzNkZDc2MzUxMmI5NzAwNzJmMDFiZDkzZTAxY2Q1OWNlOSIsIkMiOiIwMzM4NzdhYTUzODU2N2JkNDFkMmVmOWE2ZTMxNjJmZDg5MGViNTUyZmNhNWEzYjlhYmU3ZThkOWIyY2Y0ZDE0ZmIifSx7ImlkIjoiMDA1MDA1NTBmMDQ5NDE0NiIsImFtb3VudCI6MTYsInNlY3JldCI6IjZmMjM1MjczYTNhZjAwNzgwNmNhNDNjY2NmYTNiMzZkZGEwZTc0NTExNjYzYzUwNDEzNTVjMTg2N2QyYjM5N2EiLCJDIjoiMDNhYmQ0N2I4OTc5NzJjNmU0ZTE2YWFjNmJlNmI1NjdkZDg5ZmE1ZWM1NGExNmM2NjA3MWY4ZTQzYmVjYTU5ZmIxIn1dfV0sInVuaXQiOiJzYXQiLCJtZW1vIjoiTW9yZSBudXRzIGZvciBkZW1vcyJ9
respect to the researcher's ethics
"2.4 Ethical Considerations
As far as the practical evaluation of the presented attack is concerned, we followed the guidelines of the Menlo report [5] and general security research best practices.
In particular, with the exception of obtaining a network snapshot from our own node, we did not interact with the public mainnet in any way. We deployed a modified version of our proof-of-concept implementation to the testnet in order to validate the feasibility of the attack’s preliminary phase. However, at no point did we actually mount the attack in the testnet.
All adverse experiments were conducted in our private network comprising only nodes we set up for the precise purpose. In order to evaluate the potential impact of our work on the main network, we followed a simulation-based approach using the obtained snapshot. The simulation mocks payment routing in the network by reconstructing the topology locally."
Payment Censorship in the Lightning Network Despite Encrypted Communication
The authors demonstrate how to detect LN messages by their deterministic sizes and packet flows. These methods allow a network-level adversary to identify and censor payments in the Lightning Network.
😱
Paper: https://drops.dagstuhl.de/entities/document/10.4230/LIPIcs.AFT.2024.12
Run #LND? get a #TOR running partner
#lightning #privacy #research
Payment Censorship in the Lightning Network Despite Encrypted Communication - Charmaine Ndolo & Florian Tschorsch, 2024
"5.2 Towards a solution
...
The purpose of doing so is to utilise Tor’s implementation of WTF-PAD and not for Tor’s privacy properties. We issued payments in both directions, closed the channel and finally the TCP connection. Not only did all packets have the same packet length (as is expected when using Tor), but the flow of transmitted packets included packets that did not originate from the application.
Consequently, we were not able to detect which packets belonged to which Lightning message by manually inspecting the capture. The rule-based state machine is therefore no longer capable of distinguishing application messages based on the network traces alone. In fact, we conjecture that this approach offers a high degree of protection for
the LN against more sophisticated fingerprinting techniques by network-level adversaries as basically all size and timing features are destroyed.
...
Specifically, we concurrently captured the packets sent locally between the LND node and the Tor SOCKS5 proxy, as well
as the packets sent between the Tor process and Tor network. The former provides data on the packets that actually come from the application while the latter provides data on what a network-level attacker would observe. The captures show a total of 14, 824 bytes transmitted
in 379 TCP packets to/from LND and 929, 596 bytes in 3191 TCP packets to/from the Tor network. This equates to an increase of ≈ 6170% in bandwidth when using Tor. The captures also show a peak rate of 0.116 Mbit/s when using Tor, which clearly should not cause any problems for LN nodes while maintaining their current hardware configurations."
gitlab / gitea?
there were some nostr-based git protocols being thrown around, but did not follow their develoment or remember the name
Why Angor.io is unique?
✅️ Funds are released through time-locked contracts. When milestones are reached, funds are unlocked.
✅ If founders buy lambos investors pull funds.
nostr:npub182muyyy9yjmarsw9shcfcxm7r984uleztfdmj3ln0rs8f46wnklstahf3j
not production but I stumbled across nostr:nprofile1qqsr4d7zzzzjfd73c8zctuyurdlpjn670u395kaegleh3cr56a8fm0cpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uq3wamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmny9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcmut80v recently thanks to nostr, came here thanks to a nostr:nprofile1qqsypwwgtll74lqu4huvxzjwtjyxvrlkujt35rw8y026ke6ttesmg5gpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7qg5waehxw309amk7apwvaa82at49eu8j730rlqdev boost
you might also like this recent discovery of the largest prime number
This boy SAVED the INTERNET… but couldn't save himself.
10 years ago, he was persecuted by his government, and ultimately paid with his life.
Aaron Swartz is a modern hero that most people DO NOT KNOW.
But they should.

Aaron was creative, focused, and brilliant.
At 14, he invented RSS; He dropped out of Stanford; At 19, he was in the first Y Combinator class; He co-founded Reddit.
Most likely, if he were alive today, he would be involved with #Bitcoin.
But that’s not EVEN 1% of what he did for us 🙏
Let’s take a look 👇

From a young age, Aaron believed in an OPEN INTERNET. In computers as a tool for LIBERATION.
"But wait, wasn’t the internet always open?"
No.
Believe it or not, there was a time when they wanted you to REGISTER your ID before you could browse or send an email.



He believed that PUBLIC LEGAL RECORDS and SCIENTIFIC RESEARCH should be accessible to everyone.
But in the U.S.,
• 98% of scientific articles are behind paywalls; and
• ~80% of legal records are too.
Imagine being sued and still having to pay to view the documents?
https://video.nostr.build/2af872c7a7d1b74ce0fb8d42369a87df45a7ee2d23df006d287b58ac60fcfe26.mp4
Aaron's war had 3 major battles.
The first was against PACER.
A legal records database.
PACER is PAID... but it was "free" in 17 public libraries.
With friends, Aaron wrote a script on a USB drive, plugged it into a USB port, downloaded 2.7 million documents... and SET THEM FREE.
https://video.nostr.build/21b565dd1742bc950748be2ac0e0ce2868f4b94c54d1da9321a198c49fe85d1e.mp4
No charges were made against the group.
But the FBI began to take notice.
That had only been the beginning. That boy would still challenge the system.
The following year, Aaron would enter the biggest fight of his life — and the greatest battle in internet history against censorship ✊

"SOPA/PIPA" 👉 if you're over 20, you probably still remember these acronyms.
A bill to "combat piracy"... which was just an excuse for the government to shut down ANY SITE, without warning.
Some companies loved the idea.
But those who loved the internet fought back.
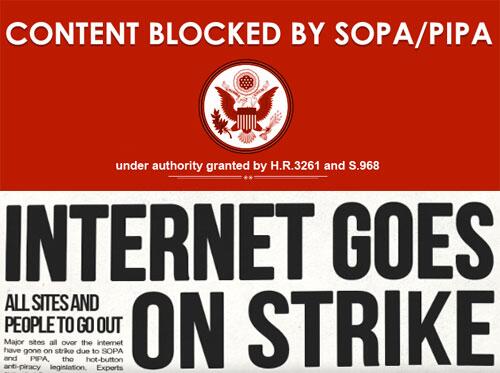
And then, something wonderful happened.
We still knew how to fight against online censorship.
In a coordinated response, the biggest websites on the internet "went on STRIKE."
Wikipedia and Reddit went offline. Google turned black.
Protests also erupted in the STREETS.
But...

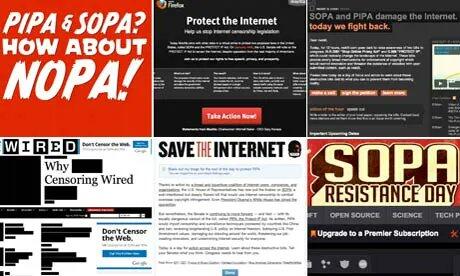


... but people have short memories.
This battle was won.
However, the NEXT one would be the LAST for young Aaron.
This MIT security camera was the final straw that ruined his life 👇📹

JSTOR was Swartz's final target: the largest database of academic papers in the world.
Aaron wrote a script to download MILLIONS of papers, over the course of months, using his MIT access, in a small room.
MIT has a rebellious culture.
But the FBI could no longer tolerate the boy's defiance.

With the video evidence, the U.S. prosecution charged Aaron with 13 crimes. Up to 50 years in prison.
In January 2011, he was arrested by undercover agents near the Harvard campus.
From then on, he was legally tortured.
Two years later, he would be found dead at home.
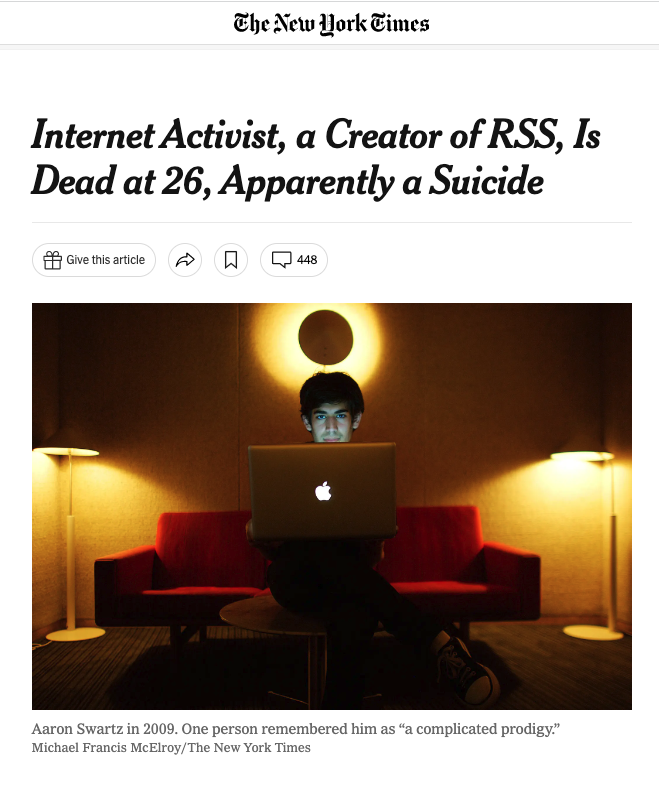
"Aaron would be 38 years old today.
He was accused of 'pirating' scientific papers funded with public money.
Facing up to 50 years in prison, he took his own life.
Those he inspired continue to democratize access to science.
Let us remember him."
*These are the words of Susan, his mother.

After his death, the charges were dropped by the government.
Aaron never considered entering a 'plea deal'. He would have faced millions of dollars in legal costs.
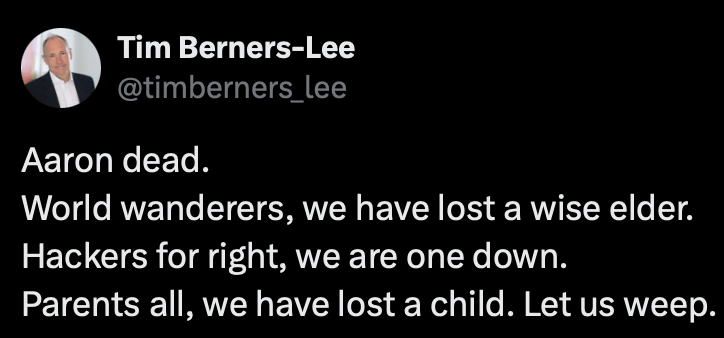
The father of the internet, Tim Berners-Lee, published a short poem at the time that says it all:
“The world was a little worse for his passing,
But a lot better for his being.”
Aaron wasn’t a unanimous figure. You may disagree with his methods.
But he was faithful to his ideal.
He was genuine. Firm in what he believed.
He was a person who used his prodigious skills not to enrich himself, but to make the internet fairer, and the world a better place.

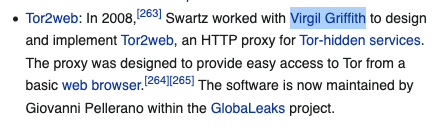
Aaron had worked with Virgil Griffith (former Ethereum, now imprisoned for "teaching about crypto" to North Koreans).
He knew Elizabeth Stark (from Lightning).
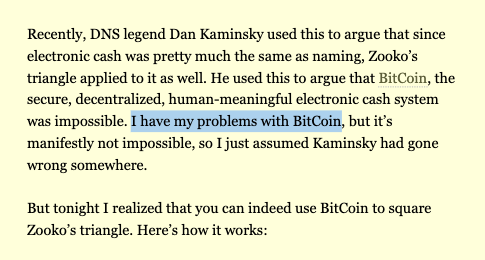
He was friends with Zooko.
And he wrote about #Bitcoin — on the DAY he was arrested (1/6/11)! 😢
http://www.aaronsw.com/weblog/squarezooko

Curious? To learn more about the story, start with this documentary (on YouTube) 👇
[https://youtu.be/9vz06QO3UkQ](https://youtu.be/9vz06QO3UkQ)
We’ll finish with an excerpt from the "Manifesto for Free Access," by Aaron himself:
"Information is power. But, like all power, there are those who want to keep it for themselves. There is no justice in following unjust laws. It’s time to come to the light, and, in the tradition of civil disobedience, declare our opposition to the private theft of public culture.
We must take information, wherever it is, make our copies, and share them with the world."
RIP, Aaron ✊



cashu is the spec
minibits a client running cashu
like what nostr is to (your nostr client)
or never use it again
turning point
12.5 year of captivity after some bad statistics by chainanal point to your UTXO
horrible precedence
It is probably a crime to change your IMEI in that nation, don't suggest solutions which will get peopke in trouble



