I’m not surprised from “We The People” though. They’re just tacky larpers.
The key ID is the lower 32 or 64 bytes of the fingerprint. You can think of the fingerprint as the “full ID”.
You’re welcome. Message me any time!
My wife is a semi-pro samba dancer. Her group is one of the most warm and welcoming people I have ever met. Wonderful community.
It's called the "fingerprint". You'll see it in the output of `gpg --list-keys` under your pub.
You can search for keys with the fingerprint with tools like https://keys.openpgp.org
I haven’t worked on many projects/platforms I didn’t think were terrible lol
I'll keep surfing forums and nostr:nprofile1qqs0nt9skq6vfsgh06v979rrnuchau87mmnk2lqxpv2xaeusqfp30mqpzamhxue69uhky6t5vdhkjmn9wgh8xmmrd9skctcpzemhxue69uhk2er9dchxummnw3ezumrpdejz7qgwwaehxw309ahx7uewd3hkctc9ad278 guides as I go, but if I get real stuck I'll reach out for help I barely understand 😂🫂🫡
Best unsolicited advice I can give is have a solid recovery plan and test it.
It can be a little harrowing but knowing you have a solid recovery will set you at ease.
Ohhh sim sim sim, ohhh nao nao nao
Been hosting a node for about 4 years now. If you want any advice I’d be glad to help.
Feels good to own your own node!
Worst Holster Product #grownostr #guns #gunsafety #comfort #marketing #pewpew
https://youtube.com/shorts/r0VDko8Fz14? https://video.nostr.build/a5c65a42587e41d9e06bb3084dc2642d00fbfc43a8073469521e4dcaa5e0d805.mp4
No off body carry. Ever. That thing is with me.
That worst case is hilarious
Congrats on the activation! Cool spot
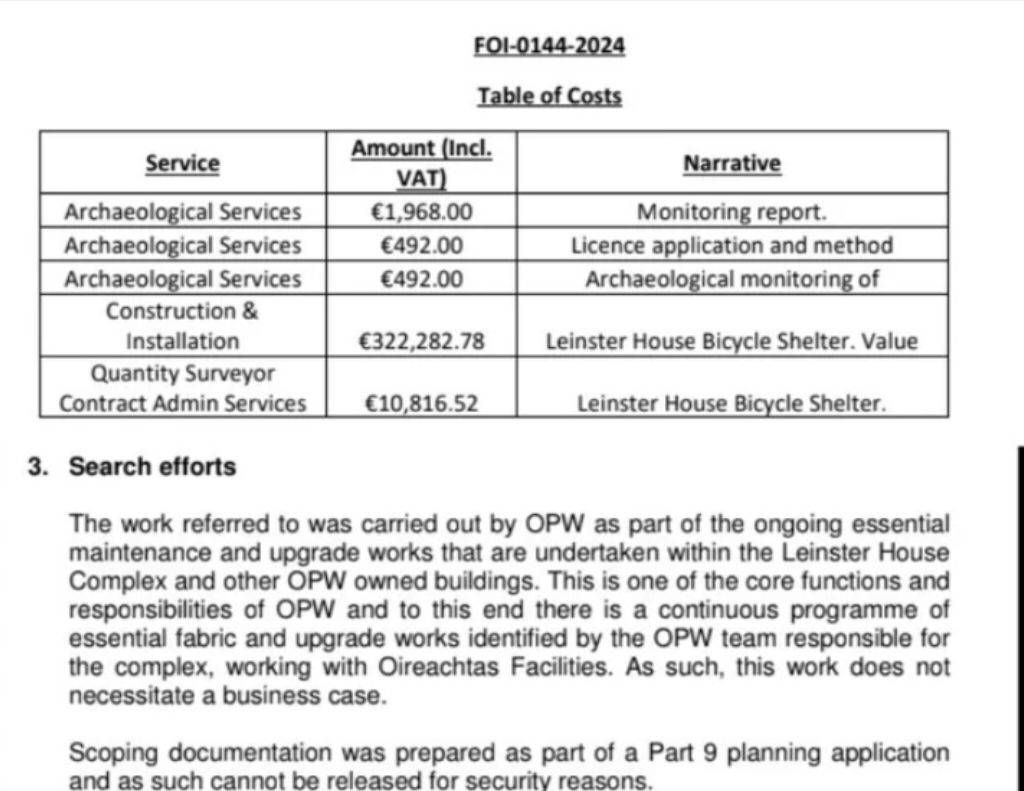
I frankly don’t understand how we haven’t put boots down to go get those people.
I often wonder if he’s out here somewhere. I just wonder what he thinks about how this whole experiment is going.
Very nice. Permanent install or do you do portable op?
Currently reading Broken Money by nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
What a banger 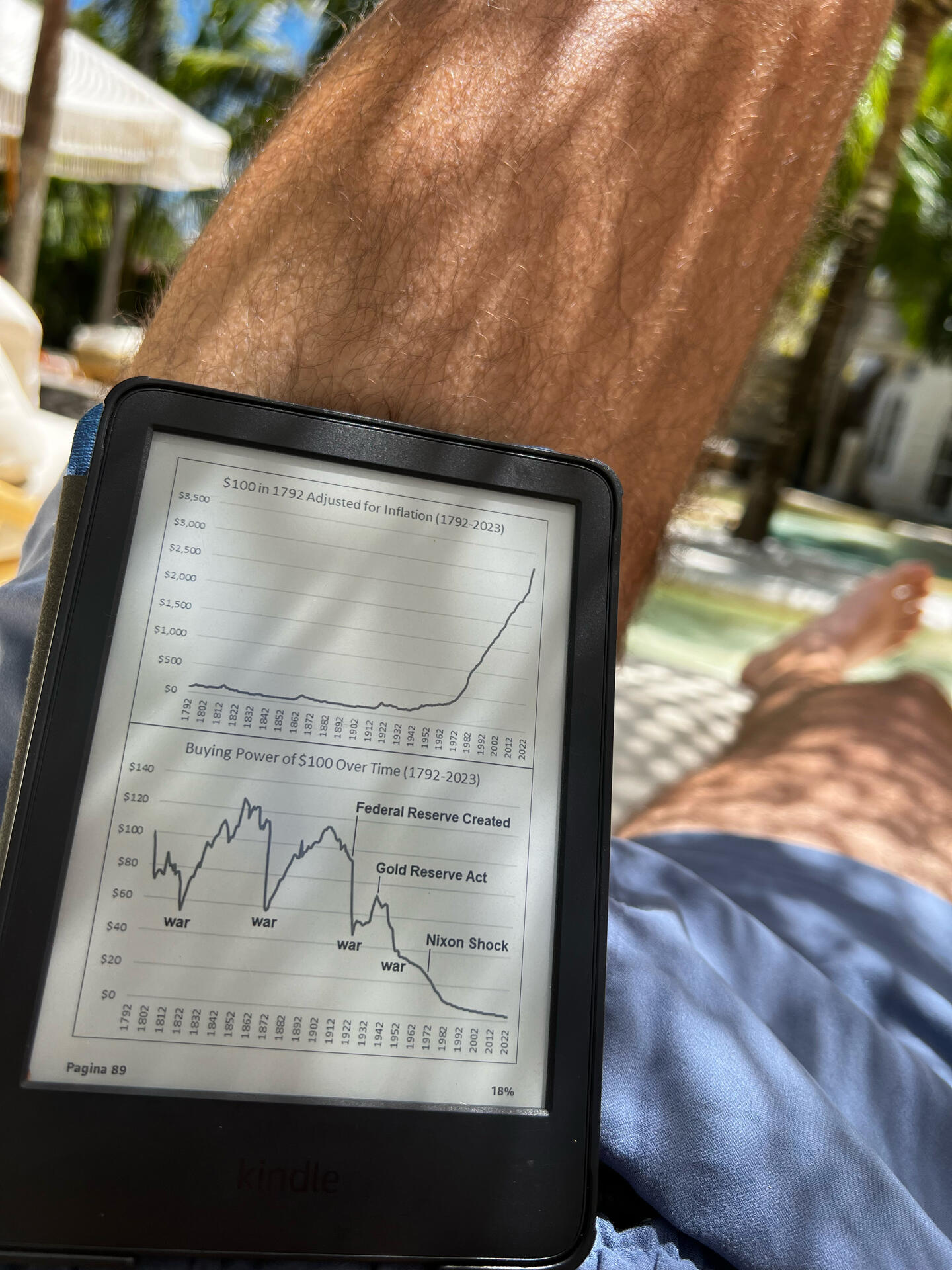
It’s good stuff! I listened to the audiobook so didn’t get to check out the graphs.
Upside is I got to listen to nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev read me bedtime stories 😆
These models are static, and they take hundreds of millions of dollars of compute to train. So they’re not up to date with current events. It’s VERY well documented. The models just make shit up. It’s literally how they work… Don’t trust what they say.
Not everything is a conspiracy and it’s exhausting that people look for them in bullshit like this.
These things hallucinate all the time. Don’t trust em 🤷♂️