"The Fed in Flames"
by Alex Schaefer
Oil Painting
#federalreserve #endthefed #banks #centralbanking #fractionalreservebanking #nationaldebt #cuckbucks #bitcoin #modernmoneymechanics #centralbank #fiat #federalreservenotes #fed #banking #aislop #brainmade #painting #oilpainting

NVM
#nostr
I would, essentially for the same reason nostr:nprofile1qqsx0z3s3evuynhpkdptpl56hhm0m7jaenps46e8tffhu8ml5psfl0qppemhxue69uhkummn9ekx7mp0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9uq3qamnwvaz7tmwdaehgu3wd4hk6tcazwwt9 mentioned
Funny you say this. In Stirner schools this is the age when they teach about revolutions. It has something to do with biology and hormones, a young teenage male is essentially in a continuous state of revolution against their parents, their teachers, and even themselves.
'If you aren't a socialist by the time you're 12 you have no heart, if you're still a socialist by the time you're 14 you have no brain"
- John 21:12*
*possible misattribution
It would be quite rare for the entire internet to shutdown, but as they say, prepare for the worst and hope for the best. On the other hand it is easy for a nation to implement a comms blackout (example, Egypt 2011), or espionage targeting submarine telexommunication networks (image attached).
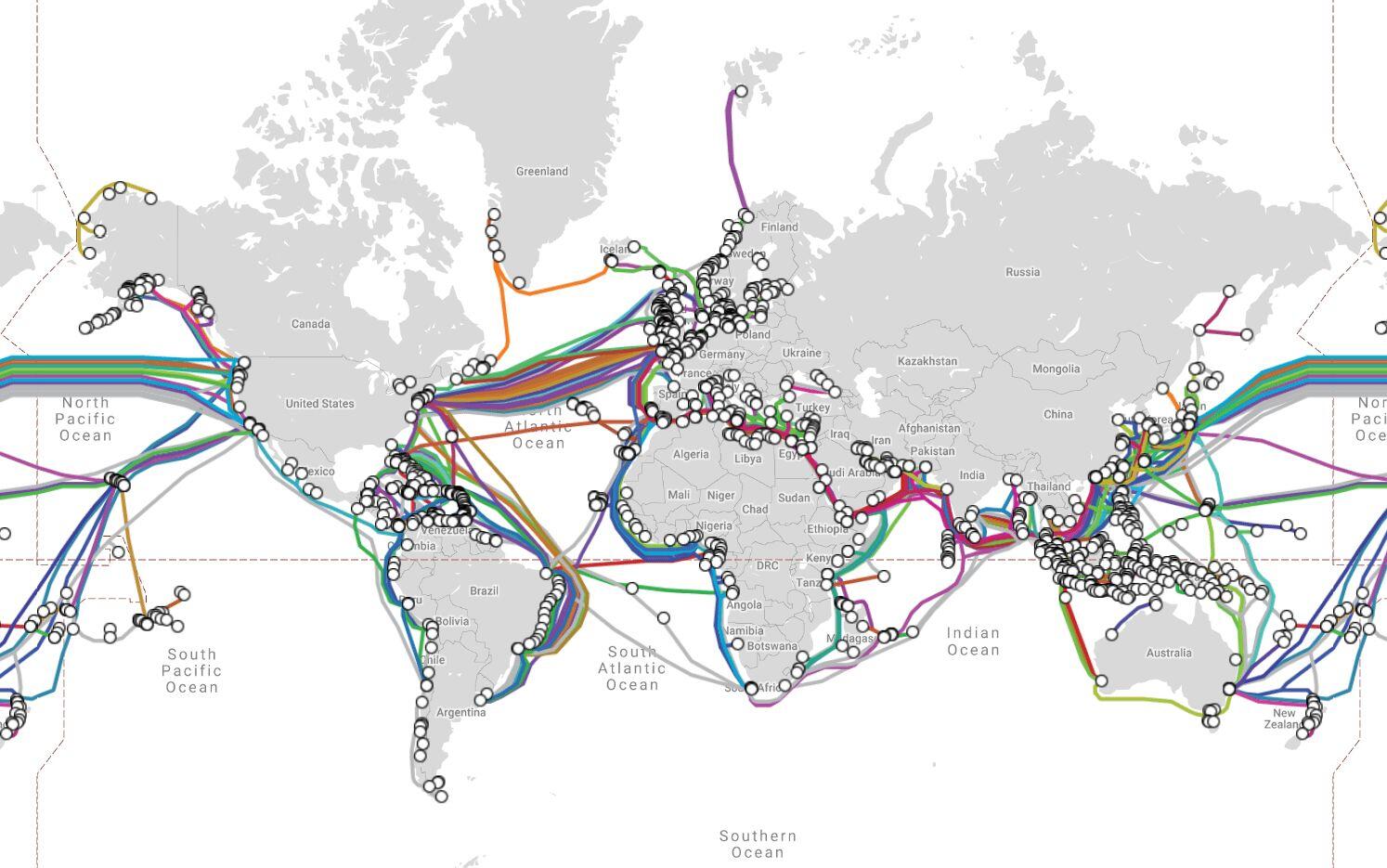
I think the answer may be in further decentralization of data networks such as https://reticulum.network/ - LoRa has the ability but scalability seems to be an issue, and will require at least one gateway to the internet.
The Crypto Anarchist Manifesto
Timothy C. May
tcmay@netcom.com
A specter is haunting the modern world, the specter of crypto anarchy.
Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner. Two persons may exchange messages, conduct business, and negotiate electronic contracts without ever knowing the True Name, or legal identity, of the other. Interactions over networks will be untraceable, via extensive re-routing of encrypted packets and tamper-proof boxes which implement cryptographic protocols with nearly perfect assurance against any tampering. Reputations will be of central importance, far more important in dealings than even the credit ratings of today. These developments will alter completely the nature of government regulation, the ability to tax and control economic interactions, the ability to keep information secret, and will even alter the nature of trust and reputation.
The technology for this revolution--and it surely will be both a social and economic revolution--has existed in theory for the past decade. The methods are based upon public-key encryption, zero-knowledge interactive proof systems, and various software protocols for interaction, authentication, and verification. The focus has until now been on academic conferences in Europe and the U.S., conferences monitored closely by the National Security Agency. But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable. High-speed networks, ISDN, tamper-proof boxes, smart cards, satellites, Ku-band transmitters, multi-MIPS personal computers, and encryption chips now under development will be some of the enabling technologies.
The State will of course try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy.
Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions. Combined with emerging information markets, crypto anarchy will create a liquid market for any and all material which can be put into words and pictures. And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property.
Arise, you have nothing to lose but your barbed wire fences!
---
#cryptoanarchy #cryptoanarchist #bitcoin #cypherpunk #manifesto #timothycmay #anarchy #agorism
Get yourself a pair of these. Side effects include loosing friends quicker than if you joined Scientology. Vibram 5 Fingers. #footstr indeed *needs a cold shower*

What is Fascism? by George Orwell
TRIBUNE 1944
Of all the unanswered questions of our time, perhaps the most important is: ‘What is Fascism?’
One of the social survey organizations in America recently asked this question of a hundred different people, and got answers ranging from ‘pure democracy’ to ‘pure diabolism’. In this country if you ask the average thinking person to define Fascism, he usually answers by pointing to the German and Italian régimes. But this is very unsatisfactory, because even the major Fascist states differ from one another a good deal in structure and ideology.
It is not easy, for instance, to fit Germany and Japan into the same framework, and it is even harder with some of the small states which are describable as Fascist. It is usually assumed, for instance, that Fascism is inherently warlike, that it thrives in an atmosphere of war hysteria and can only solve its economic problems by means of war preparation or foreign conquests. But clearly this is not true of, say, Portugal or the various South American dictatorships. Or again, antisemitism is supposed to be one of the distinguishing marks of Fascism; but some Fascist movements are not antisemitic. Learned controversies, reverberating for years on end in American magazines, have not even been able to determine whether or not Fascism is a form of capitalism. But still, when we apply the term ‘Fascism’ to Germany or Japan or Mussolini's Italy, we know broadly what we mean. It is in internal politics that this word has lost the last vestige of meaning. For if you examine the press you will find that there is almost no set of people — certainly no political party or organized body of any kind — which has not been denounced as Fascist during the past ten years. Here I am not speaking of the verbal use of the term ‘Fascist’. I am speaking of what I have seen in print. I have seen the words ‘Fascist in sympathy’, or ‘of Fascist tendency’, or just plain ‘Fascist’, applied in all seriousness to the following bodies of people:
Conservatives: All Conservatives, appeasers or anti-appeasers, are held to be subjectively pro-Fascist. British rule in India and the Colonies is held to be indistinguishable from Nazism. Organizations of what one might call a patriotic and traditional type are labelled crypto-Fascist or ‘Fascist-minded’. Examples are the Boy Scouts, the Metropolitan Police, M.I.5, the British Legion. Key phrase: ‘The public schools are breeding-grounds of Fascism’.
Socialists: Defenders of old-style capitalism (example, Sir Ernest Benn) maintain that Socialism and Fascism are the same thing. Some Catholic journalists maintain that Socialists have been the principal collaborators in the Nazi-occupied countries. The same accusation is made from a different angle by the Communist party during its ultra-Left phases. In the period 1930-35 the Daily Worker habitually referred to the Labour Party as the Labour Fascists. This is echoed by other Left extremists such as Anarchists. Some Indian Nationalists consider the British trade unions to be Fascist organizations.
Communists: A considerable school of thought (examples, Rauschning, Peter Drucker, James Burnham, F. A. Voigt) refuses to recognize a difference between the Nazi and Soviet régimes, and holds that all Fascists and Communists are aiming at approximately the same thing and are even to some extent the same people. Leaders in The Times (pre-war) have referred to the U.S.S.R. as a ‘Fascist country’. Again from a different angle this is echoed by Anarchists and Trotskyists.
Trotskyists: Communists charge the Trotskyists proper, i.e. Trotsky's own organization, with being a crypto-Fascist organization in Nazi pay. This was widely believed on the Left during the Popular Front period. In their ultra-Right phases the Communists tend to apply the same accusation to all factions to the Left of themselves, e.g. Common Wealth or the I.L.P.
Catholics: Outside its own ranks, the Catholic Church is almost universally regarded as pro-Fascist, both objectively and subjectively;
War resisters: Pacifists and others who are anti-war are frequently accused not only of making things easier for the Axis, but of becoming tinged with pro-Fascist feeling.
Supporters of the war: War resisters usually base their case on the claim that British imperialism is worse than Nazism, and tend to apply the term ‘Fascist’ to anyone who wishes for a military victory. The supporters of the People's Convention came near to claiming that willingness to resist a Nazi invasion was a sign of Fascist sympathies. The Home Guard was denounced as a Fascist organization as soon as it appeared. In addition, the whole of the Left tends to equate militarism with Fascism. Politically conscious private soldiers nearly always refer to their officers as ‘Fascist-minded’ or ‘natural Fascists’. Battle-schools, spit and polish, saluting of officers are all considered conducive to Fascism. Before the war, joining the Territorials was regarded as a sign of Fascist tendencies. Conscription and a professional army are both denounced as Fascist phenomena.
Nationalists: Nationalism is universally regarded as inherently Fascist, but this is held only to apply to such national movements as the speaker happens to disapprove of. Arab nationalism, Polish nationalism, Finnish nationalism, the Indian Congress Party, the Muslim League, Zionism, and the I.R.A. are all described as Fascist but not by the same people.
* * *
It will be seen that, as used, the word ‘Fascism’ is almost entirely meaningless. In conversation, of course, it is used even more wildly than in print. I have heard it applied to farmers, shopkeepers, Social Credit, corporal punishment, fox-hunting, bull-fighting, the 1922 Committee, the 1941 Committee, Kipling, Gandhi, Chiang Kai-Shek, homosexuality, Priestley's broadcasts, Youth Hostels, astrology, women, dogs and I do not know what else.
Yet underneath all this mess there does lie a kind of buried meaning. To begin with, it is clear that there are very great differences, some of them easy to point out and not easy to explain away, between the régimes called Fascist and those called democratic. Secondly, if ‘Fascist’ means ‘in sympathy with Hitler’, some of the accusations I have listed above are obviously very much more justified than others. Thirdly, even the people who recklessly fling the word ‘Fascist’ in every direction attach at any rate an emotional significance to it. By ‘Fascism’ they mean, roughly speaking, something cruel, unscrupulous, arrogant, obscurantist, anti-liberal and anti-working-class. Except for the relatively small number of Fascist sympathizers, almost any English person would accept ‘bully’ as a synonym for ‘Fascist’. That is about as near to a definition as this much-abused word has come.
But Fascism is also a political and economic system. Why, then, cannot we have a clear and generally accepted definition of it? Alas! we shall not get one — not yet, anyway. To say why would take too long, but basically it is because it is impossible to define Fascism satisfactorily without making admissions which neither the Fascists themselves, nor the Conservatives, nor Socialists of any colour, are willing to make. All one can do for the moment is to use the word with a certain amount of circumspection and not, as is usually done, degrade it to the level of a swearword.
1944
THE END
#facism #facist #orwell
A Cypherpunk's Manifesto
by Eric Hughes
Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world.
If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to.
Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must always reveal myself.
Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy.
Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature.
We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.
We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money.
Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down.
Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible.
For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals.
The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace.
Onward.
Eric Hughes
9 March 1993
#Cypherpunk #Freedomtech #Bitcoin
The use of AI art only highlights your lack of creativity and talent. Your memes aren't funny or educational, you are simply responsible for The Dead Internet and Uncanny Valley. Learn to actually create something, not replicate.
#AIart #Brainmade

Missing some math there
https://www.faithandfreedom.com/jeffersons-warnings-about-money-and-banks/
//The Wire//2300Z March 28, 2025//
//PRIORITY//
//BLUF: MAJOR EARTHQUAKES STRIKE BURMA AND THAILAND, THOUSANDS OF CASUALTIES ESTIMATED. DIPLOMATIC ACTIONS CONTINUE IN UKRAINE.//
-----BEGIN TEARLINE-----
-International Events-
Southeast Asia: A very large earthquake (and many aftershocks) struck the region this morning, primarily within the nations of Myanmar (Burma) and Thailand. The epicenter of the Burmese earthquake was located almost exactly under the city of Mandalay, Burma's second largest city. Early estimates indicate the earthquake's magnitude was 7.7, larger than usual for the region. In Thailand, several aftershocks were felt and have caused damage through much of the northwest. A state of emergency remains in effect throughout most of Burma, and parts of Thailand that have been hardest hit. Many skyscrapers and high-rise buildings have collapsed in Bangkok, about 600 miles from the epicenter.
AC: This earthquake is a big deal, with most authorities estimating thousands, if not tens of thousands of casualties spread throughout the region. Right now, numbers are impossible to verify as most communications networks throughout Burma and Thailand (which barely functioned before the earthquake) are simply overwhelmed. Additionally, since Burma has been living under a state of military coup for several years, communications blackouts have been the norm to prevent access to the internet by locals. As such these censorship efforts probably will have a negative impact on determining the scale of the crisis in Burma.
Eastern Europe: The potential for peace in Ukraine remains on the table as diplomatic efforts remain constant. Overnight, President Putin gave a very frank and direct talk regarding his concerns for the war coming to a close. One of his chief concerns is the legitimacy of peace; in short, Putin stated that he's not sure if a peace agreement with Zelenskyy would be legally binding, because he is not the elected leader of Ukraine (referencing the fact that elections have been suspended in Ukraine, and Zelenskyy's term of office expired some time ago).
-----END TEARLINE-----
Analyst Comments: Though many may scoff at listening to anything Putin says, his remarks last night provide some much needed insight into his perspective during negotiations. For instance, from Putin's perspective, regime change is a non-starter. From where Putin sits, Zelenskyy must go even if that means ousting him and creating an interim transitional government while elections take place. Considering his strangely direct remarks, he probably would be amenable to a ceasefire while Ukrainian elections take place, but that's sheer speculation at best.
Rightly or wrongly, and like it or not, Zelenskyy remaining in office is one of the biggest barriers to peace and Russia has made it clear that they will continue fighting as long as he is in power. Zelenskyy himself did make it illegal for any ceasefire or peace talks to even happen with Putin, that is an undeniable fact that is complicating things quite a bit. Of course, on the other side of the issue, Russia wants to come out of this war in the best position possible, and a transitional government where everyone is vying for power would be politically advantageous to Russia.
Fundamentally, opinions will vary on what is happening as long as those interpreting the diplomatic efforts adopt certain opinions. For instance, if a person thinks that Putin is hellbent on taking the entire continent of Europe, one analytical perspective will be adopted. If a person thinks that Putin just wants to make a minor land grab and isn't interested in land outside of Ukraine, another analytical perspective will be used. This is one of the major reasons for analytical discrepancy throughout the conflict, and is why the terms of a peace agreement might be confusing to many people who had believed one set of beliefs about the war for so long that at war's end, the reality of the situation might be hard to understand.
Analyst: S2A1
Research: publish.obsidian.md/s2underground
//END REPORT//
#Myanmar #Burma #Thailand #Earthquake #Ukraine
Given the issue with their browser and it's sneaky relationship with Microsoft I don't have a lot of faith:
https://www.tomsguide.com/news/duckduckgo-privacy-browser-facing-backlash-over-microsoft-trackers
In saying that the name is cool because it will possibly attract users who type "fuck AI" and it autocorrects to "Duck AI"
Personally I try not to interact with AI prompting because of the Uncanny Valley feeling but I have found Braves Leo AI to be good - but my lack of AI experience doesn't qualify me to rank them.
When looking at privacy concerns with Leo AI all that comes up is the communities voice and no actual privacy issues (to date).
//The Wire//2300Z March 27, 2025//
//ROUTINE//
//BLUF: VEHICLE RAMMING IN BERLIN, MASS STABBING IN AMSTERDAM. WILDFIRE SEASON RISKS INCREASED DUE TO HELENE DAMAGE.//
-----BEGIN TEARLINE-----
-International Events-
Germany: Overnight a vehicle ramming attack was conducted in the Gesundbrunnen district of Berlin, resulting in multiple casualties. So far 6x people were wounded in the attack, and 1x fatality was reported.
AC: At the moment, the circumstances of this attack are unclear. Some reporting suggests the ramming attack was intentional, other reports state that it was the result of a driver attempting to flee a police checkpoint because he was unlicensed, which resulted in the crash into a crowd of pedestrians. In either case, deliberate action was undertaken by the driver.
Netherlands: This morning a mass stabbing was reported in Amsterdam. 5x victims were stabbed by an assailant in Dam Square, with the attacker being detained at the scene. So far no details on the attacker have been released by authorities.
-HomeFront-
Washington D.C. - Following the Signal group chat scandal, overnight new developments have come to light. Using the data from the group chat as a jumping off point, various old email accounts, friends lists on various accounts, and random other data points have been linked to several of government officials. The media group that originated this digital snooping also claims that passwords were also found on various websites, likely resulting from various data breaches over the years.
North Carolina: Wildfire season is underway, bringing more risks than normal in some areas. For instance, in western North Carolina, the downed trees from Hurricane Helene have resulted in challenges managing wildfires. Similar situations and concerns have been reported in Tennessee and South Carolina.
-----END TEARLINE-----
Analyst Comments: Even though federal resources have arrived to work cleanup operations in western North Carolina (all of which is greatly appreciated by locals), much of it has been unfortunately too little, too late. All locals know that state leadership has been intentionally dragging feet on their Helene response to the point of being criminally negligent, even though local responders have done and continue to do great work at the local level. Regarding the fire season, responders are doing the best they can but many fires have been burning for almost a week and are still at zero-percent containment.
As one disaster often leads to another, the twist of the knife in this case turns out to be an increased wildfire risk. Downed trees provide fuel, change wind patterns, and provide barriers to vehicle traffic....both for firefighting resources and for those trying to evacuate. In short, firefighting will be a lot harder this year in the areas impacted by Hurricane Helene, so heightened situational awareness would be a great idea this fire season. If an evacuation is called for, evacuating earlier than you might think will be helpful, especially in areas that firefighting resources might have a hard time accessing. Just because a small passenger vehicle will squeeze through hurricane damaged roads doesn't mean that a firefighting rig can too.
Regarding the new developments in Washington, it would seem that various journalists simply conducted a bunch of free online background checks on various people in the original group chat, and since data privacy is a nightmare these days, a lot of links could be made using very little initial data. This isn't really a groundbreaking or scandalous development, it's more akin to just bad data protection practices.
We all have an old email address that we don't use anymore, or an account at a random website that we needed once and never used again, or the infamous data sucked up every single moment of an online existence. It turns out that government officials are people too, and if people are looking, a digital trail of breadcrumbs can easily be found.
In the age of data privacy being very hard to achieve, the various digital breadcrumbs left by those in government is a point of targeting by malign actors. Of course, this problem has existed for a long time and is irrespective of political party. As such a bit of survivability bias is probably in play here...anyone other than Trump's administration gets a free pass on their lax data security, but Trump's team gets examined with a fine-toothed comb. Now that journalists have found a profitable way to target various Trump officials, they will probably continue to dogpile on issues that are really inherent to government at large (and thus not really specific to something Trump or his people have done).
Nevertheless, this does highlight some inefficiencies in the day-to-day operations surrounding various government officials. For example, it has been known for many years that almost all military generals and admirals one-star and above, have a personal assistant solely dedicated to finding negative stories about that general, and shaping the general's image online (known as the Army Protective Services Battalion (APSB)). If a journalist can hop on a "free background check" website and find this data, one might have thought that the NSA would have completed a Personally Identifiable Information (PII) vulnerability assessment for senior government officials. An official getting blackmailed because of an embarrassing email account that they created when they were 12 years old is generally counter productive to the management of a nationstate. Consequently, as this scandal drags on, this might be a point of improvement in the long run.
Analyst: S2A1
Research: publish.obsidian.md/s2underground
//END REPORT//
#news #Berlin #Amsterdam #Wildfire #Helene
#Feminism #Girlboss 
//The Wire//2300Z March 26, 2025//
//ROUTINE//
//BLUF: STRATEGIC AMERICAN BOMBERS STAGE AT DIEGO GARCIA. FALLOUT FROM GROUP CHAT SCANDAL CONTINUES.//
-----BEGIN TEARLINE-----
-International Events-
Indian Ocean: Aviation watchers have noted a significant buildup of military aircraft at Diego Garcia. Several B2 bombers have forward deployed to the infamous island, along with almost a dozen KC-135R Stratotankers and other transport aircraft.
AC: This morning, a Notice-to-Airmen (NOTAM) was issued for Diego Garcia announcing ramp parking spot closures for the runway, indicating preparations to stage large numbers of military aircraft. This NOTAM is active until May 1, 2025.
Lithuania: Four American service members were found deceased after a training accident this morning. Initial reporting indicates that an M88 recovery vehicle drove/overturned into a lake during a routine training exercise. The soldiers were assigned to 1st Brigade, 3ID.
-HomeFront-
Washington D.C. - Fallout from the Atlantic scandal continues in a variety of means. Various liberal politicians have called for various resignations due to this scandal, while conservatives have stated that no resignations will occur. As the initial release of screenshots did not achieve the desired effect, The Atlantic released more screenshots of group chat messages.
AC: This morning, the activist group American Oversight filed a lawsuit against SECDEF Hegseth for the leak, and the judge assigned to this case has been announced as D.C. District Court Judge James Boasberg, the same judge who is currently at the center of hot controversy for out-of-jurisdiction rulings.
-----END TEARLINE-----
Analyst Comments: The events at Diego Garcia are a major indication and warning of an impending large-scale military conflict. Since these aircraft were not entirely covert in their movements, various intelligence services around the world know that this logistical staging is underway. What it's for, is anyone's guess. This could be for an escalation of the conflict in Yemen, or it could be staging for a large scale war with Iran. The use of Diego Garcia as a staging zone implies that the traditional staging sites (Bahrain, Qatar, Kuwait, etc) probably do not want to be diplomatically involved in what is about to take place. The remote location of Diego Garcia (which is also not located in an Islamic nation) provides the added benefit of being out of range of most of Iran's weapons, and thus a vastly more secure site for the staging of strategic bombers. In short, if the United States were to seek a war with Iran, this is exactly the type of forward-deployment that would take place.
Of course, despite the very clear and obvious military staging, a single phone call can result in all of these aircraft heading home without firing a shot. From the voyage of the Great White Fleet, to flying B-52's low and slow over various countries over the years, American history is full of examples of American power projection via the movement of very big weapons.
However, using the information we have at the moment, the forward-deployment of national-level strategic assets indicates staging for a military campaign.
Regarding the group chat scandal, now that we have a closer look at more screenshots provided by The Atlantic, a lot more information of questionable classification level has come to light. Even though the newly-posted screenshots are not the smoking-gun The Atlantic claims, if this information was not a deliberate plant, it would indeed have been a serious violation of Operational Security (OPSEC). Really the only communication that was a serious breach of OPSEC came from the SECDEF, who announced that the targeting missions against the Houthis in Yemen were a "GO", and detailed the number of strikes and estimated Time-on-Target. However, when determining the classification level of information, the source itself would dictate this. For instance, the SECDEF did not create this information himself, this was paraphrased from a slide deck or a briefing he was sent through proper channels. If an investigation were to be conducted, the classification of the information in that document would be the true source for whether or not Hegseth's comments were classified in any way. But therein lies the problem, he very likely paraphrased, and didn't copy directly from a classified intelligence product. It is this paraphrasing that gets into muddy waters really quickly, and highlights long-standing issues in government.
When it comes to the higher levels of government organization, OPSEC is a nightmare under the best of conditions; regardless of party affiliation, anytime a politician gets their hands on any classified information one can rest assured that it will be held under the most lax security conditions possible. This does not excuse the behavior, but it does explain it. Similar story with the use of the Signal app in the first place; historically, this has very obviously not been an authorized form of communication. However it's been used for many years unofficially by staffers all over Washington (along with WhatsApp, before the security concerns prompted the general shift to Signal a few years ago). This morning DNI Tulsi Gabbard somewhat perplexingly confirmed that the Signal app is pre-installed on government-issued communications devices. If this is true, this would suggest a very new approach to the handling of official communications. Smartphones with access to classified information systems have existed for many years (such as the DMCC-S phones), but are highly compartmentalized and controlled, and do not usually have third party apps or app stores installed. However, if the DNI's testimony is to be believed, and the use of Signal itself was somehow authorized, the scandal then shifts to how an unauthorized person obtained access (since this clearly confirms that these communications were not compartmentalized in accordance with long-standing regulations).
More generally, the use of Signal is mostly a byproduct of fast-paced comms being needed between high-ranking officials that are also convenient to use, even if they aren't as secure or official. This is also complicated by the fact that almost all politicians do not understand the concept of what's called Aggregation in the world of intelligence work. In short, a single detail can be unclassified...but if you get enough unclassified information together in the same report, this can add up to being a classified report. As Hegseth stated in response to the leak "No names. No targets. No locations. No units. No routes. No sources. No methods." were stated in the group chat. However, all of this data could have been easily discerned from other sources, in conjunction with what was provided. Notably, Mr. Hegseth left out the Time-on-Target information, which is almost certainly classified SECRET or higher, based on CENTCOM's own Classification Guide.
If this group chat is indeed genuine, ignorance of the concept of Aggregation was probably the best explanation for what happened. Various officials "sanitizing" their remarks thinking that they are unclassified, but when put into the context of the larger conversation, their remarks should have been made by other means. This happens all the time, and is why the age-old spy tradecraft tactic of nationstates monitoring American Congressional hearings is still probably a wealth of information...all it takes is a Congressman getting a bit carried away and suddenly sensitive information is being alluded to, implied, or in some cases, stated openly. This has been the culture of Washington for a long time, but this is something that is really only accepted at the higher levels of organization. Once again, it doesn't make it right, but this is the reality of the way that classified information is handled by politicians; if any junior soldier had posted attack timeline details in a group chat, they would have been punished severely for this OPSEC breach, and their future career destroyed. If it were a low-ranking service member, the question of "is this classified?" would default to an answer of "yes, at bare minimum SECRET". When a politician is involved however, the answer defaults to a slap-on-the-wrist, at most. This is simply the reality of how things work.
The official White House response has also shifted to denial, with the Press Secretary calling the event a "hoax". However, this statement is in opposition to the statements by other officials, such as the Vice President and SECDEF themselves. Both have not denied that the group chat was real, and both have spoken about the incident in terms of accepting that the chat is real, but also denying that anything damning was said (which is very obviously not true if a targeting timeline was posted).
One possibility that must be considered is that these messages (or even the entire group chat itself) could have been run primarily by low-level staffers instead of the public figures themselves. In other words, it might not have actually been the SECDEF himself communicating the probably classified information, but a staffer instead. Historically speaking, it wouldn't be the first time that a staffer got their boss in trouble. However in this specific case, this is a hard argument to make. It's hard to believe that a low-level staffer would be posting targeting timetables in this manner. The sheepish responses by those implicated in the scandal also indicates that they were the ones behind the messages, especially since many words have been spoken on this scandal...none of which have been a flat-out denial of the identities of those involved.
At this point, what the exact truth is will be impossible to verify with a high level of confidence. The whole affair could be fabricated from the ground up by the Atlantic, though this is unlikely based on the statements by those who were in the group chat. The group chat is almost certainly real, and the messages were probably sent by those as alleged. If the more controversial information was indeed taken from a classified briefing product, paraphrased, and posted in the group chat, this paraphrasing does not change the original classification of the intelligence product.
The real question that remains is whether or not this was a deliberate deception attempt, or a deliberate leak of some kind. Whatever the truth is, it's unlikely to matter much in the long run, as this whole scandal has already turned into a political issue rather than the objective investigation and learning opportunity it should be. Also, the Secretary of Defense is an Original Classification Authority (OCA) per long standing mandate, so even if Hegseth (and others) did disclose classified information, he has the authority to retroactively declassify that information himself, at will.
Analyst: S2A1
Research: publish.obsidian.md/s2underground
//END REPORT//
nostr:naddr1qq7yummnw3ez63rpw3sj6stkv95kcctzd9kxjare942xsefd2d68yetfwdskuepdg4nxvetrwsk4qun0w3hkxmmv95ex5utsv36qygqyey2a4mlw8qchlfe5g39vacus4qnflevppv3yre0xm56rm7lveypsgqqqw4rs38aa3w