Some interesting possibilities for new types of delegate keys 👀

CC nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
Some interesting possibilities for new types of delegate keys 👀

CC nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
Not sure why the image is broken here's a copy
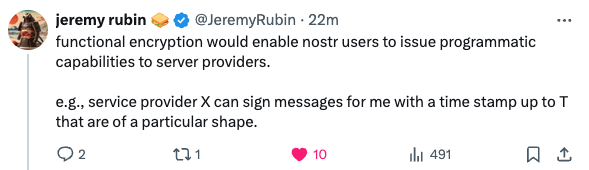
This is what nsec bunker already does.
But this would be totally trustless. No need to have a custodian hold your key or run your own bunker
From the “functional encryption” description it’s unclear what he means.
From my understanding, it's sort of like homomorphic encryption where you can create a function key based on a particular private key, which allows a certain function to operate on the encrypted data as if it was not encrypted. Thus, allowing for a note signing without revealing the nsec.
Ahhh. This looks fun. 🤓
I'm seeing a bunch of primal images this morning that aren't loading in Amethyst.
I think primal's image server may be down cc nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq36amnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdshszymhwden5te0wp6hyurvv4cxzeewv4ej7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uq32amnwvaz7tmjv4kxz7fwdehhxarj9e3xwtcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcqyrtp7w79k045gq80mtnpdxjuzl9t7vjxk52rv80f888y5xsd5mh55wp9vxs nostr:nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzdmhxue69uhhqatjwpkx2urpvuhx2ue0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9uq3wamnwvaz7tmjv4kxz7fwwpexjmtpdshxuet59uq32amnwvaz7tmjv4kxz7fwdehhxarj9e3xwtcppemhxue69uhkummn9ekx7mp0qyf8wumn8ghj7mmwvd5xz6tw9ec82c30qqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpsd488pl
This just sounds like NIP-26. It still requires the client to validated the delegation and remember who the real author was
This would allow the delegate to create a real signature as if they had the actual nsec based on some constraints. So somthing like x key can generate valid signatures for kind 1's with created_at < Y. And that would create valid signatures, clients would just verify them as any other note and you would have no idea that it was created via one of these delegate keys.